Cybersecurity
Category Added in a WPeMatico Campaign
The flaw, CVE-2023-32315, allows attackers to bypass authentication and create new admin accounts, enabling them to install malicious Java plugins and execute arbitrary code on compromised servers.
The government of Kuwait is in the process of recovering from a ransomware attack that affected its Ministry of Finance. The ransomware attack began on September 18 and government officials immediately tried to separate and shut off affected systems. Officials sought to preempt concerns that workers would not be paid, reiterating that payment and payroll […]
Stratascale, an SHI company, announced the acquisition of Vector0, an Attack Surface Management (ASM) provider. Through the acquisition, Stratascale professionals and their customers gain visibility of attack vectors and points of vulnerability, enhancing Stratascale’s ability to deliver proactive cybersecurity services. “Vector0 enables us to offer a comprehensive and proactive approach to Attack Surface Validation (ASV), […]
ShadowSyndicate is believed to be an initial access broker (IAB) or an affiliate working with multiple ransomware operations, including Quantum, Nokoyawa, BlackCat/ALPHV, Clop, Royal, Cactus, and Play, based on evidence found by researchers.
The Royal ransomware group intruded Dallas’ systems and surveilled and exfiltrated data for a month before it initiated a ransomware attack that threw city operations into disarray last spring, the city said Wednesday in a post-attack report. The prolific ransomware group, which was linked to a spree of attacks in the Dallas metro area, established […]
Researchers at SentinelOne have noticed a potential cyberespionage group, whose origins are unclear (as of now), and employed modular backdoors and covert techniques to target telecommunication firms in the Middle East, Western Europe, and South Asia. This group, labeled Sandman APT, utilizes a new backdoor named LuaJIT, which is a just-in-time compiler for the Lua […]
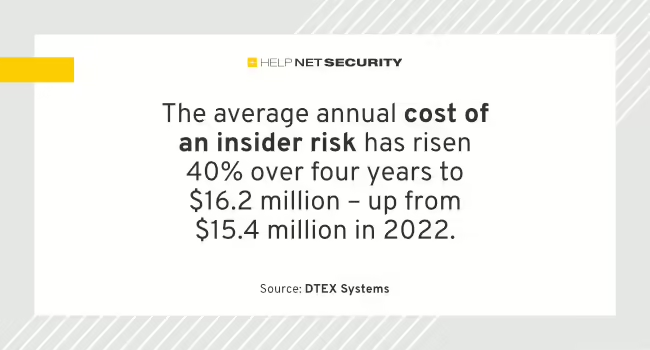
The cost of an insider risk is the highest it’s ever been, as organizations spend more time than ever trying to contain insider incidents, according to DTEX Systems. The average annual cost of an insider risk has increased to $16.2 million – a 40% increase over four years. Meanwhile, the average number of days to […]
SOC 2, ISO, HIPAA, Cyber Essentials – all the security frameworks and certifications today are an acronym soup that can make even a compliance expert’s head spin. If you’re embarking on your compliance journey, read on to discover the differences between standards, which is best for your business, and how vulnerability management can aid compliance. […]
Sep 26, 2023THNMobile Security / Malware An updated version of an Android banking trojan called Xenomorph has set its sights on more than 35 financial institutions in the U.S. The campaign, according to Dutch security firm ThreatFabric, leverages phishing web pages that are designed to entice victims into installing malicious Android apps that target a […]