CloudGrappler: Open-source tool detects activity in cloud environments – Help Net Security
CloudGrappler is an open-source tool designed to assist security teams in identifying threat actors within their AWS and Azure environments.
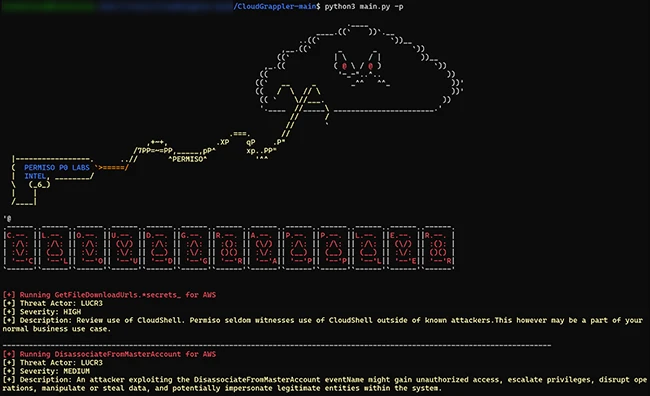
The tool, built on the foundation of Cado Security’s cloudgrep project, offers enhanced detection capabilities based on the tactics, techniques, and procedures (TTPs) of modern cloud threat actors like LUCR-3 (Scattered Spider).
CloudGrappler queries for high-fidelity activities of threat actors in the cloud. This tool can identify and scrutinize individual log events, providing a perspective on potential security incidents in real-time or retrospectively within AWS and Azure environments.
The tool allows users to define the data sources they want to scope in their scan. Through another JSON file, users can leverage a list of predefined TTPs commonly used by cloud threat actors. Users can also add new queries dynamically or create a new file with multiple queries to scan the target data set.
After scanning, CloudGrappler delivers a JSON report, including a detailed breakdown of the scan results.
“CloudGrappler brings cloud threat actor knowledge, distilled by Permiso p0 Labs, directly into the hands of security teams. The initial ruleset is designed to detect 54 TTPs from four (4) major threat actors in AWS and Azure environments, it significantly reduces the time and expertise required to identify potential threats. The initial release is all about getting the foundation set. Further releases will be focused on more detection content. The next set of TTPs we will be adding will be related to one of our favorite threat actors, APT29,” Ian Ahl, SVP of P0 Labs, told Help Net Security.
CloudGrappler is available for free on GitHub.

Must read: 15 open-source cybersecurity tools you’ll wish you’d known earlier

More open-source tools to consider:

