Setting up a virtual private network on your phone or laptop means a much better level of privacy and security for you and your data. VPNs help to hide your browsing activity and protect your sensitive data from other people, including the company supplying your broadband service. Using a VPN as a privacy measure is […]
You can create room dividers in open layouts to better separate seating and dining areas, and drop in furniture to tell it what to expect in certain spaces. The in-app AI also tried to add furniture during some of the mapping, but it wasn’t accurate. The 2D map is the main one that you’ll edit […]
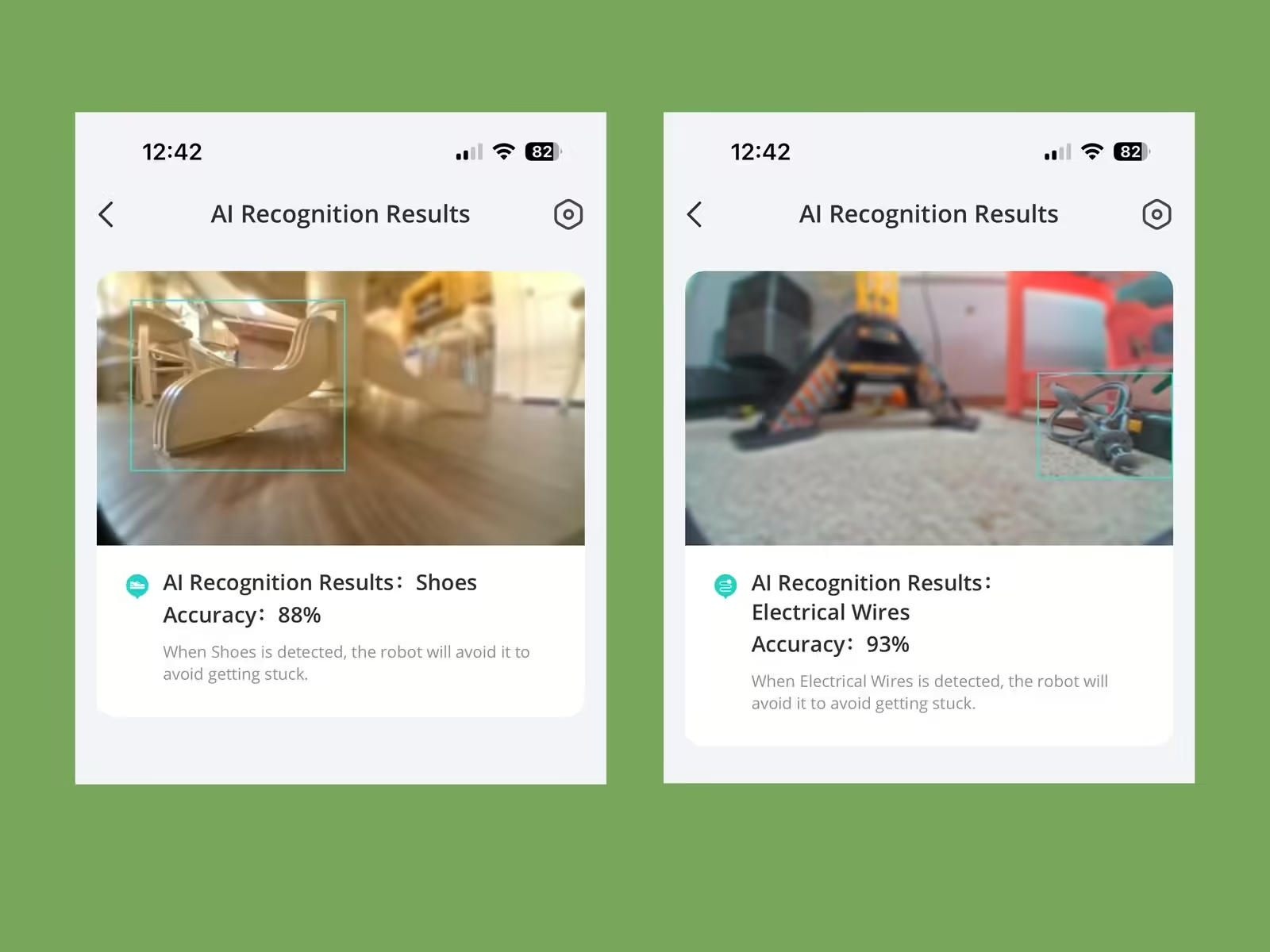
Like last year’s model, it also meets the TÜV Rheinland privacy and security certification. This is important, because it navigates via AI.See—a “visual recognition technology.” Basically, it uses a camera to steer around your house. It’s not upward-facing, and Eufy assures its customers that the photos are not stored in a server and are deleted […]
A burr grinder is the automatic, electronic version of the manual coffee mills people have been using to grind coffee for centuries. Whether it’s a flat or conical burr grinder (I explain the differences in my Best Coffee Grinders guide), those heavy-duty burrs are going to break coffee beans down into a relatively uniform size, […]
Spring isn’t just the time for cleaning your home. It’s also the time for renovating, refurbishing, and restoring. That yard work project you put off last fall? Those garage projects you wanted to do all winter when it was too cold to work out there? Now’s the time to stock up on tools and gear, […]
Do you know what TCP/IP means? (Hint: You’re using it right now.) What about CDMA? Or GPT? While the concepts and execution of these technologies are clear to most of us who have been on the internet nearly our whole lives, the acronyms we use to define them are often inscrutable. On this week’s episode, […]
Dear reader, I am exhausted. Over the past few days, the House and Senate passed a massive foreign aid package that also forces TikTok to divest from its China-based owner ByteDance and find a new American owner—or else be banned nationwide. President Joe Biden signed that bill into law, and TikTok has threatened to sue […]
Follow this real-life network attack simulation, covering 6 steps from Initial Access to Data Exfiltration. See how attackers remain undetected with the simplest tools and why you need multiple choke points in your defense strategy. Surprisingly, most network attacks are not exceptionally sophisticated, technologically advanced, or reliant on zero-day tools that exploit edge-case vulnerabilities. Instead, […]
Meta’s online ad library shows the company is hosting thousands of ads for AI-generated, NSFW companion or “girlfriend” apps on Facebook, Instagram, and Messenger. They promote chatbots offering sexually explicit images and text, using NSFW chat samples and AI images of partially clothed, unbelievably shaped, simulated women. Many of the virtual women seen in ads […]