Cybersecurity
Category Added in a WPeMatico Campaign
The motive behind these cloned sites is likely to generate traffic for gambling operators, as they can serve third-party ads that publishers may be reluctant to carry on their own sites.
One of the vulnerabilities, known as “Reptar,” affects Intel CPUs and could lead to system instability or privilege escalation. The other vulnerability, CVE-2023-46835, could allow malicious code in a guest VM to compromise an AMD-based host.
Researchers have discovered 21 vulnerabilities in a popular brand of industrial router. On Dec. 7 at Black Hat Europe, analysts from Forescout will reveal the bugs — including one of 9.6 “Critical” severity on the CVSS scale, and nine “High” severity — affecting a brand of operational technology (OT)/Internet of Things (IoT) routers especially common […]
Scammers are exploiting the trust placed in reputable accounts by creating fake accounts with similar names and spreading fabricated security breach claims to deceive users into clicking on malicious links and revealing their wallet information.
Nov 16, 2023NewsroomVulnerability / Email Security A zero-day flaw in the Zimbra Collaboration email software was exploited by four different groups in real-world attacks to pilfer email data, user credentials, and authentication tokens. “Most of this activity occurred after the initial fix became public on GitHub,” Google Threat Analysis Group (TAG) said in a report […]
Security researchers with eSentire, a top global cybersecurity solutions provider, are warning that Russian-speaking affiliates of the ransomware gang ALPHV/BlackCat are attacking corporations and public entities in the Americas and Europe. In the past three weeks, we have seen these affiliates attempt to breach a law firm, a manufacturer, and a warehouse provider within our […]
The Rhysida attackers exploit vulnerabilities like the lack of Multi-Factor Authentication (MFA) and the Zerologon vulnerability to gain initial access and maintain a presence within victims’ networks.
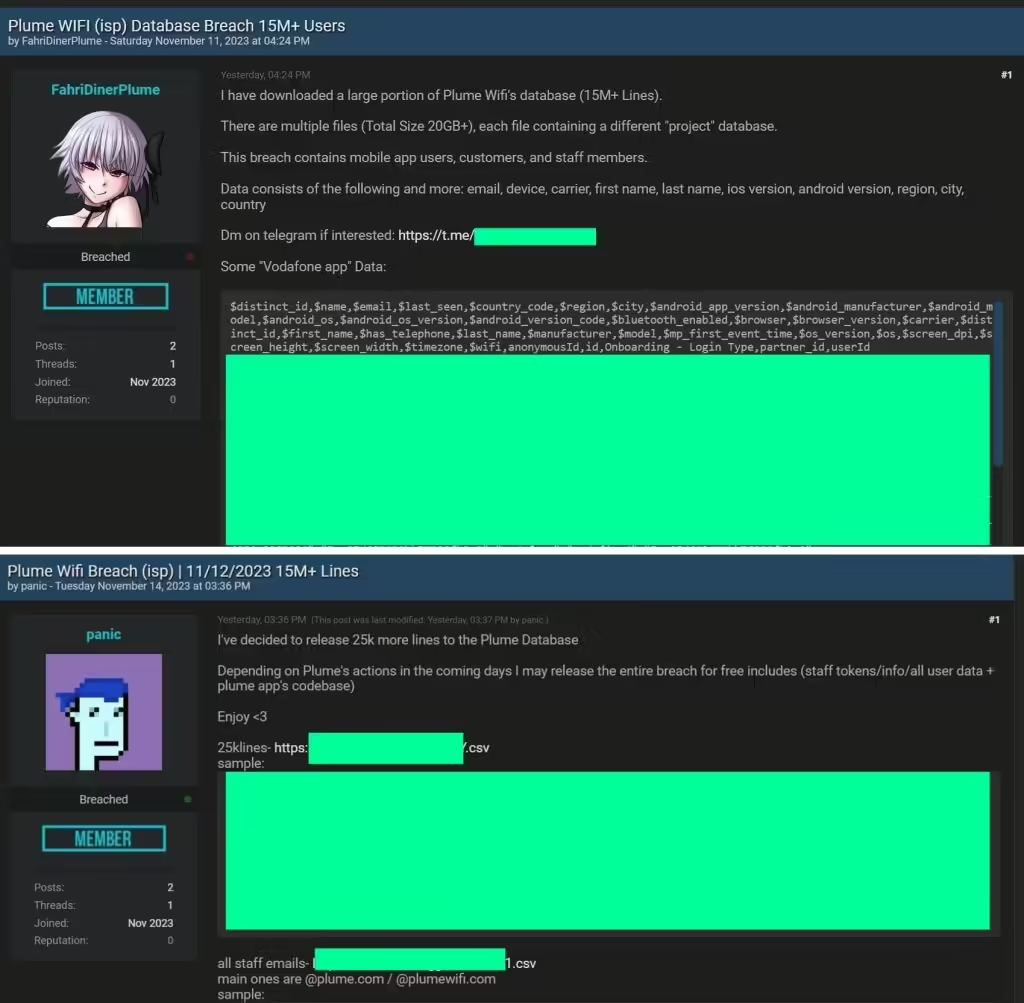
An X (Twitter) account, operated by hackers using the handle @MonkeyInject, alleges that the breach was facilitated by a former employee of Plume. The smart Wi-Fi service provider, Plume, has apparently fallen victim to a data breach. The perpetrators, claiming responsibility for the incident, made their announcement on the notorious Breach Forums. This is the […]
Nov 16, 2023NewsroomAdvanced Persistent Threat / Zero-Day A hacking group that leveraged a recently disclosed security flaw in the WinRAR software as a zero-day has now been categorized as an entirely new advanced persistent threat (APT). Cybersecurity company NSFOCUS has described DarkCasino as an “economically motivated” actor that first came to light in 2021. “DarkCasino […]