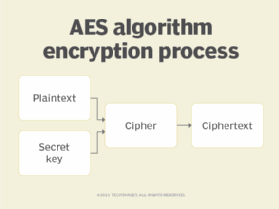
Encrypted SSDs have existed for more than a decade, but many end users and some sys admins don’t fully understand them. Most SSDs are self-encrypting drives (SEDs) that support internal encryption. However, there are various levels of encryption, reasons for using it and vendors that supply it, so organizations have a lot to consider. How […]
SOC 2, ISO, HIPAA, Cyber Essentials – all the security frameworks and certifications today are an acronym soup that can make even a compliance expert’s head spin. If you’re embarking on your compliance journey, read on to discover the differences between standards, which is best for your business, and how vulnerability management can aid compliance. […]
Sep 26, 2023THNMobile Security / Malware An updated version of an Android banking trojan called Xenomorph has set its sights on more than 35 financial institutions in the U.S. The campaign, according to Dutch security firm ThreatFabric, leverages phishing web pages that are designed to entice victims into installing malicious Android apps that target a […]
Despite some positive developments, the impact of ransomware attacks remains high, according to SpyCloud. Infostealer infections preceded 22% of ransomware events for North American and European ransomware victim companies in 2023 – with common infostealers such as Raccoon, Vidar, and Redline increasing the probability even further. SpyCloud’s analysis shows that 76% of infections that preceded […]
How To Use This Report Enhance situational awareness of techniques used by threat actors Identify potential attacks targeting your industry Gain insights to help improve and accelerate your organization’s threat response Summary of Findings The Network Effect Threat Report offers insights based on unique data from Fastly’s Next-Gen WAF from Q2 2023 (April 1, 2023 […]
Key Takeaways Proofpoint identified a new malware called ZenRAT being distributed via fake installation packages of the password manager Bitwarden. The malware is specifically targeting Windows users and will redirect people using other hosts to a benign webpage. At this time, it is unknown how the malware is being distributed. The malware is a modular […]
Changing approaches to cybersecurity have led to slow but steady progress in defense and protection. Still, competing interests create a growing challenge for cybersecurity decision makers and practitioners, according to CompTIA. The state of cybersecurity Most business and technology professionals feel that cybersecurity is improving, both generally and within their organizations. They also acknowledge that […]
Sep 26, 2023THNCyber Espionage / Malware A “multi-year” Chinese state-sponsored cyber espionage campaign has been observed targeting South Korean academic, political, and government organizations. Recorded Future’s Insikt Group, which is tracking the activity under the moniker TAG-74, said the adversary has been linked to “Chinese military intelligence and poses a significant threat to academic, aerospace […]
Security processes are increasingly automated which has led some businesses to deprioritize developing their security teams’ defense skills. While antivirus and non-human generated threat detections efficiently identify vulnerabilities, they cannot detect every single threat. With the rising number of cyber-attacks, organizations must make sure they are ready to defend themselves. That means equipping cybersecurity teams […]