Cybersecurity
Category Added in a WPeMatico Campaign
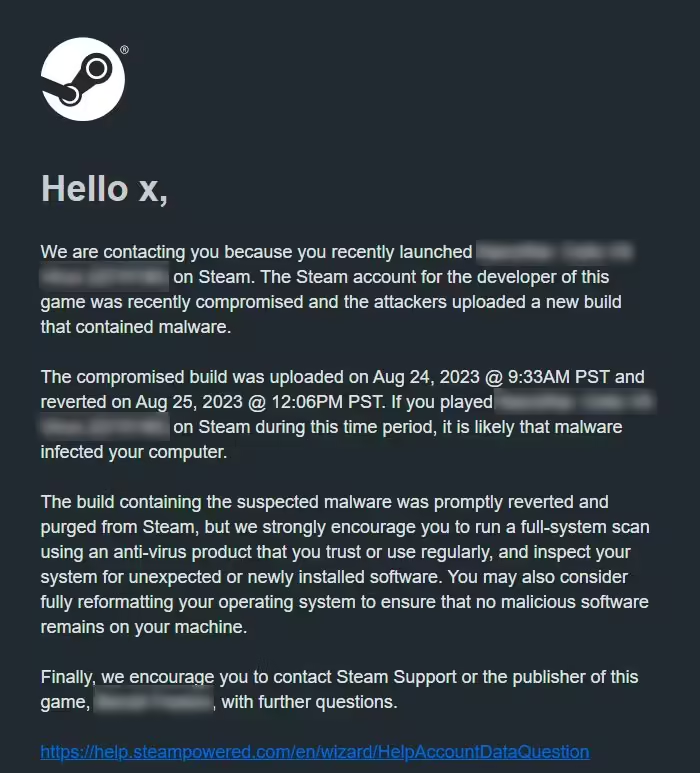
After hackers distribute malware in-game updates, Steam adds SMS-based security check for developers
Valve, the company behind the Steam video game platform, has announced a new security feature after multiple reports of game updates being poisoned with malware. Last month, some game players reported receiving messages from Steam’s support team telling them that updated games they played via the platform had contained malware. Valve claimed that fewer than […]
Beware Lumma Stealer Distributed via Discord CDN Content has been added to your Folio Go to Folio (0) close Cyber Threats This blog discusses how threat actors abuse Discord’s content delivery network (CDN) to host and spread Lumma Stealer, and talks about added capabilities to the information stealing malware. By: Carl Malipot October 16, 2023 […]
Oct 16, 2023NewsroomZero Day / Vulnerability Encrypted messaging app Signal has pushed back against “viral reports” of an alleged zero-day flaw in its software, stating it found no evidence to support the claim. “After responsible investigation *we have no evidence that suggests this vulnerability is real* nor has any additional info been shared via our […]
Oct 16, 2023NewsroomBlockchain / Malware Threat actors have been observed serving malicious code by utilizing Binance’s Smart Chain (BSC) contracts in what has been described as the “next level of bulletproof hosting.” The campaign, detected two months ago, has been codenamed EtherHiding by Guardio Labs. The novel twist marks the latest iteration in an ongoing […]
By: Robert O’Callaghan A method of communication that remains important in our modern world is that of the voice message. The PDC recently observed a phishing campaign where threat actors included an access key in the body as a way to entice the user to access the voice message that had been left for them […]
Oct 14, 2023NewsroomAuthentication / Endpoint Security Microsoft has announced that it plans to eliminate NT LAN Manager (NTLM) in Windows 11 in the future, as it pivots to alternative methods for authentication and bolster security. “The focus is on strengthening the Kerberos authentication protocol, which has been the default since 2000, and reducing reliance on […]
The outages have affected various operations, such as new orders, payments, and access to support systems, leading to customer frustration and the posting of signs by employees.
Guardio · Follow 9 min read · 1 day ago — By Nati Tal, Oleg Zaytsev (Guardio Labs) “EtherHiding” presents a novel twist on serving malicious code by utilizing Binance’s Smart Chain contracts to host parts of a malicious code chain in what is the next level of Bullet-Proof Hosting. Over the last two months, […]
Networking equipment manufacturer Juniper Networks on Thursday announced patches for more than 30 vulnerabilities in Junos OS and Junos OS Evolved, including nine high-severity flaws. The most severe of these issues is an incorrect default permissions bug that allows an unauthenticated attacker with local access to a vulnerable device to create a backdoor with root […]