FatalRAT Targets Cryptocurrency Users With DLL Side-loading Techniques
Researchers have discovered a sophisticated phishing campaign meticulously crafted to target cryptocurrency users. This elaborate scheme, equipped with the notorious FatalRAT along with supplementary malware like Clipper and Keylogger, was orchestrated by threat actors utilizing DLL side-loading techniques.
FatalRAT, renowned as a Remote Access Trojan, grants attackers control over victim systems, facilitating the theft of sensitive information.
This campaign’s strategic inclusion of a clipper module alongside FatalRAT hints at a targeted approach towards cryptocurrency users, amplifying data interception capabilities with the addition of a keylogger module.
The FatalRAT Phishing Campaign
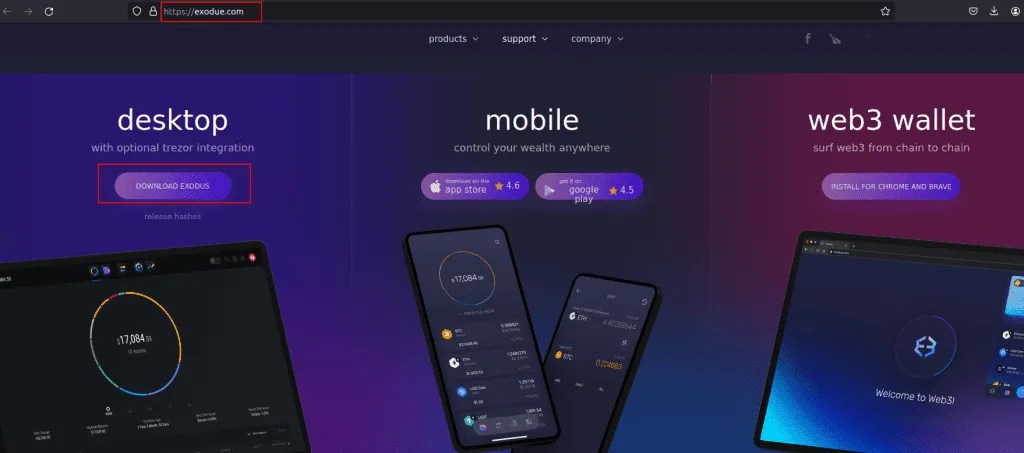
The FatalRAT phishing campaign primarily targeted Chinese-speaking individuals or organizations, evident from the use of Chinese-language installers. The phishing endeavor bore a striking resemblance to the Exodus cryptocurrency wallet interface, designed to lure unsuspecting users into divulging confidential information.
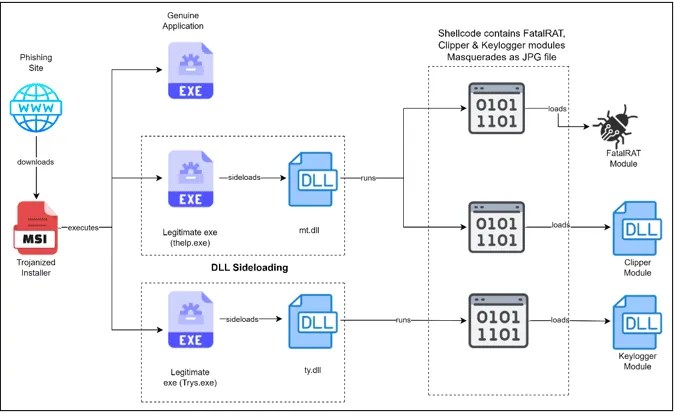
According to Cyble Research and Intelligence Labs (CRIL), once users fell prey to the deceptive website and downloaded the counterfeit Exodus installers, they unwittingly installed FatalRAT, Clipper, and Keylogger. Employing DLL side-loading tactics, the attackers evaded detection, seamlessly executing their malicious payloads.
Upon installation, the Trojanized Exodus installer granted attackers unauthorized access, enabling them to clandestinely pilfer information, manipulate data, and intercept transactions. This operation, augmented by the diversionary tactic of foreground installation, ensured users remained unaware of the malicious activities unfolding in the background.
Technical Analysis of the FatalRAT Campaign
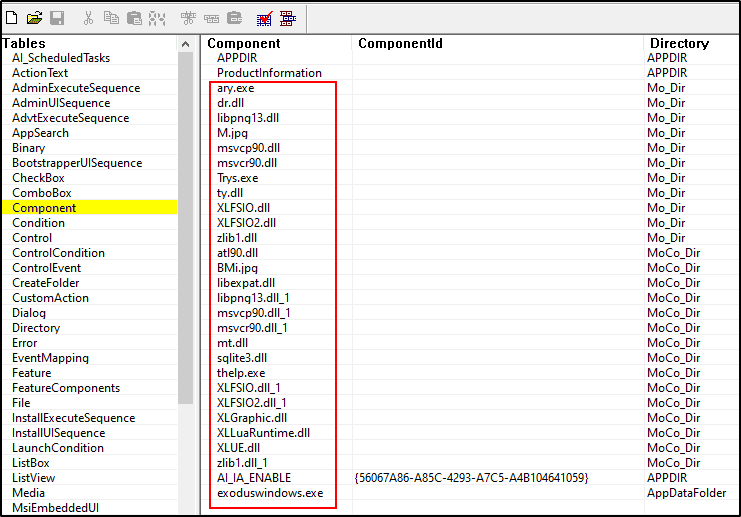
Technical analysis revealed a multi-staged attack unfolding with precision, dropping files into designated directories and utilizing DLL side-loading to execute payloads discreetly. FatalRAT, equipped with capabilities ranging from keystroke logging to data theft, closely resembled previous variants identified by security experts.
The clipper module, embedded within the phishing scheme, monitored clipboard activity, intercepting cryptocurrency addresses and substituting them with malicious wallet addresses controlled by the Threat Actors. Meanwhile, the keylogger module operated independently, recording keystrokes and system events for later exfiltration.
Attribution suggests the involvement of a group behind previous campaigns, evidenced by similarities in the infection chain, file names, and targeting strategies. The campaign’s focus on Chinese individuals and the pattern of C&C servers further bolsters this speculation.
Moreover, the surge in cryptocurrency popularity has made users prime targets for cybercriminals. With the fusion of FatalRAT and dedicated clipper modules, attackers can exploit vulnerabilities in cryptocurrency transactions, making it a gigantic threat for crypto users.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.

