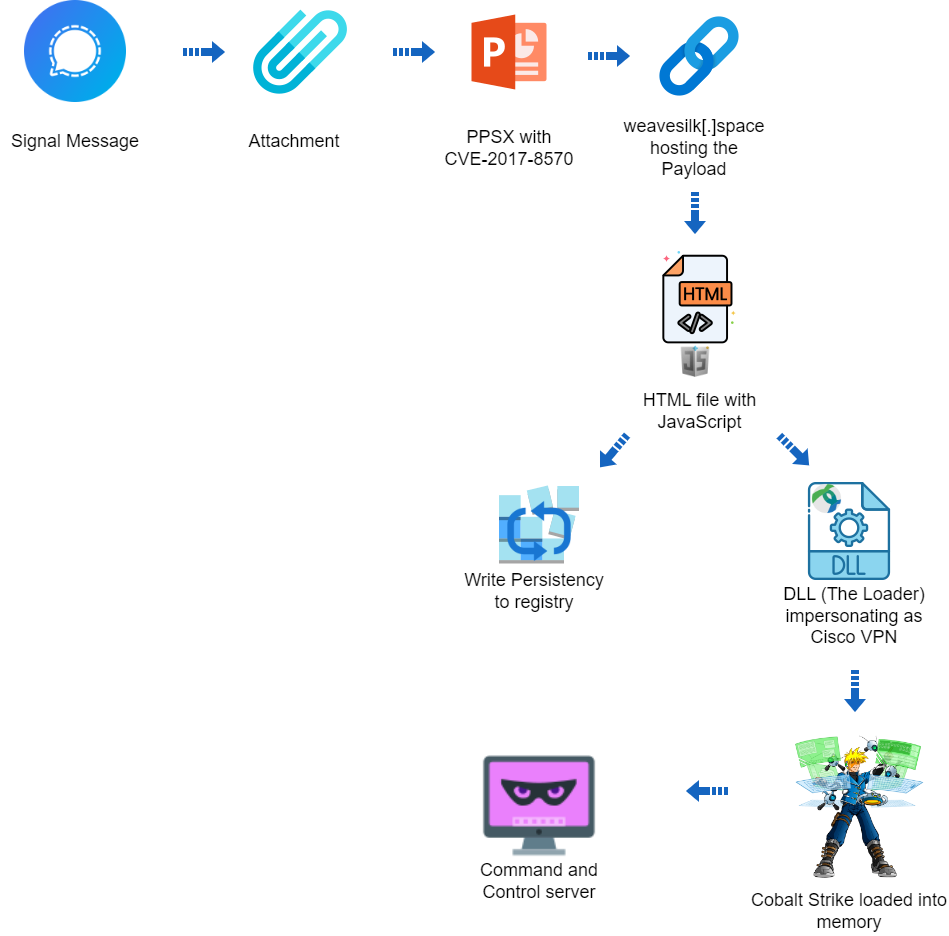
Executive Summary The Deep Instinct Threat Lab discovered a suspected targeted operation against Ukraine The operation is using CVE-2017-8570 as the initial vector The operation could not be attributed to any known threat actor The operation used a custom loader for Cobalt Strike Beacon Deep Instinct is detecting all stages of the attack Campaign Overview […]
Apr 25, 2024NewsroomMalware / Cyber Threat The North Korea-linked threat actor known as Lazarus Group employed its time-tested fabricated job lures to deliver a new remote access trojan called Kaolin RAT. The malware could, “aside from standard RAT functionality, change the last write timestamp of a selected file and load any received DLL binary from […]
How It Works The sequence begins with threat actors creating a fake site on a web hosting service, which remains undetected by the hosting service itself. When a user searches for relevant information and clicks on a link from the search results, they unknowingly access the malicious site. Interestingly, if the user directly enters the […]
A GitHub flaw, or possibly a design decision, is being abused by threat actors to distribute malware using URLs associated with Microsoft repositories, making the files appear trustworthy.
Apr 23, 2024NewsroomNational Security Agency / Threat Intelligence The Russia-linked nation-state threat actor tracked as APT28 weaponized a security flaw in the Microsoft Windows Print Spooler component to deliver a previously unknown custom malware called GooseEgg. The post-compromise tool, which is said to have been used since at least June 2020 and possibly as early […]
Apr 22, 2024NewsroomNetwork Security / Endpoint Security The threat actor known as ToddyCat has been observed using a wide range of tools to retain access to compromised environments and steal valuable data. Russian cybersecurity firm Kaspersky characterized the adversary as relying on various programs to harvest data on an “industrial scale” from primarily governmental organizations, […]
Threat actors created a website to impersonate UsenetClub, a subscription service for “uncensored” access to images and videos downloaded from Usenet. They claimed to provide free access to the site after the installation of a “CryptVPN” software.
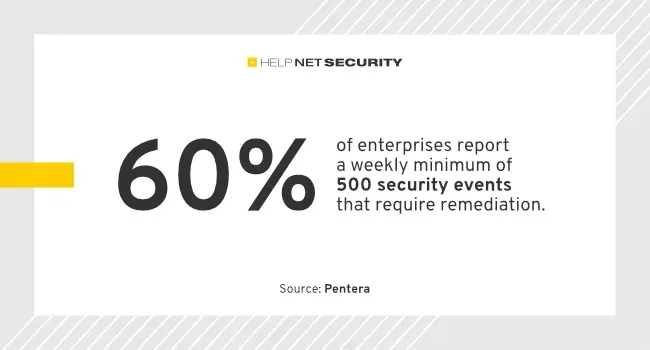
Threat actors are continuing to successfully breach across the entire attack surface and the stakes are only getting higher: 93% of enterprises who admitted a breach reported unplanned downtime, data exposure, or financial loss as a result, according to Pentera. Pentera surveyed 450 CISOs, CIOs, and IT security leaders at enterprise companies with more than […]
Between crossovers – Do threat actors play dirty or desperate? In our dataset of over 11,000 victim organizations that have experienced a Cyber Extortion / Ransomware attack, we noticed that some victims re-occur. Consequently, the question arises why we observe a re-victimization and whether or not this is an actual second attack, an affiliate crossover […]