Cybersecurity
Category Added in a WPeMatico Campaign
In the current digital landscape, data has emerged as a crucial asset for organizations, akin to currency. It’s the lifeblood of any organization in today’s interconnected and digital world. Thus, safeguarding the data is of paramount importance. Its importance is magnified in on-premises Exchange Server environments where vital business communication and emails are stored and […]
Kansas State University is managing a cybersecurity incident that has disrupted various network systems, including VPN, email services, and video platforms, impacting the educational continuity for its 20,000 students and 1,400 academic personnel.
Small business owners have been left feeling suicidal following ransomware attacks, according to new research that examines how the criminal ecosystem is causing harm beyond simply the money it extorts from victims. The new report from the Royal United Services Institute (RUSI) creates a typology of harm for ransomware, including the “significantly overlooked” psychological impact […]
Jan 19, 2024NewsroomCyber Theat / Zero-Day The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a now-patched critical flaw impacting Ivanti Endpoint Manager Mobile (EPMM) and MobileIron Core to its Known Exploited Vulnerabilities (KEV) catalog, stating it’s being actively exploited in the wild. The vulnerability in question is CVE-2023-35082 (CVSS score: 9.8), an […]
The bot gains access to the databases, deletes all tables and databases, and leaves a ransom note demanding payment for data recovery. However, the bot only saves a small portion of the data, even if the ransom is paid.
What happened Proofpoint researchers identified the return of TA866 to email threat campaign data, after a nine-month absence. On January 11, 2024, Proofpoint blocked a large volume campaign consisting of several thousand emails targeting North America. Invoice-themed emails had attached PDFs with names such as “Document_[10 digits].pdf” and various subjects such as “Project achievements”. The […]
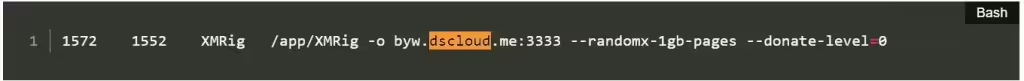
Jan 18, 2024NewsroomServer Security / Cryptocurrency Vulnerable Docker services are being targeted by a novel campaign in which the threat actors are deploying XMRig cryptocurrency miner as well as the 9Hits Viewer software as part of a multi-pronged monetization strategy. “This is the first documented case of malware deploying the 9Hits application as a payload,” […]
Cybercriminals are targeting vulnerable Docker servers by deploying two containers: a standard XMRig miner and the 9Hits viewer application—an automated traffic exchange system. Cado Security researchers have discovered a new campaign targeting vulnerable Docker servers, deploying two containers – a regular XMRig miner and the 9hits viewer application. This is the first documented case of malware deploying the […]
Jan 18, 2024NewsroomSupply Chain Attacks / AI Security Continuous integration and continuous delivery (CI/CD) misconfigurations discovered in the open-source TensorFlow machine learning framework could have been exploited to orchestrate supply chain attacks. The misconfigurations could be abused by an attacker to “conduct a supply chain compromise of TensorFlow releases on GitHub and PyPi by compromising […]