Cybersecurity
Category Added in a WPeMatico Campaign
New Version of Meduza Stealer Released in Dark Web Pierluigi Paganini December 29, 2023 The Resecurity’s HUNTER unit spotted a new version of the Meduza stealer (version (2.2)) that was released in the dark web. On Christmas Eve, Resecurity’s HUNTER unit spotted the author of perspective password stealer Meduza has released a new version (2.2). […]
Jan 02, 2024The Hacker NewsBrowser Security / Threat Protection Security stakeholders have come to realize that the prominent role the browser has in the modern corporate environment requires a re-evaluation of how it is managed and protected. While not long-ago web-borne risks were still addressed by a patchwork of endpoint, network, and cloud solutions, it […]
Jan 02, 2024NewsroomData Privacy / Online Tracking Google has agreed to settle a lawsuit filed in June 2020 that alleged that the company misled users by tracking their surfing activity who thought that their internet use remained private when using the “incognito” or “private” mode on web browsers. The class-action lawsuit sought at least $5 […]
PRESS RELEASE SANTA CLARA, Calif., Dec. 28, 2023 /PRNewswire/ — Palo Alto Networks (NASDAQ: PANW), the global cybersecurity leader, today announced that it has completed the acquisition of Talon Cyber Security, a pioneer of enterprise browser technology. “We are thrilled to welcome Talon to Palo Alto Networks,” said Nikesh Arora, chairman and CEO of Palo Alto Networks. “Most work […]
Clash of Clans gamers at risk while using third-party app Pierluigi Paganini December 29, 2023 An exposed database and secrets on a third-party app puts Clash of Clans players at risk of attacks from threat actors. The Cybernews research team has discovered that the Clash Base Designer Easy Copy app exposed its Firebase database and […]
Two New York hospitals are seeking a court order to retrieve stolen data stored on a cloud storage company’s servers after a ransomware attack. The stolen data includes sensitive information such as patients’ personal and health information.
Cybercriminals launched “Leaksmas” event in the Dark Web exposing massive volumes of leaked PII and compromised data Pierluigi Paganini December 28, 2023 Leaksmas: On Christmas Eve, multiple threat actors released substantial data leaks, Resecurity experts reported. On Christmas Eve, Resecurity protecting Fortune 100 and government agencies globally, observed multiple actors on the Dark Web releasing […]
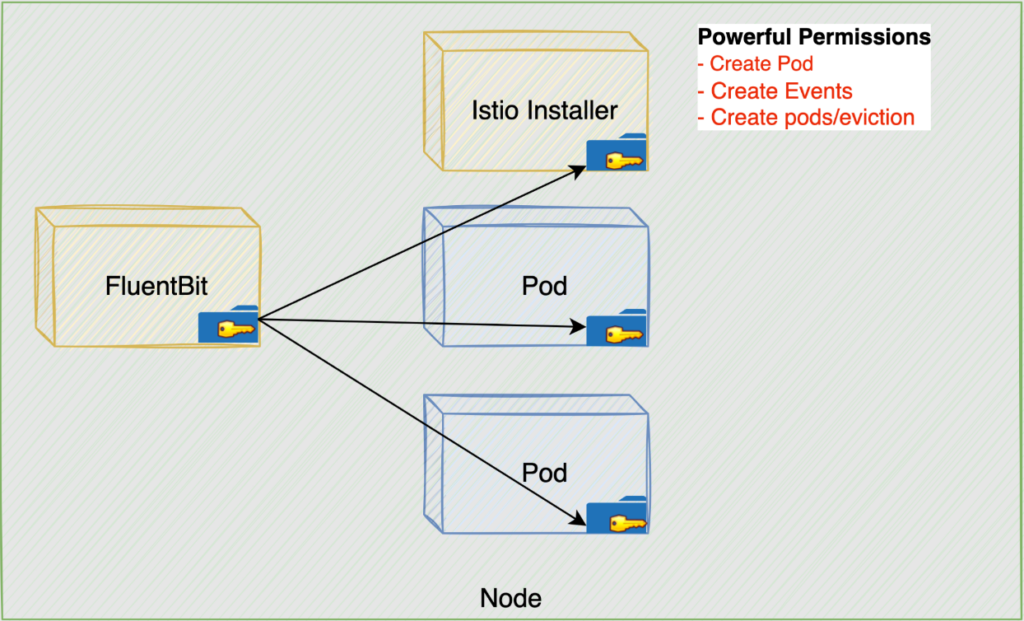
A recent Unit 42 investigation revealed a dual privilege escalation chain impacting Google Kubernetes Engine (GKE). This exploit chain arises from specific misconfigurations in GKE’s FluentBit logging agent and Anthos Service Mesh (ASM). When combined, these issues could provide attackers with existing Kubernetes cluster access an opportunity to escalate privileges. Kubernetes, a widely adopted open-source […]
Jan 01, 2024NewsroomWindows Security / Vulnerability Security researchers have detailed a new variant of a dynamic link library (DLL) search order hijacking technique that could be used by threat actors to bypass security mechanisms and achieve execution of malicious code on systems running Microsoft Windows 10 and Windows 11. The approach “leverages executables commonly found […]