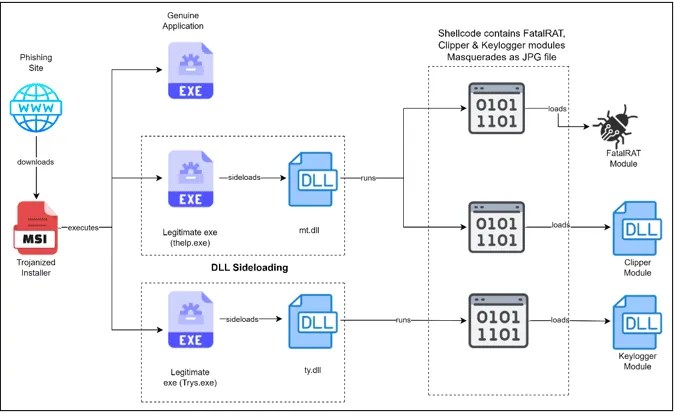
Researchers have discovered a sophisticated phishing campaign meticulously crafted to target cryptocurrency users. This elaborate scheme, equipped with the notorious FatalRAT along with supplementary malware like Clipper and Keylogger, was orchestrated by threat actors utilizing DLL side-loading techniques. Source: Infection Chain (Cyble) FatalRAT, renowned as a Remote Access Trojan, grants attackers control over victim systems, […]
AuthLogParser is an open-source tool tailored for digital forensics and incident response, specifically crafted to analyze Linux authentication logs (auth.log). The tool examines the auth.log file, extracting crucial details like SSH logins, user creations, event names, IP addresses, among others. It produces a concise summary that offers a clear overview of the activities documented in […]
Executive summary In recent developments, a sophisticated malware stealer strain crafted in the Go programming language has been discovered by AT&T Alien Labs, posing a severe threat to both Windows and macOS operating systems. As of the time of publishing of this article, traditional antivirus solutions have low or even non-existent detection rates, making it […]