Cybersecurity
Category Added in a WPeMatico Campaign
Dec 21, 2023NewsroomMobile Security / Banking Trojan Cybersecurity researchers have discovered an updated version of an Android banking malware called Chameleon that has expanded its targeting to include users in the U.K. and Italy. “Representing a restructured and enhanced iteration of its predecessor, this evolved Chameleon variant excels in executing Device Takeover (DTO) using the […]
Google addressed a new actively exploited Chrome zero-day Pierluigi Paganini December 20, 2023 Google has released emergency updates to address a new actively exploited zero-day vulnerability in the Chrome browser. Google has released emergency updates to address a new zero-day vulnerability, tracked as CVE-2023-7024, in its web browser Chrome. The flaw has been addressed with […]
The Securities and Exchange Commission has officially reached the implementation dates for its historic cyber incident reporting requirements. The rules, which require companies to report material cyber incidents within four business days of determination, are leading to significant changes in how companies prepare for and implement cyber risk strategies at the highest levels of publicly […]
Indian information technology company HCL Technologies reported a ransomware attack to regulators on Wednesday and said that it is investigating the incident. In a filing with the National Stock Exchange of India, the company said it “has become aware of a ransomware incident in an isolated cloud environment for one of its projects.” “There has […]
Scammers are taking advantage of the last-minute rush to order Christmas gifts, with one threat intelligence vendor claiming to have seen a 34% increase in new phishing sites impersonating delivery services. Group-IB said it identified 587 sites designed to look like legitimate postal operators and delivery companies in the first 10 days of December, up […]
On December 20, 2023, Rosvodokanal, the Russian water utility firm, experienced a alleged cyberattack perpetrated by the Ukrainian hacker group Blackjack. Multiple undisclosed law enforcement sources confirmed the occurrence of a cyberattack on the IT infrastructure of the Russian water utility. The announcement of the Russian water utility cyberattack was followed by the cyberattack against […]
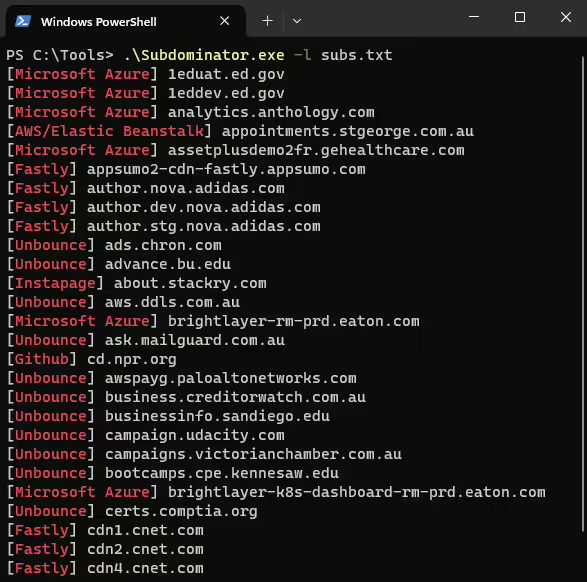
Subdominator is a dependable and fast open-source command-line interface tool to identify subdomain takeovers. It boasts superior accuracy and reliability, offering improvements compared to other tools. “Initially, Subdominator was created internally because all the current subdomain takeover tools had gaps in their functionality. No tool had a complete set of accurate service fingerprints or features. […]
The campaign sends phishing emails pretending to be from Meta, Instagram’s parent company, claiming that the recipient’s account has been restricted due to copyright infringement.
Bringing artificial intelligence into the cybersecurity field has created a vicious cycle. Cyber professionals now employ AI to enhance their tools and boost their detection and protection capabilities, but cybercriminals are also harnessing AI for their attacks. Security teams then use more AI in response to the AI-driven threats, and threat actors augment their AI […]