Cybersecurity
Category Added in a WPeMatico Campaign
Citrix provides additional measures to address Citrix Bleed Pierluigi Paganini November 22, 2023 Citrix urges admins to kill NetScaler user sessions after patching their appliances against the CVE-2023-4966 Citrix Bleed vulnerability. Citrix is providing additional measures to admins who are patching their NetScaler appliances against the CVE-2023-4966 ‘Citrix Bleed‘ vulnerability. The company is urging admins […]
Nov 22, 2023NewsroomAuthentication Security / Windows A new research has uncovered multiple vulnerabilities that could be exploited to bypass Windows Hello authentication on Dell Inspiron 15, Lenovo ThinkPad T14, and Microsoft Surface Pro X laptops. The flaws were discovered by researchers at hardware and software product security and offensive research firm Blackwing Intelligence, who found […]
Ransomware and cyber extortion attacks aimed at organizations are not letting up. Occasionally, they even come in pairs. The often large and sometimes massive ransomware recovery costs companies incur when they decide not to meet the demands deter many other victims from taking that path. In the end, many organizations decide to pay to get […]
Finance & Banking , Fraud Management & Cybercrime , Industry Specific New Analysis Says Cyberattack Sent Failed Trading Rates Soaring to $60 Billion Chris Riotta (@chrisriotta) • November 21, 2023 Image: Shutterstock New reports are beginning to reveal the extent of fallout from a ransomware attack that targeted the Industrial and Commercial Bank […]
The U.S. Navy on Tuesday released its long-awaited cyber strategy, as the service tries to revamp its efforts in the digital domain after years of personnel and readiness issues. The strategy is a more detailed version of the two-page Navy Cyberspace Superiority Vision that was released last year. The document was expected to be unveiled […]
Enterprise software provider TmaxSoft leaks 2TB of data Pierluigi Paganini November 22, 2023 TmaxSoft, a Korean IT company developing and selling enterprise software has leaked over 50 million sensitive records. The 2 TB-strong Kibana dashboard has been exposed for over two years. Cybernews researchers discovered it back in January 2023, noting the set of data […]
There has been a significant decrease in vulnerabilities found in target applications – from 97% in 2020 to 83% in 2022 – an encouraging sign that code reviews, automated testing and continuous integration are helping to reduce common programming errors, according to Synopsys. The report details three years of data (2020 – 2022) derived from […]
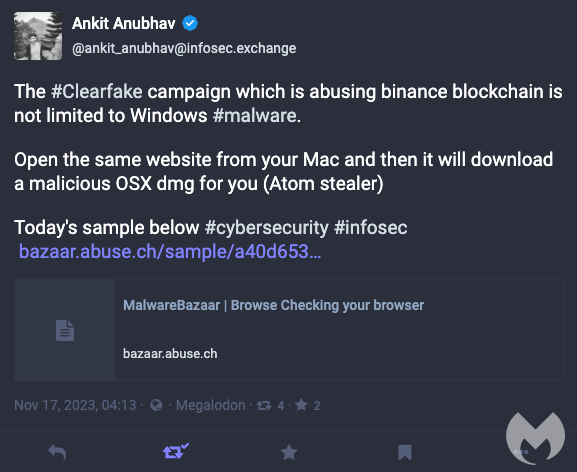
Atomic Stealer, also known as AMOS, is a popular stealer for Mac OS. Back in September, we described how malicious ads were tricking victims into downloading this piece of malware under the disguise of a popular application. In an interesting new development, AMOS is now being delivered to Mac users via a fake browser update […]
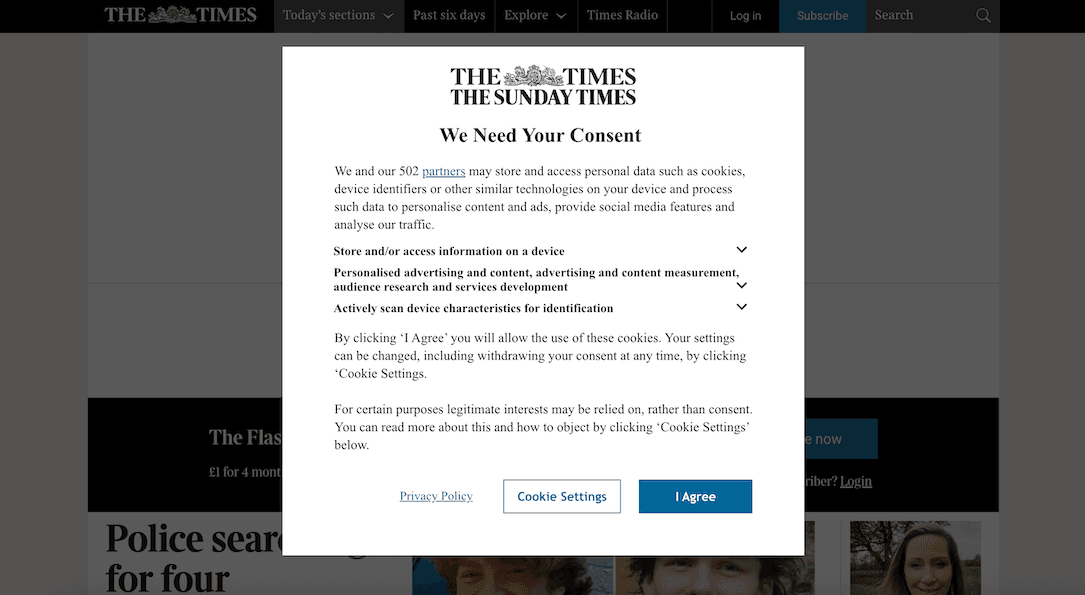
Britain’s data protection regulator has warned some of the country’s most visited websites that they risk being fined unless they stop coercing visitors into accepting advertising cookies. The Information Commissioner’s Office (ICO) announced on Tuesday that the top websites in the United Kingdom had 30 days to comply with the country’s privacy laws or they […]