Cybersecurity
Category Added in a WPeMatico Campaign
A British startup called Harmonic Security has attracted $7 million in seed-stage investment to build technology to help secure generative AI deployments in the enterprise. Harmonic, based in London and San Francisco, said it is working on software to mitigate against the ‘wild west’ of unregulated AI apps harvesting company data at scale. The company […]
The International Criminal Court (ICC) said on Friday that the serious cybersecurity incident it detected in September was an act of espionage. In a statement on the Court’s website, it said the attack can be “interpreted as a serious attempt to undermine the Court’s mandate.” The statement did not suggest a perpetrator, but the Court […]
Europol on Friday announced the takedown of the infrastructure associated with Ragnar Locker ransomware, alongside the arrest of a “key target” in France. “In an action carried out between 16 and 20 October, searches were conducted in Czechia, Spain, and Latvia,” the agency said. “The main perpetrator, suspected of being a developer of the Ragnar […]
Oct 21, 2023NewsroomData Breach / Cyber Attack Identity services provider Okta on Friday disclosed a new security incident that allowed unidentified threat actors to leverage stolen credentials to access its support case management system. “The threat actor was able to view files uploaded by certain Okta customers as part of recent support cases,” David Bradbury, […]
Oct 21, 2023NewsroomZero-Day / Vulnerability Cisco has warned of a new zero-day flaw in IOS XE that has been actively exploited by an unknown threat actor to deploy a malicious Lua-based implant on susceptible devices. Tracked as CVE-2023-20273 (CVSS score: 7.2), the issue relates to a privilege escalation flaw in the web UI feature and […]
India’s Central Bureau of Investigation (CBI) conducted raids at 76 locations across the country as part of Operation Chakra-II, targeting cybercrime operations involved in tech support scams and cryptocurrency fraud.
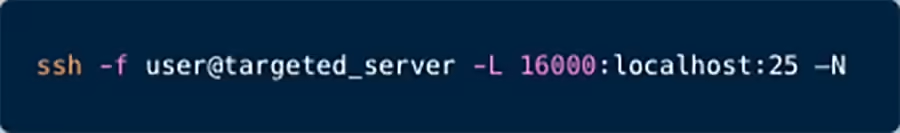
Aqua Nautilus researchers have shed brighter light on a long-standing threat to SSH in the context of the cloud. More specifically, the threat actor harnessed our SSH server to be a slave proxy and pass traffic through it. In this blog, we will explain this threat, demonstrate how attackers exploit SSH, what actions they take […]
WASHINGTON – The Cybersecurity and Infrastructure Security Agency (CISA), National Security Agency (NSA), Federal Bureau of Investigation (FBI) and Multi-State Information Sharing and Analysis Center (MS-ISAC) today published “Phishing Guidance, Stopping the Attack Cycle at Phase One” to help organizations reduce likelihood and impact of successful phishing attacks. It provides detailed insight into malicious actor […]
Security researchers located tens of thousands of exploited hosts linked to a critical zero-day vulnerability in the web user interface of Cisco IOS XE software. Censys researchers found almost 42,000 exploited devices with a backdoor installed, according to a Wednesday blog post. Cisco hasn’t yet released a patch or provided a timeline for when one […]