Threat Report: The High Tech Industry Targeted the Most with 46% of NLX-Tagged Attack Traffic
How To Use This Report
- Enhance situational awareness of techniques used by threat actors
- Identify potential attacks targeting your industry
- Gain insights to help improve and accelerate your organization’s threat response
Summary of Findings
The Network Effect Threat Report offers insights based on unique data from Fastly’s Next-Gen WAF from Q2 2023 (April 1, 2023 to June 30, 2023). This report looks at traffic originating from IP addresses tagged by Fastly’s Network Learning Exchange (NLX), our collective threat intelligence feed that anonymously shares attack source IP addresses across all Next-Gen WAF customer networks.
Before diving deeper into the attack observations, here are five key takeaways that we found most significant in our research, covering global traffic across multiple industries, including High Tech, Financial Services, Commerce, Education, and Media and entertainment.
- Multi-customer attacks: 69% of IPs tagged by NLX targeted multiple customers, and 64% targeted multiple industries.
- Targeted Industries: The High Tech industry was targeted the most, accounting for 46% of attack traffic tagged by NLX.
- Trending Techniques: While SQL injection is a popular attack choice (28%), attackers are favoring Traversal techniques, which make up nearly one-third (32%) of attacks analyzed.
- Out-of-Band (OOB) Callbacks: Callback server domains are prevalent throughout NLX data, particularly in Log4j JNDI lookups, OS command injection, and Cross-Site Scripting (XSS) attacks. 46% of requests were utilizing known out-of-band application security testing (OAST) domains (e.g. interact.sh).
- Autonomous Systems (AS): Cloud Hosting providers are the primary sources of attack traffic. They are useful for conducting large-scale attacks, providing adversaries with cost-efficient computing resources and the ability to distribute their traffic, offering a layer of anonymity.
Report Overview
The Network Effect Threat Report is based on unique data and insights derived from Fastly’s Next-Gen WAF. Our analysis is based on NLX data from the period of Q2 2023 (April 1, 2023 to June 30, 2023, the “Reporting Period”). This report aims to deliver actionable intelligence by examining attack trends across industries, exploring the prevalence of out-of-band callbacks included in attacks, and describing traffic patterns as it relates to autonomous systems. By contextualizing threats and indicators from NLX traffic, organizations can gain a broader understanding of the overall threat landscape.
Network Learning Exchange (NLX)
Fastly’s NLX is a collective threat feed included in Next-Gen WAF, used to identify and share potentially threatening IP addresses across all customer networks. NLX is built into Next-Gen WAF so that every customer can implement preemptive protective measures against a potential attack, blocking the IP before a request even reaches their network. The shared threat data fosters a network effect, where the collective intelligence of all customers contributes to stronger security for each organization.
The Next-Gen WAF continuously collects anonymized attack data from tens of thousands of our distributed software agents across our customer base and feeds it into our Cloud Engine. By correlating patterns from the data, NLX tags IP addresses and anonymously shares them with all customers. For example, if Acme Enterprises starts to experience a series of SQL injection attacks on their login page, NLX will flag the IP and apply the SIGSCI-IP signal for the next 24 hours. Every customer using Next-Gen WAF can then apply custom rules to block, limit, or monitor the IP before it can potentially attack their applications.
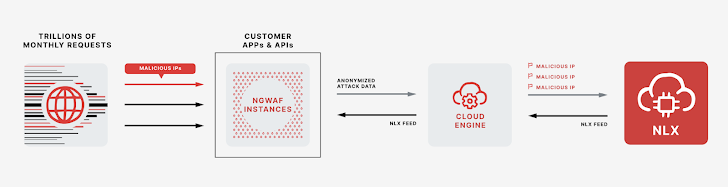 |
| Fig. 1: NLX Diagram |
As a collective threat feed, NLX gets better as our network grows and our team is able to observe attacks and analyze trends through increasing magnitudes of traffic volume. Fastly’s Next-Gen WAF protects over 90,000 apps and APIs and inspects 4.1 trillion requests per month*, covering a wide variety of industries, including some of the largest e-commerce, streaming, media and entertainment, and technology companies around the world. The breadth of our reach, especially with modern architectures and cloud-native environments, allows us to generate insights that are relevant and actionable to security teams of all sizes and in all industries, while complementing the ongoing work of the greater threat intelligence community.
We can see the benefits of NLX’s network effect helping our customers in multiple ways. It ensures that organizations gain immediate awareness of potentially threatening IPs, and our report shows that attacks are not as targeted or siloed as people think: 69% of IPs are targeting multiple customers, and 64% are targeting multiple industries. The breadth of our customer base also reflects a higher-quality threat feed that allows teams to respond with greater confidence, especially since the feed is updated in real-time.
Our report draws insights from NLX’s confirmed malicious activity, allowing us to share broader trends with the same level of trust and confidence our customers rely on; the resulting deductions are proactive and accurate.
Observations
During the Reporting Period, more than half (54%) of all attacks observed were tagged with NLX and the majority of IP addresses in NLX data were not focused on a single customer or industry but spread across multiple targets: 69% of IP addresses targeted multiple customers (Figure 2), and 64% targeted multiple industries.
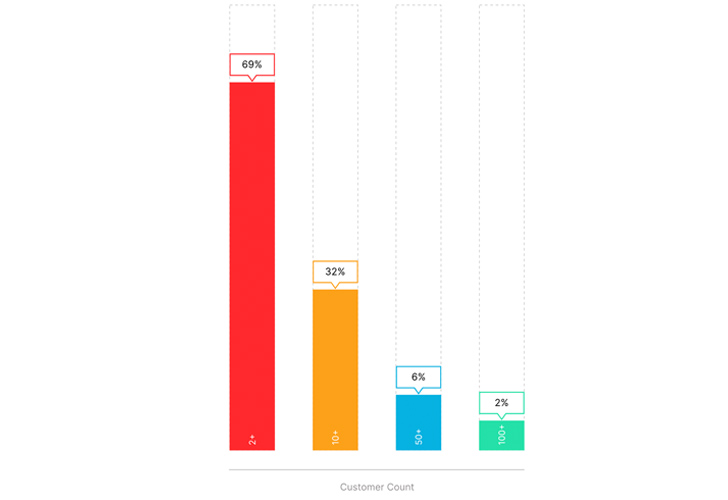 |
| Fig 2: Multi-customer attacks tagged with NLX |
The benefit of NLX’s network effect becomes more apparent when breaking down attacks tagged with and without NLX by Industry (Figure 3). The Media & Entertainment sector experienced 56% more attacks tagged with NLX, while the Commerce industry experienced 36% more, and the High Tech industry experienced 24% more.
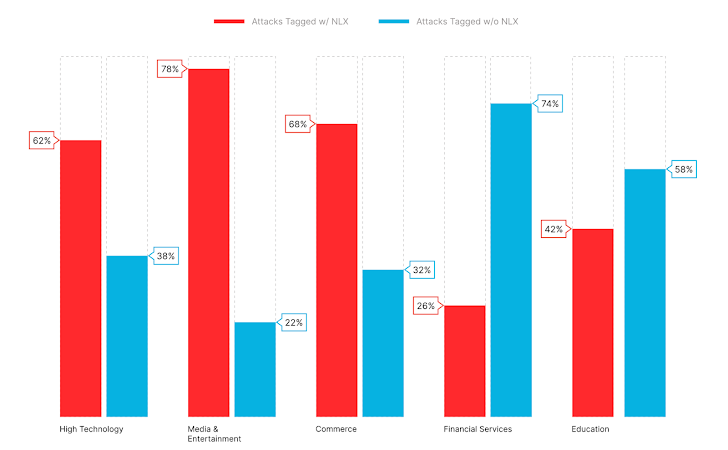 |
| Fig. 3: Attacks tagged with and without NLX by Industry |
Although the Financial Services and Education industries recorded fewer attacks tagged with NLX, NLX still accounts for a considerable portion of each industry’s overall attack volume.
Moreover, breaking down NLX attack traffic by industry, we see that the High Tech industry was targeted the most, accounting for 46% of attack traffic tagged with NLX (Figure 4). So while the Media and Entertainment industry benefited the most from the NLX’s network effect, the High Tech industry experienced the highest number of attacks tagged with NLX.
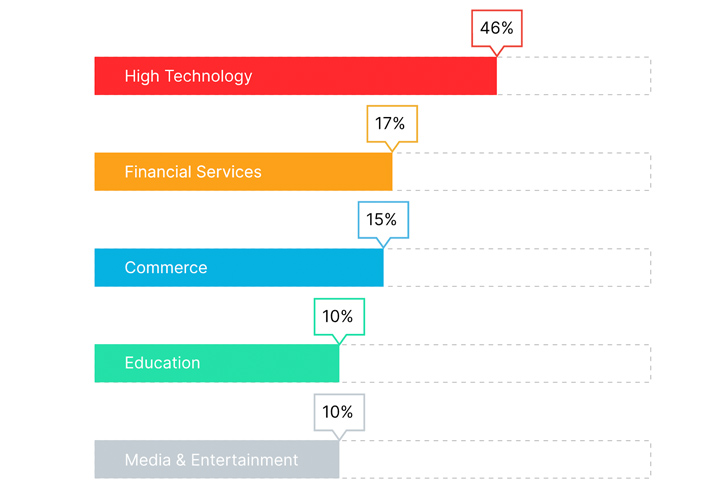 |
| Fig. 4: NLX Traffic by Industry |
Furthermore, nearly one-third (32%) of attacks analyzed in the NLX data were Traversal; while SQL Injection (SQLI) accounted for 28%, Cross Site Scripting (XSS) at 20%, OS Command Injection (CMDEXE) at 13%, and Log4j JNDI lookups (LOG4J-JNDI) at 7%.
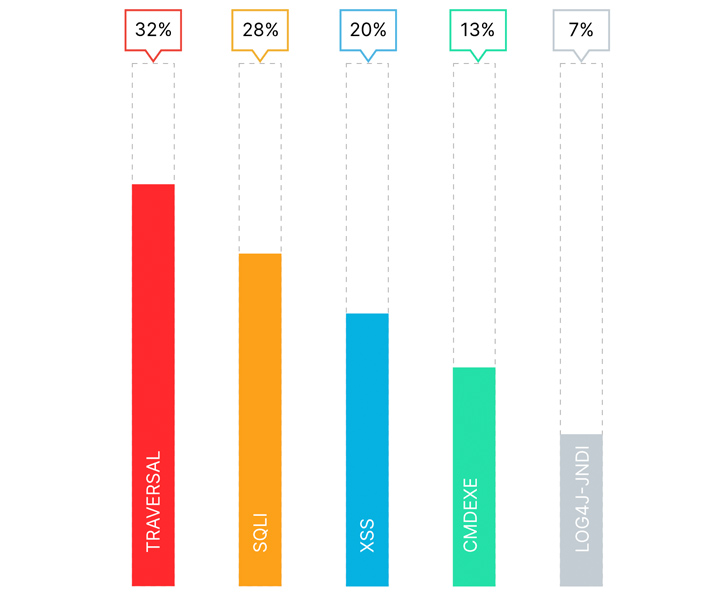 |
| Fig. 5: Top Web & API attacks tagged by NLX |
While SQL injection is a popular attack choice, attackers are favoring Traversal techniques (which overlaps with Local File Inclusion). Traversal vulnerabilities (Figure 6) enable attackers to read or write unwanted files, allowing them to reveal sensitive information, modify application data, and are commonly used to chain attacks together which can lead to remote code execution (RCE). The preference for traversal could suggest that attackers are primarily focused on finding ways to execute arbitrary commands that can be used to install malware, launch ransomware, and exfiltrate data.
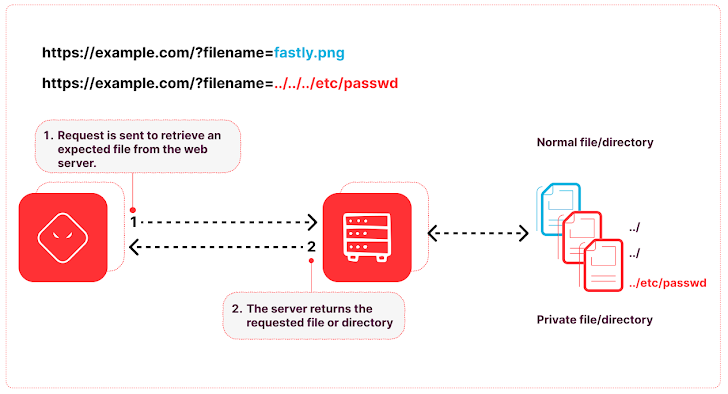 |
| Fig. 6: Traversal Vulnerability |
Similarly, the Log4j JNDI lookup vulnerability leads to RCE, giving an adversary an easy entrypoint to the targeted system. Despite the age and awareness of this vulnerability, we’re continuing to see exploit attempts. The discovery and disclosure of the Log4j JNDI lookup vulnerability, colloquially known as Log4Shell, surfaced in December of 2021, and accounts for a considerable portion (7%) of attack traffic tagged with NLX.
Out of Band Callbacks
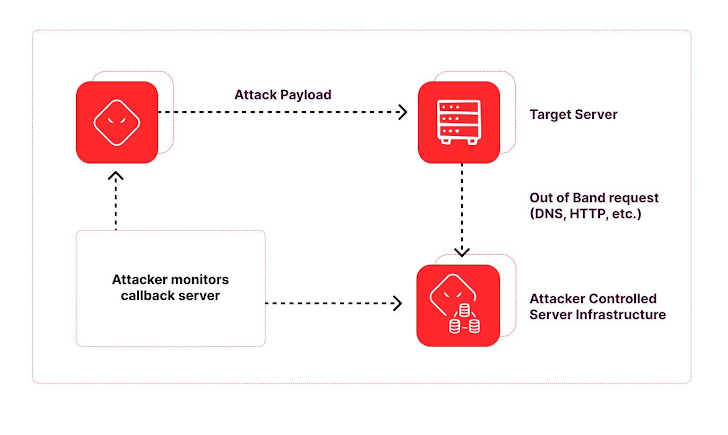
When analyzing attack traffic, knowing what to look for and where to start can be the greatest challenge. A good place to start is looking for out-of-band (OOB) callbacks. OOB callbacks are a common technique used to uncover hidden vulnerabilities. In the context of web application security, this typically involves a vulnerable application making requests to an attacker-controlled domain. Attackers use out-of-band callbacks for several reasons, including vulnerability identification, data exfiltration, dynamic payload delivery and evading detection. Monitoring and tracking out-of-band callback domains can help identify compromised systems, detect ongoing attacks, and showcase trends in attacker methodology.
 |
|
Fig. 7: Out of Band Exploitation |
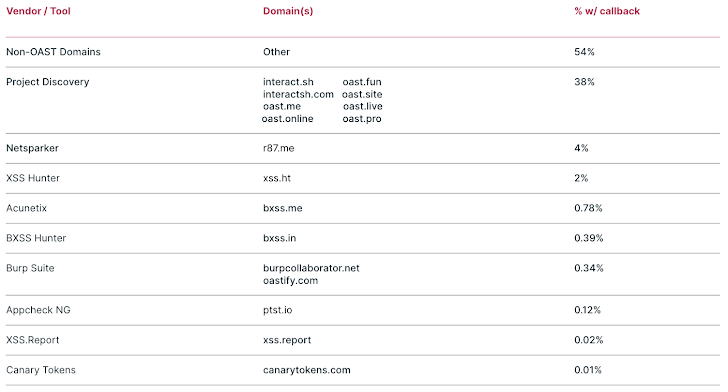
OOB callback domains are prevalent in attack payloads tagged with NLX. During the Reporting Period, we found Log4j JNDI lookups, OS Command Injection, and XSS attacks all containing OOB callbacks. Among these requests, Log4j accounted for 75%, OS Command Injection 18%, and XSS for 7%. Furthermore, 46% of those requests utilized known out-of-band application security testing (OAST) domains. OAST domains are specifically used for finding exploitable vulnerabilities and facilitated by tools such as Project Discovery (interact.sh) and Port Swigger (Burp Collaborator).
 |
| Fig. 8: Out-of-Band Callback Domains |
Autonomous Systems
Delving further, we analyzed traffic patterns concerning Autonomous Systems (AS). AS refers to networks or groups of IP addresses under a single entity’s control, typically an Internet Service Provider (ISP) or a large organization. The identification of AS plays an important role in tracking and attributing malicious activities to specific threat actors or groups; The additional context it provides helps assess potential attackers’ motives, capabilities, methodology, and intentions – which can thereby inform and improve defensive strategies.
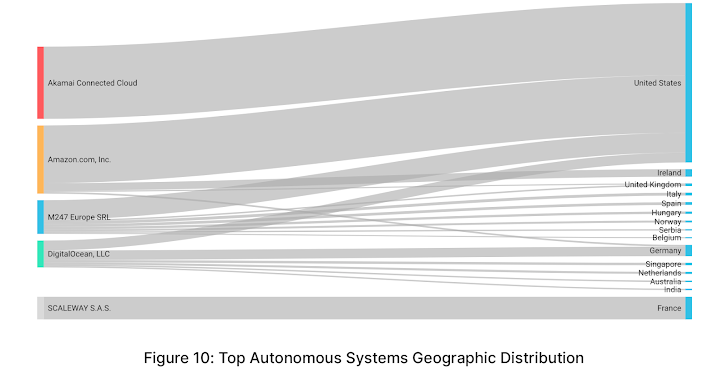
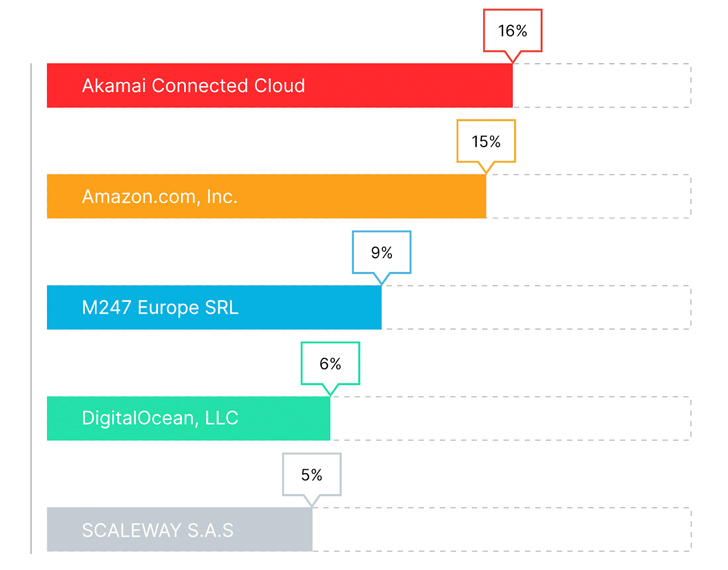
When analyzing corresponding Autonomous Systems (AS) of NLX IP addresses, Akamai Connected Cloud (formerly Linode) accounted for the largest portion of NLX traffic (16%), followed by Amazon (15%), M247 Europe SRL (9%), DigitalOcean (6%) and Scaleway (5%)**.
 |
| Fig. 9: Top Autonomous Systems (AS)1 |
All of these ASs align to cloud hosting providers. When attackers conduct cyber attacks from hosting providers, they gain ease of use, cost-efficient computing resources, scalability, and the ability to leverage geographic diversity. This allows attackers to launch large-scale attacks and choose specific cloud regions to strategically distribute their traffic to obtain a degree of anonymity. Moreover, the disposability of such infrastructure makes it very convenient to pivot in case the attack domain, application, or IP addresses gets detected or flagged as malicious.
Among the above-mentioned ASs, 61% originated from the United States, Germany represented 6%, France 6%, and Ireland 3.5%. The following chart illustrates the geographic distribution of the attack traffic from these ASs**.
Actionable Guidance
NLX
Fastly Next-Gen WAF customers can take advantage of NLX – highlighted through the SIGSCI-IP signal – to improve their detections. This signal can be used in conjunction with attack and anomaly signals, along with other custom conditions in rules. Learn more about using signals in the Next-Gen WAF documentation.
AS Attribution
While it can be convenient to add all of your cloud hosting provider’s ASN or IP addresses to an allow list, attackers frequently utilize those same providers to host their own ephemeral infrastructure. Consider tightening those IP restrictions to only the ones being used by your current instances, which can further reduce unwanted traffic going to origin. Our general recommendation is to always inspect traffic regardless of where it comes from.
OOB Callbacks
Armed with this knowledge, defenders can study OOB callbacks, either attempted or successful. Monitor DNS logs for requests originating from out-of-band callbacks used in attack payloads. If you see outbound DNS resolutions to out-of-band application security testing (OAST) domains, you likely have an exploitable web app, as they are used specifically for finding exploitable vulnerabilities. A WAF can be configured to inspect requests for known callback domains.
About Fastly Security Research
Fastly’s Security Research Team is chartered to advance threat intelligence, adversary emulation, defensive research, and community empowerment. Our team focuses on continuously analyzing the threat landscape and applying that knowledge to the technology, processes, and mitigations that Fastly offers to its customers. Our understanding of threats works from multiple angles, including our own vulnerability research, strong intelligence partnerships with private/public partners, and data analysis of the activities seen against our customers.
As a global leader in application and API security, Fastly has a distinctive viewpoint on the attack traffic we see across our network. Our team was created to offer our customers best-in-class threat research powered by our Next-Gen WAF technology. The superior decisioning of the Next-Gen WAF Cloud Engine, combined with our NLX threat feed, allows our team to analyze attack trends and validate our findings with a higher degree of confidence.
The goal for our threat reports is to provide actionable threat intelligence to our customers and contribute new findings to the greater security community. If you have any feedback on this report or suggestions for future topics, please reach out to us on Twitter or LinkedIn.
* Trailing 6 month average as of June 30, 2023
* * AS attribution supplemented by https://ipinfo.io/