Apr 20, 2024NewsroomVulnerability / Endpoint Security Users of the CrushFTP enterprise file transfer software are being urged to update to the latest version following the discovery of a security flaw that has come under targeted exploitation in the wild. “CrushFTP v11 versions below 11.1 have a vulnerability where users can escape their VFS and download […]
In January 2024, FortiGuard Labs collected a PDF file written in Portuguese that distributes a multi-functional malware known as Byakugan. While investigating this campaign, a report about it was published.
First cc.bat for reconnaissance Once the scheduled task is triggered, a previously deployed batch file, %System%cc.bat, is executed in the remote machine. Based on our telemetry, this batch file launches commands to gather system information. Among the commands executed are: powershell.exe -command “Get-NetAdapter |select InterfaceGuid” arp -a ipconfig /all fsutil fsinfo drives query user net […]
Cookie List A cookie is a small piece of data (text file) that a website – when visited by a user – asks your browser to store on your device in order to remember information about you, such as your language preference or login information. Those cookies are set by us and called first-party cookies. […]
Defense evasion by exploiting CVE-2023-36025 Once the malicious .url file exploiting CVE-2023-36025 is executed, it connects to an attacker-controlled server to download and execute a control panel item (.cpl) file. Microsoft Windows Defender SmartScreen should warn users with a security prompt before executing the .url file from an untrusted source. However, the attackers craft a […]
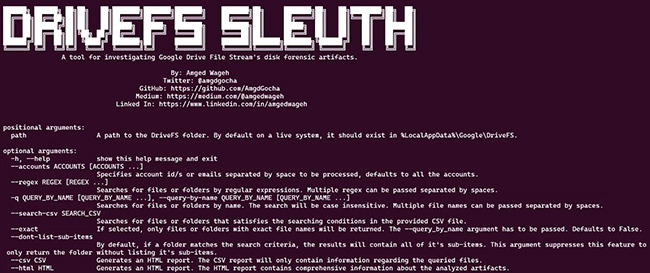
DriveFS Sleuth automates the investigation of Google Drive File Stream disk artifacts. The tool can parse the disk artifacts and build a filesystem tree-like structure enumerating the synchronized files along with their respective properties. “While engaged in a threat-hunting activity for a client to detect the misuse of file-syncing applications within their network, I identified […]
What is a configuration management database (CMDB)? A configuration management database (CMDB) is a file — usually in the form of a standardized database — that contains all relevant information about the hardware and software components used in an organization’s IT services and the relationships among those components. A CMDB stores information that provides an […]
The breach occurred after a file transfer program used by the company was hacked. Welltok works with health service providers, maintaining online wellness programs and holding databases with patient data.
In the latest disclosures related to a Russian ransomware gang’s exploitation of the popular MOVEit file transfer service, a federal government agency revealed that more than 330,000 Medicare recipients were affected in a leak of sensitive data. The U.S. Center for Medicare & Medicaid Services (CMS) provides health coverage to more than 160 million people […]
- 1
- 2