Scammers have started creating videos implying leaked sensitive photos of celebrities and urging viewers to download the Temu app and enter their referral number to view the content. These scams have been targeting multiple celebrities.
Enlarge Getty Images Incomplete information included in recent disclosures by Apple and Google reporting critical zero-day vulnerabilities under active exploitation in their products has created a “huge blindspot” that’s causing a large number of offerings from other developers to go unpatched, researchers said Thursday. Two weeks ago, Apple reported that threat actors were actively exploiting […]
Dive Brief: The average annual cost of insider cybersecurity threats increased to $16.2 million during the past 12 months, a 40% increase over four years, according to research conducted by the Ponemon Institute. The biggest costs associated with insider risks came after the incident had occurred, with containment and remediation representing the most expensive areas at […]
A cryptocurrency business based in Hong Kong announced on Monday that hackers had stolen around $200 million of its assets after attacking its cloud service provider. Mixin, which describes itself as building “open source software that always puts security, privacy and decentralization first” announced the incident in a social media post. The company said that […]
Kosi Goodness Simon-Ebo, a Nigerian national, pleaded guilty to wire fraud and money laundering through business email compromise (BEC) schemes, resulting in millions of dollars in losses.
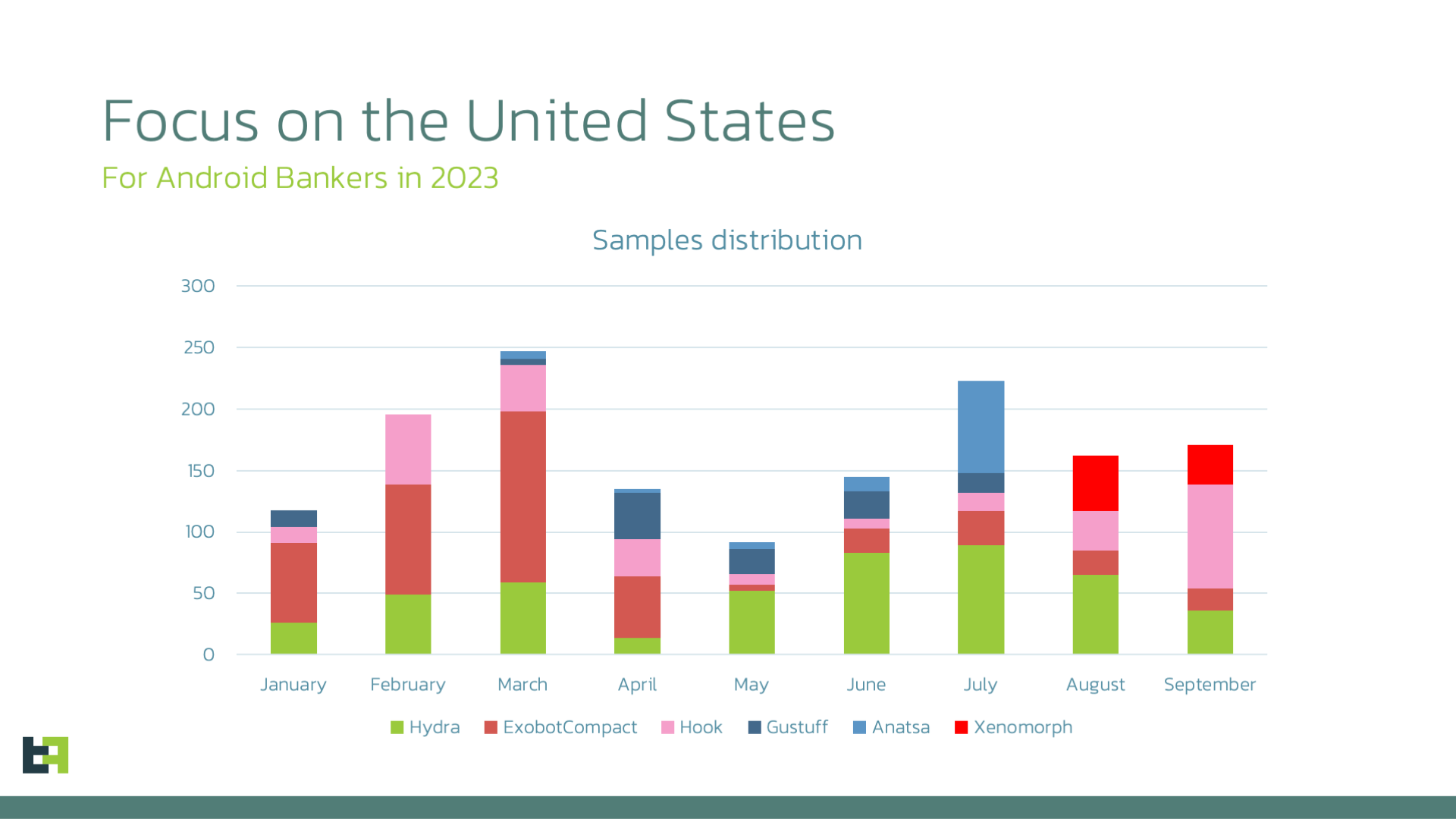
A New Xenomorph Campaign Anyone familiar with the famous movie “Alien”, directed by Ridley Scott in 1979, is well aware of how hard it is to get rid of the titular monsters of this franchise. Despite all the efforts from the protagonists, the monsters seem to always return. When we discovered and named Xenomorph, in […]
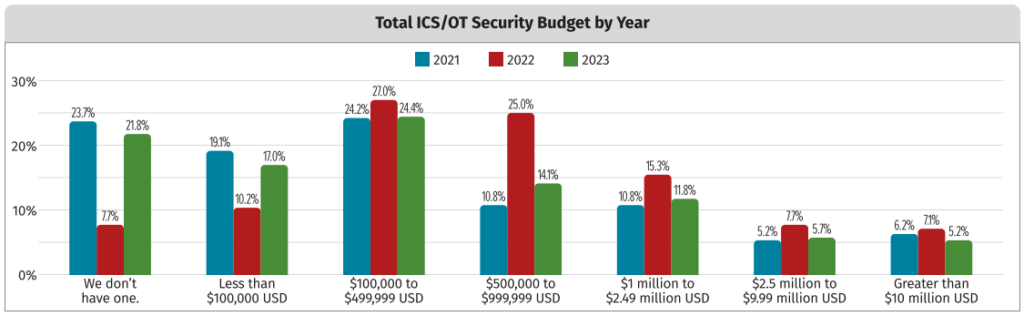
A survey conducted by the SANS Institute shows that the budgets allocated by organizations for the security of industrial control systems (ICS) and other operational technology (OT) has decreased significantly in 2023 compared to the previous year. For its 2023 ICS/OT Cybersecurity Survey (PDF), SANS surveyed over 700 individuals from every continent. The respondents represent […]
Sep 25, 2023THNCyber Attack / Phishing Ukrainian military entities are the target of a phishing campaign that leverages drone manuals as lures to deliver a Go-based open-source post-exploitation toolkit called Merlin. “Since drones or Unmanned Aerial Vehicles (UAVs) have been an integral tool used by the Ukrainian military, malware-laced lure files themed as UAVs service […]
A novel and sophisticated backdoor malware named Deadglyph was seen used in a cyberespionage campaign targeting a government agency in the Middle East. The malware is attributed to the Stealth Falcon hacking group, which is infamous for targeting activists, journalists, and dissidents. Deadglyph infection method While the exact delivery method is currently unknown, it is […]