Attackers are increasingly making use of “networkless” attack techniques targeting cloud apps and identities. Here’s how attackers can (and are) compromising organizations – without ever needing to touch the endpoint or conventional networked systems and services. Before getting into the details of the attack techniques being used, let’s discuss why these attacks are becoming more […]
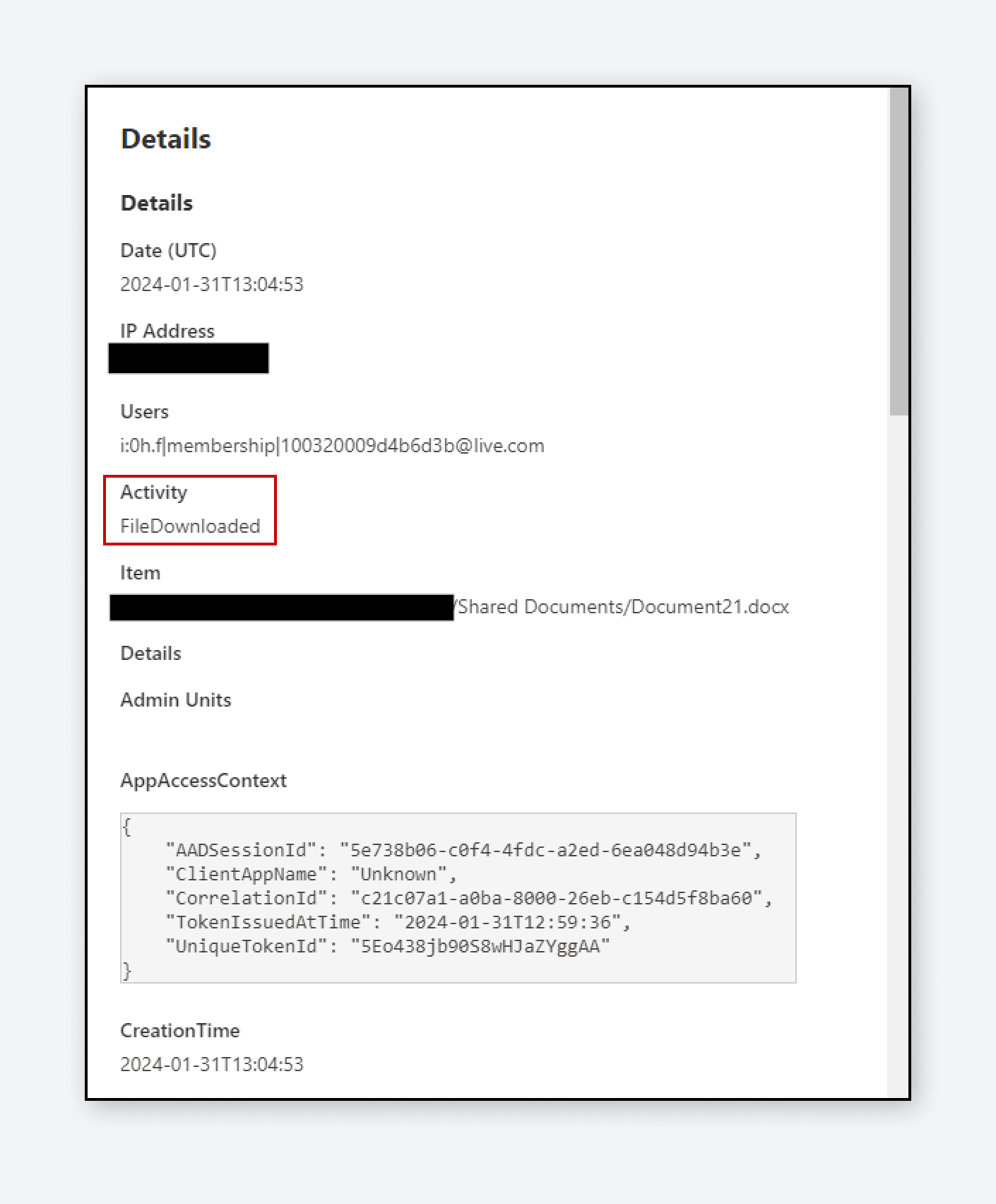
Varonis Threat Labs discovered two techniques in SharePoint that allow users to circumvent audit logs and avoid triggering download events while exfiltrating files. These techniques can bypass the detection and enforcement policies of traditional tools, such as cloud access security brokers, data loss prevention, and SIEMs, by hiding downloads as less suspicious access and sync […]
The FBI and the US Cybersecurity and Infrastructure Security Agency (CISA) have released details on the tactics and techniques threat actors are using to deploy the Phobos ransomware strain on target networks. The advisory is part of an ongoing stop-ransomware effort by the two entities working in collaboration with the Multi-State Information Sharing and Analysis […]
Morphisec Threat Labs has shared details of a new campaign that used steganography techniques to deliver the Remcos RAT onto the systems of a Ukrainian entity operating in Finland. The campaign, attributed to a hacking group named UAC-0184, used a relatively new IDAT Loader to drop the trojan. Modus operandi According to researchers, the attack […]
The threat actors behind the campaign utilized multiple stages and techniques, including obfuscation and leveraging open platforms, to carry out the attack and steal sensitive information.
Summary Threat actors often employ stealthy attack techniques to elude detection and stay under the defender’s radar. One way they do so is by using uncommon programming languages to develop malware. Using an uncommon programming language to develop malware provides several benefits, including: Evading some signature based detections Impeding analysis by malware analysts that are […]
Dec 11, 2023NewsroomEndpoint Security / Malware A new collection of eight process injection techniques, collectively dubbed PoolParty, could be exploited to achieve code execution in Windows systems while evading endpoint detection and response (EDR) systems. SafeBreach researcher Alon Leviev said the methods are “capable of working across all processes without any limitations, making them more […]
Bypassing major EDRs using Pool Party process injection techniques Pierluigi Paganini December 08, 2023 Researchers devised a novel attack vector for process injection, dubbed Pool Party, that evades EDR solutions. Researchers from cybersecurity firm SafeBreach devised a set of process injection techniques, dubbed Pool Party, that allows bypassing EDR solutions. They presented the technique at Black […]
Mandiant Says Sandworm Used Novel Techniques in Ukrainian Cyberattack Chris Riotta (@chrisriotta) • November 9, 2023 Fires on a combined heat and power plant in Kyiv after Russian missile strikes on Oct. 10, 2022 (Image: Main Directorate of the State Emergency Service of Ukraine in Kyiv) Russian military hackers in October 2022 successfully […]
- 1
- 2