The malware is delivered through a fake Google Chrome update that is shown while using the web browser. Brokewell is under active development and features a mix of extensive device takeover and remote control capabilities.
Researchers have sinkholed a command and control server for a variant of the PlugX malware and observed in six months more than 2.5 million connections from unique IP addresses.
Apr 25, 2024NewsroomVulnerability / Zero-Day A new malware campaign leveraged two zero-day flaws in Cisco networking gear to deliver custom malware and facilitate covert data collection on target environments. Cisco Talos, which dubbed the activity ArcaneDoor, attributing it as the handiwork of a previously undocumented sophisticated state-sponsored actor it tracks under the name UAT4356 (aka […]
Apr 24, 2024NewsroomMalware / Data Security A new ongoing malware campaign has been observed distributing three different stealers, such as CryptBot, LummaC2, and Rhadamanthys hosted on Content Delivery Network (CDN) cache domains since at least February 2024. Cisco Talos has attributed the activity with moderate confidence to a threat actor tracked as CoralRaider, a suspected […]
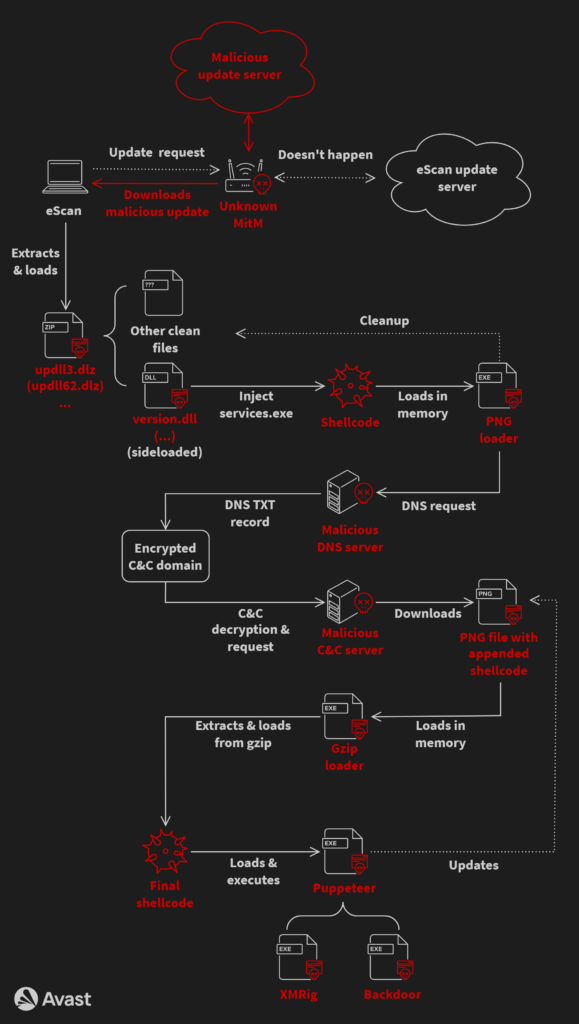
Key Points Avast discovered and analyzed a malware campaign hijacking an eScan antivirus update mechanism to distribute backdoors and coinminers Avast disclosed the vulnerability to both eScan antivirus and India CERT. On 2023-07-31, eScan confirmed that the issue was fixed and successfully resolved The campaign was orchestrated by a threat actor with possible ties to […]
The malware does not try to hide its presence in the system from antivirus programs and has not gained much popularity in the underground yet, indicating that it is a new player in the market.
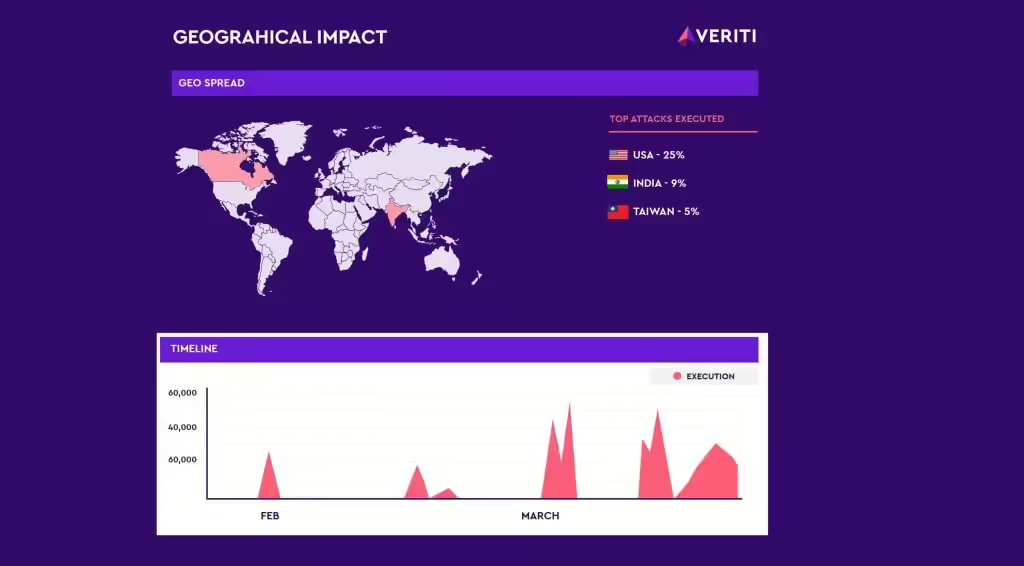
Veriti Research has discovered a surge in attacks from operators of the Androxgh0st malware family, uncovering over 600 servers compromised primarily in the U.S., India and Taiwan. According to Veriti’s blog post, the adversary behind Androxgh0st had their C2 server exposed, which could allow for a counterstrike by revealing the impacted targets. The researchers then […]
Last August we documented a malware campaign that was injecting malicious JavaScript code into compromised WordPress sites to redirect site visitors to VexTrio domains. The most interesting thing about that malware was how it used dynamic DNS TXT records of the tracker-cloud[.]com domain to obtain redirect URLs. Typical notification scam destination for the redirects We’ve […]
A new info-stealing malware linked to Redline poses as a game cheat called ‘Cheat Lab,’ promising downloaders a free copy if they convince their friends to install it too.