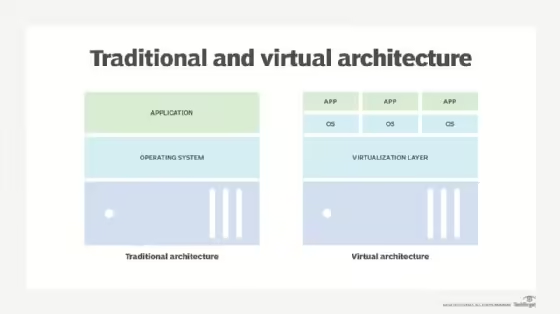
IT administrators who combine virtualization with a server consolidation plan can improve server utilization and reduce data center power consumption and hardware costs. A server consolidation plan can include one of two consolidation methods: migrating workloads to a server’s OS or using virtualization to run applications inside of VMs. Virtualization is often the preferred choice […]
Last updated 3 April, 2024 Join Phil Morse of the Digital DJ Tips DJ school, as he answers another batch of student questions about their DJing. About this podcast This is the video version of our monthly Your Questions show, where Digital DJ Tips course owners get to ask questions and get help with their […]
Cisco Talos Incident Response (Talos IR) has observed the ongoing use of legitimate digital document publishing (DDP) sites for phishing, credential theft and session token theft during recent incident response and threat intelligence engagements. Hosting phishing lures on DDP sites increases the likelihood of a successful phishing attack, since these sites often have a favorable […]
The stolen data includes sensitive personal details such as full name, date of birth, social security number, and contact information, posing a significant risk of identity theft and phishing.
Dive Brief: Officials from the White House and the U.S. Department of Health and Human Services held a meeting on Tuesday with UnitedHealth and other industry groups to discuss the cyberattack at Change Healthcare, which has disrupted the healthcare sector for three weeks. HHS Secretary Xavier Becerra and White House Domestic Policy Advisor Neera Tanden […]
Czech software giant JetBrains harshly criticized security company Rapid7 this week following a dispute over two recently-discovered vulnerabilities. In a blog post published Monday, JetBrains attributed the compromise of several customers’ servers to Rapid7’s decision to release detailed information on the vulnerabilities. “After the full disclosure was made, we started hearing from some customers who […]
While the results of law enforcement action against ransomware-as-a-service operators Alphv/BlackCat and LockBit are yet to be fully realized, the August 2023 disruption of the Qakbot botnet has had one notable effect: ransomware affiliates have switched to vulnerability exploitation as the primary method of delivering the malware. The switch is obvious to Symantec’s Threat Hunter […]
The breach resulted in the theft of various sensitive information, including government identification like Medicare cards, driving licenses, passports, and tax file numbers.
Cybercrime , Fraud Management & Cybercrime Repeat Crackdowns Drive Criminals to Embrace Foreign-Made Encrypted Messaging Apps Mathew J. Schwartz (euroinfosec) • March 13, 2024 Chinese criminals prefer not to draw the state’s attention. (Image: Shutterstock) Think “Chinese hackers” and most likely Beijing’s many state espionage threat actors come to mind. Partly, says cybersecurity […]