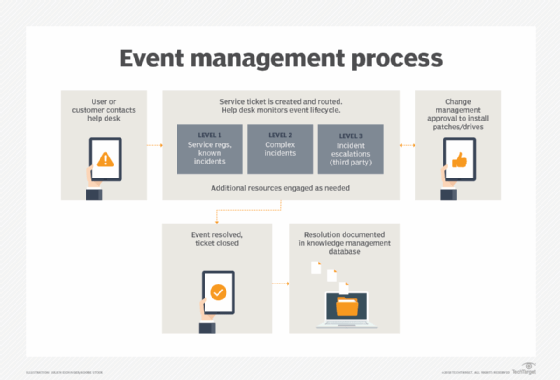
What are data center services? Data center services provide all the supporting components necessary to the proper operation of a data center. They include all activities associated with data center implementation, maintenance and operation and involve hardware, software, processes and personnel. Data center services are responsible for providing IT organizations with data backup and recovery, […]
What is IOPS (input/output operations per second)? IOPS (input/output operations per second) is the standard unit of measurement for the maximum number of reads/writes to noncontiguous storage locations. IOPS is pronounced EYE-OPS. Simply put, IOPS is a measure of a storage device’s read/write speed. It refers to the number of input/output (I/O) operations the device […]
Mar 28, 2024NewsroomTechnology / Data Privacy In June 2017, a study of more than 3,000 Massachusetts Institute of Technology (MIT) students published by the National Bureau for Economic Research (NBER) found that 98% of them were willing to give away their friends’ email addresses in exchange for free pizza. “Whereas people say they care about […]
Mar 27, 2024NewsroomCyber Espionage / Data Breach Indian government entities and energy companies have been targeted by unknown threat actors with an aim to deliver a modified version of an open-source information stealer malware called HackBrowserData and exfiltrate sensitive information in some cases by using Slack as command-and-control (C2). “The information stealer was delivered via […]
‘Digital Entropy is a new six-track EP on Tresor, but it’s far from ‘just another new release’. For a starter, the act behind it, Datashader, is anonymous and faceless. Yes, they’ve supplied us with a press shot (above), but ithe rather shifty looking character in it is an AI-generated image rather than a real person. […]
Mar 27, 2024NewsroomThreat Intelligence / Network Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a security flaw impacting Microsoft Sharepoint Server to its Known Exploited Vulnerabilities (KEV) catalog based on evidence of active exploitation in the wild. The vulnerability, tracked as CVE-2023-24955 (CVSS score: 7.2), is a critical remote code execution flaw […]
Mar 27, 2024NewsroomVulnerability / API Security A now-patched security flaw in the Microsoft Edge web browser could have been abused to install arbitrary extensions on users’ systems and carry out malicious actions. “This flaw could have allowed an attacker to exploit a private API, initially intended for marketing purposes, to covertly install additional browser extensions […]
CREST’s Nick Benson examines whether financial regulators are doing enough to set mandatory minimum standards for complex, unpredictable and critical intelligence-led cyber attacks
Mar 27, 2024The Hacker NewsData Protection / Browser Security As SaaS applications dominate the business landscape, organizations need optimized network speed and robust security measures. Many of them have been turning to SASE, a product category that offers cloud-based network protection while enhancing network infrastructure performance. However, a new report: “Better Together: SASE and Enterprise […]