Attackers are adept at identifying and exploiting the most cost-effective methods of compromise, highlighting the critical need for organizations to implement asset identification and understand their assets’ security posture in relation to the whole estate. Instead of asking, “Are we exposed?” organizations should ask, “How exposed are we?” To understand this question, businesses must implement […]
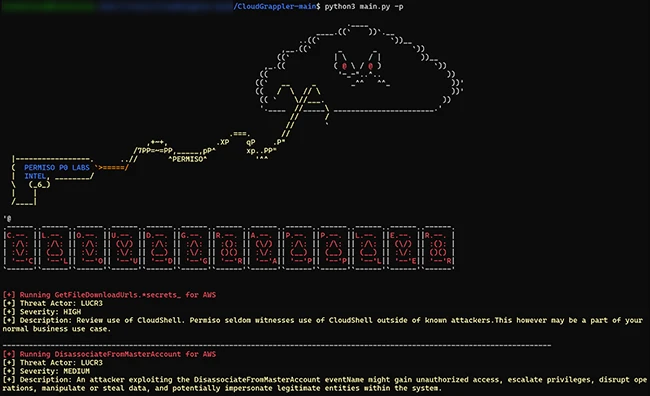
CloudGrappler is an open-source tool designed to assist security teams in identifying threat actors within their AWS and Azure environments. The tool, built on the foundation of Cado Security’s cloudgrep project, offers enhanced detection capabilities based on the tactics, techniques, and procedures (TTPs) of modern cloud threat actors like LUCR-3 (Scattered Spider). CloudGrappler queries for […]