Mar 04, 2024The Hacker NewsSaaS Security / Vulnerability Assessment A company’s lifecycle stage, size, and state have a significant impact on its security needs, policies, and priorities. This is particularly true for modern mid-market companies that are either experiencing or have experienced rapid growth. As requirements and tasks continue to accumulate and malicious actors remain […]
Multistage RA World Ransomware Uses Anti-AV Tactics, Exploits GPO Ransomware The Trend Micro threat hunting team came across an RA World attack involving multistage components designed to ensure maximum impact. By: Nathaniel Morales, Katherine Casona, Ieriz Nicolle Gonzalez, Ivan Nicole Chavez, Maristel Policarpio, Jacob Santos March 04, 2024 Read time: ( words) The RA World […]
The alliance between ransomware groups and initial access brokers (IABs) is still the powerful engine for cybercriminal industry, as evidenced by the 74% year-on-year increase in the number of companies that had their data uploaded on dedicated leak sites (DLS), according to Group-IB’s Hi-Tech Crime Trends 2023/2024 report. Global threat actors also demonstrated increased interest […]
U.S. Judge ordered NSO Group to hand over the Pegasus spyware code to WhatsApp Pierluigi Paganini March 03, 2024 A U.S. Court ordered surveillance firm NSO Group to hand over the source code for its Pegasus spyware and other products to Meta. Meta won the litigation against the Israeli spyware vendor NSO Group, a U.S. Judge ordered […]
U.S. authorities charged an Iranian national for long-running hacking campaign Pierluigi Paganini March 02, 2024 The U.S. DoJ charged Iranian national Alireza Shafie Nasab for his role in attacks targeting U.S. government and defense entities. The U.S. Department of Justice (DoJ) charged Iranian national Alireza Shafie Nasab (39) for multi-year hacking campaign targeting U.S. defense […]
Cybercriminals are targeting Mac users interested in cryptocurrency opportunities with fake calendar invites. During the attacks the criminals will send a link supposedly to add a meeting to the target’s calendar. In reality the link runs a script to install Mac malware on the target’s machine. Cybersecurity expert Brian Krebs investigated and flagged the issue. […]
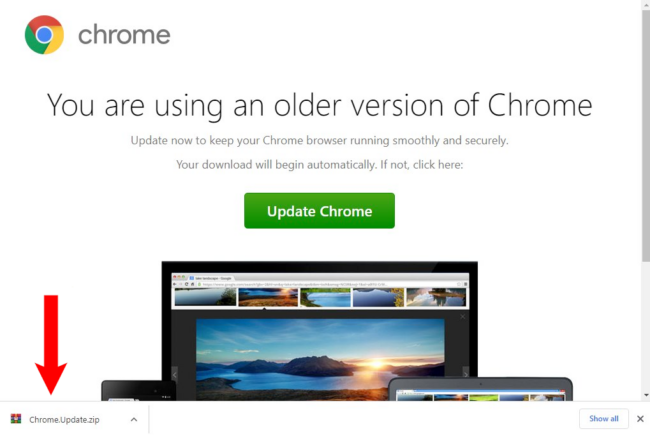
SocGholish malware, otherwise known as “fake browser updates”, is one of the most common types of malware infections that we see on hacked websites. This long-standing malware campaign leverages a JavaScript malware framework that has been in use since at least 2017. The malware attempts to trick unsuspecting users into downloading what is actually a […]
Mar 04, 2024NewsroomAI Security / Vulnerability As many as 100 malicious artificial intelligence (AI)/machine learning (ML) models have been discovered in the Hugging Face platform. These include instances where loading a pickle file leads to code execution, software supply chain security firm JFrog said. “The model’s payload grants the attacker a shell on the compromised […]
Cybersecurity researchers have identified new infrastructure likely used by the operators of the commercial spyware known as Predator in at least 11 countries. By analyzing the domains likely used to deliver the spyware, analysts at Recorded Future’s Insikt Group were able to spot potential Predator customers in Angola, Armenia, Botswana, Egypt, Indonesia, Kazakhstan, Mongolia, Oman, […]