Cybersecurity
Category Added in a WPeMatico Campaign
The stolen funds are believed to be linked to North Korean hacking groups, such as Lazarus, who use cryptocurrency cyberattacks to bypass international sanctions and finance their weapons development program.
As technology adoption has shifted to be employee-led, just in time, and from any location or device, IT and security teams have found themselves contending with an ever-sprawling SaaS attack surface, much of which is often unknown or unmanaged. This greatly increases the risk of identity-based threats, and according to a recent report from CrowdStrike, […]
Jan 03, 2024NewsroomCyber Threat / Email Security A new exploitation technique called Simple Mail Transfer Protocol (SMTP) smuggling can be weaponized by threat actors to send spoofed emails with fake sender addresses while bypassing security measures. “Threat actors could abuse vulnerable SMTP servers worldwide to send malicious emails from arbitrary email addresses, allowing targeted phishing […]
Jan 03, 2024NewsroomVoIP Service / Regulatory Compliance The U.S. Department of Justice (DoJ) on Tuesday said it reached a settlement with VoIP service provider XCast over allegations that it facilitated illegal telemarketing campaigns since at least January 2018, in contravention of the Telemarketing Sales Rule (TSR). In addition to prohibiting the company from violating the […]
Governance & Risk Management , Healthcare , HIPAA/HITECH NewYork-Presbyterian Disabled Website, Patient Portal Trackers in 2022 Marianne Kolbasuk McGee (HealthInfoSec) • January 2, 2024 Image: Getty State regulators have fined a large New York academic medical center $300,000 to settle privacy violations related to the organization’s prior use of tracking tools in its […]
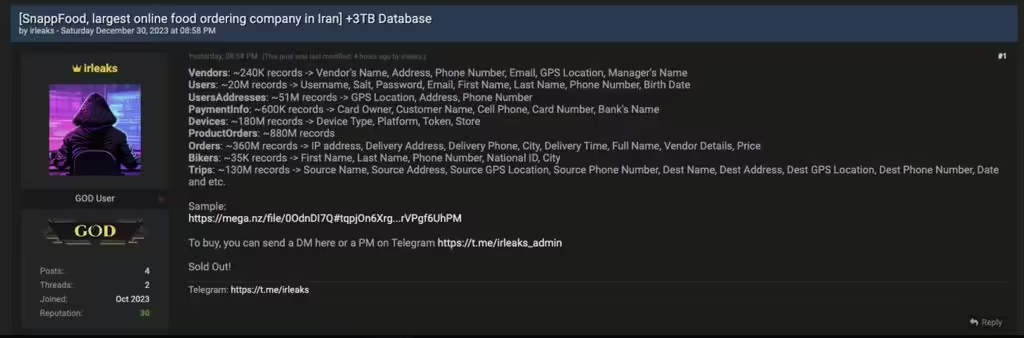
A hacker or hacker group, identified as “irleaks” (presumably indicating Iran Leaks), publicly disclosed the Snappfood cyber attack on Breach Forums and Telegram over New Year’s Eve. Snappfood, a prominent online food delivery service in Iran, has fallen victim to a major data breach, during which cybercriminals stole personal information of millions of customers, Hackread.com […]
BT has failed to meet the extended deadline to remove Huawei equipment from its core networks, with only 2G and 3G services still being served by non-compliant infrastructure.
The end of support for these older Windows versions is due to the reliance on an embedded version of Google Chrome that no longer functions on them, as well as the need for Windows feature and security updates only available on Windows 10 and above.
Managing and allocating budgets for cybersecurity and IT has become an increasingly critical aspect of organizational strategy. Organizations recognize the need to invest significantly in cybersecurity to safeguard sensitive data, protect against ransomware attacks, and ensure the integrity of their IT infrastructure. A well-structured cybersecurity budget is crucial for staying ahead of emerging threats and […]