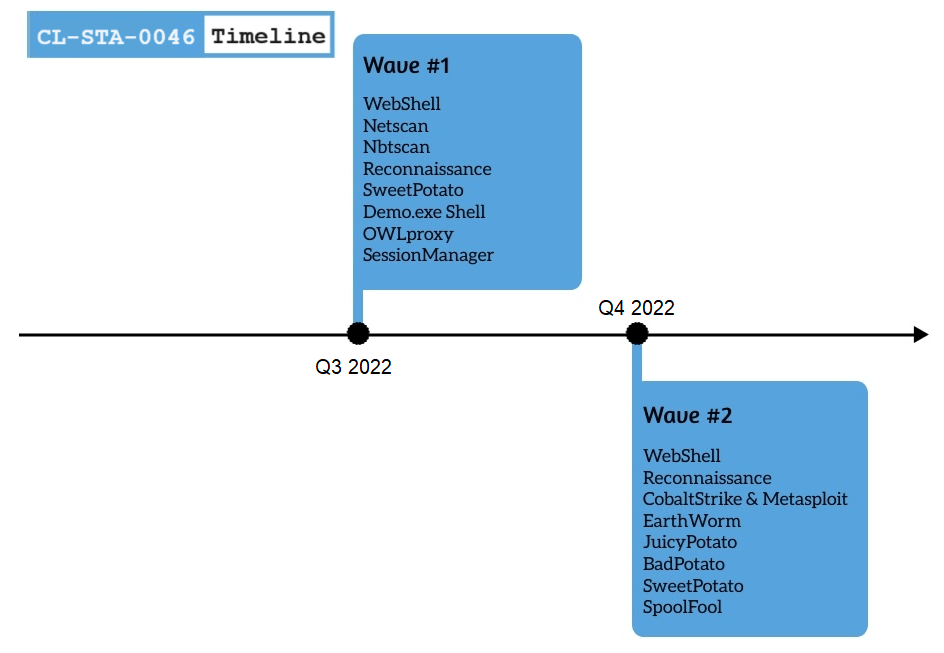
Is Gelsemium APT behind a targeted attack in Southeast Asian Government? Pierluigi Paganini September 25, 2023 A stealthy APT group tracked as Gelsemium was observed targeting a Southeast Asian government between 2022 and 2023. Palo Alto Unit42 researchers an APT group tracked as Gelsemium targeting a Southeast Asian government. The experts tracked the cluster as […]
One of the first North American organizations to suffer a data breach because of a vulnerability in the MOVEit file-transfer software says it has notified more than 165,000 people that their personal information was stolen. The government of Nova Scotia said on Thursday that it has finished sending letters to all victims of the incident […]
The Known Exploited Vulnerabilities (KEV) Catalog maintained by the US cybersecurity agency CISA has led to significant improvements in federal agencies’ patching efforts, with more than 1,000 vulnerabilities now included in the list. Launched in November 2021, the KEV Catalog lists flaws that CISA has proof are being exploited in malicious attacks, and is accompanied […]
What is ENIAC (Electronic Numerical Integrator And Computer)? ENIAC (Electronic Numerical Integrator And Computer) was the world’s first general-purpose electronic computer. ENIAC is also considered the world’s first programmable computer, although programming the computer was a complex, manual process that could take days. Even so, ENIAC was 1,000 times faster than anything else in existence […]
New Zealand’s third-largest university has been able to continue operating despite a cyberattack that forced officials to isolate affected servers. The Auckland University of Technology serves more than 29,000 students across three campuses in the country’s largest metropolitan area. Jeremy Scott, senior corporate communications manager at the university, told Recorded Future News that the school […]
More than 97% of the world’s internet traffic passes through subsea cables at some point, according to ENISA. Subsea cables are a vital component of the global internet infrastructure, and it is critical to protect them from cyberattacks, physical attacks and other threats. What are the challenges? With the growing reliance on the internet, and […]
The adoption of passkeys by GitHub, Microsoft, and Google, among other technology giants, demonstrates a growing trend toward using passkeys for secure authentication across platforms.
An unnamed Southeast Asian government has been targeted by multiple China-nexus threat actors as part of espionage campaigns targeting the region over extended periods of time. “While this activity occurred around the same time and in some instances even simultaneously on the same victims’ machines, each cluster is characterized by distinct tools, modus operandi, and […]
Last updated 25 September, 2023 Mixo, the “master DJ library” app for your phone and computer, has hit v1.1, adding a host of new features inspired by feedback from the 1.0 DJ user base. Mixo allows DJs to keep a “master” music library in their Google Drive, Dropbox or OneDrive cloud storage and easily transfer […]