Cybersecurity
Category Added in a WPeMatico Campaign
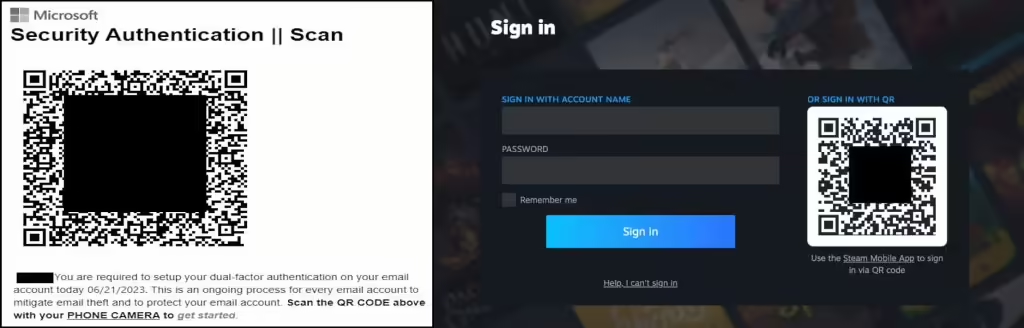
QRLJacking tricks you with fake QR codes to log into fake websites or apps, while Quishing uses QR codes to deceive you into visiting malicious sites or downloading malware. Quick Response Codes (aka QR Codes) have made life hassle-free for everyone as these versatile codes offer access to everything. However. according to SaaS-based cloud messaging […]
Oct 20, 2023NewsroomMalware / Cyber Attack Attacks leveraging the DarkGate commodity malware targeting entities in the U.K., the U.S., and India have been linked to Vietnamese actors associated with the use of the infamous Ducktail stealer. “The overlap of tools and campaigns is very likely due to the effects of a cybercrime marketplace,” WithSecure said […]
The U.S. Defense Department has received the findings of a months-long outsider examination about how to best create a new lead cyber policy chief. The Record first reported earlier this year that the Pentagon had tapped the RAND Corporation to study the creation of an assistant secretary of defense for cyber policy. The post was […]
The info-stealer market is expanding rapidly as researchers uncovered a new malware named ExelaStealer. The malware first appeared in August and includes a variety of data-stealing capabilities from stealing sensitive data, such as passwords, credit card details, cookies, and session data to key logs, from Windows systems. More in detail According to Fortiguard Labs, ExelaStealer […]
RagnarLocker, known for its double extortion tactic and refusal to negotiate ransom demands, has been a significant threat to critical infrastructure organizations, with 52 successful attacks reported.
Due to the rapid evolution of technology, the Internet of Things (IoT) is changing the way business is conducted around the world. This advancement and the power of the IoT have been nothing short of transformational in making data-driven decisions, accelerating efficiencies, and streamlining operations to meet the demands of a competitive global marketplace. IoT […]
Affected Platforms: WindowsImpacted Users: Windows usersImpact: The information collected can be used for future attacksSeverity Level: Medium In 2023, the InfoStealer market is a reasonably crowded affair. The likes of RedLine, Raccoon, and Vidar own a significant market share, with new entrants such as SaphireStealer appearing frequently. The latest entry, ExelaStealer has now taken the […]
This post is also available in: 日本語 (Japanese) Executive Summary BlackCat operators recently announced new updates to their tooling, including a utility called Munchkin that allows attackers to propagate the BlackCat payload to remote machines and shares on a victim organization network. For the past two years, the BlackCat ransomware operators have continued to evolve […]
Organizations trying to cope with securing their expanding attack surfaces eventually find themselves at a crossroads: they need to move beyond finding risks to effectively mitigating risk. Making that transition starts with a shift from using “risks found” as the KPI to “risks remediated” as the true measure of success. That change shifts security team […]