National intelligence agency of Moldova warns of Russia attacks ahead of the presidential election Pierluigi Paganini March 07, 2024 The national intelligence agency of Moldova warns of hybrid attacks from Russia ahead of the upcoming elections. The Moldovan national intelligence agency warns of hybrid attacks from Russia ahead of the upcoming elections. 2024 is a […]
The NSA and CISA have issued five joint bulletins outlining best practices for securing cloud environments, covering identity and access management, key management, encryption, data security, and mitigating risks from managed service providers.
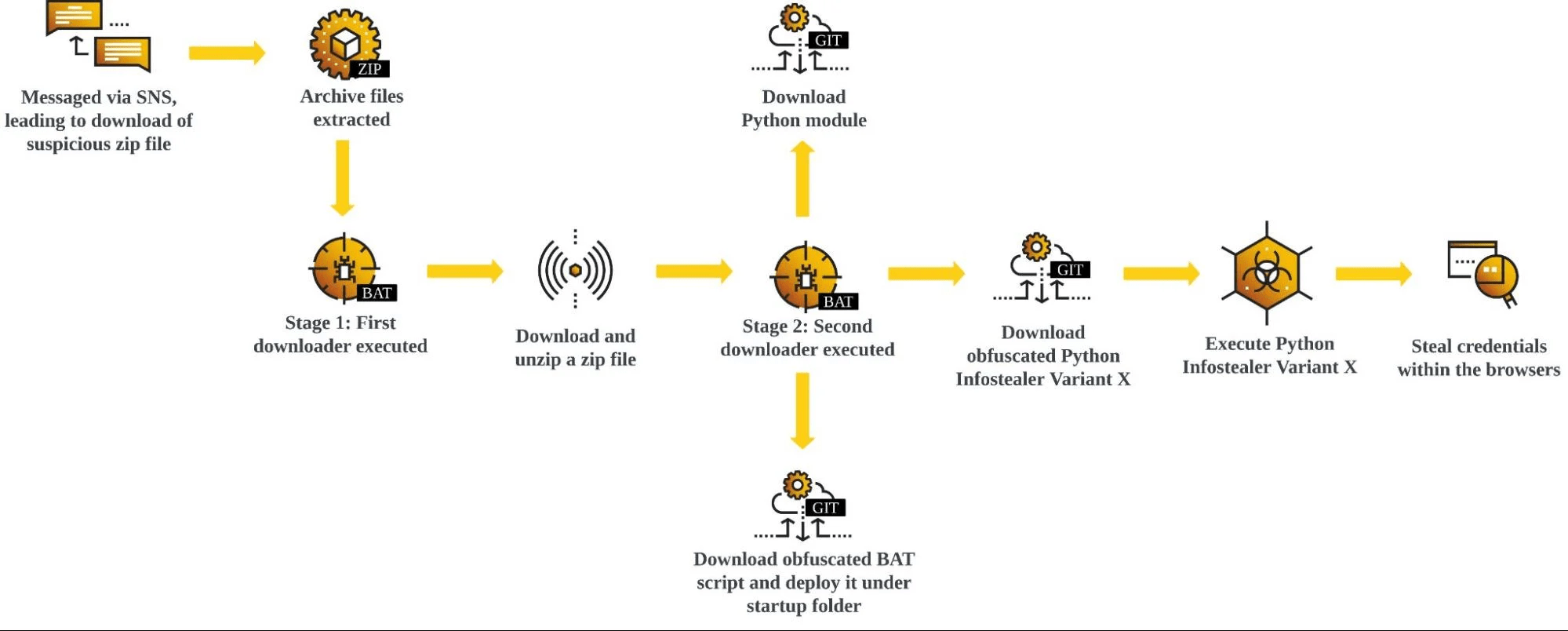
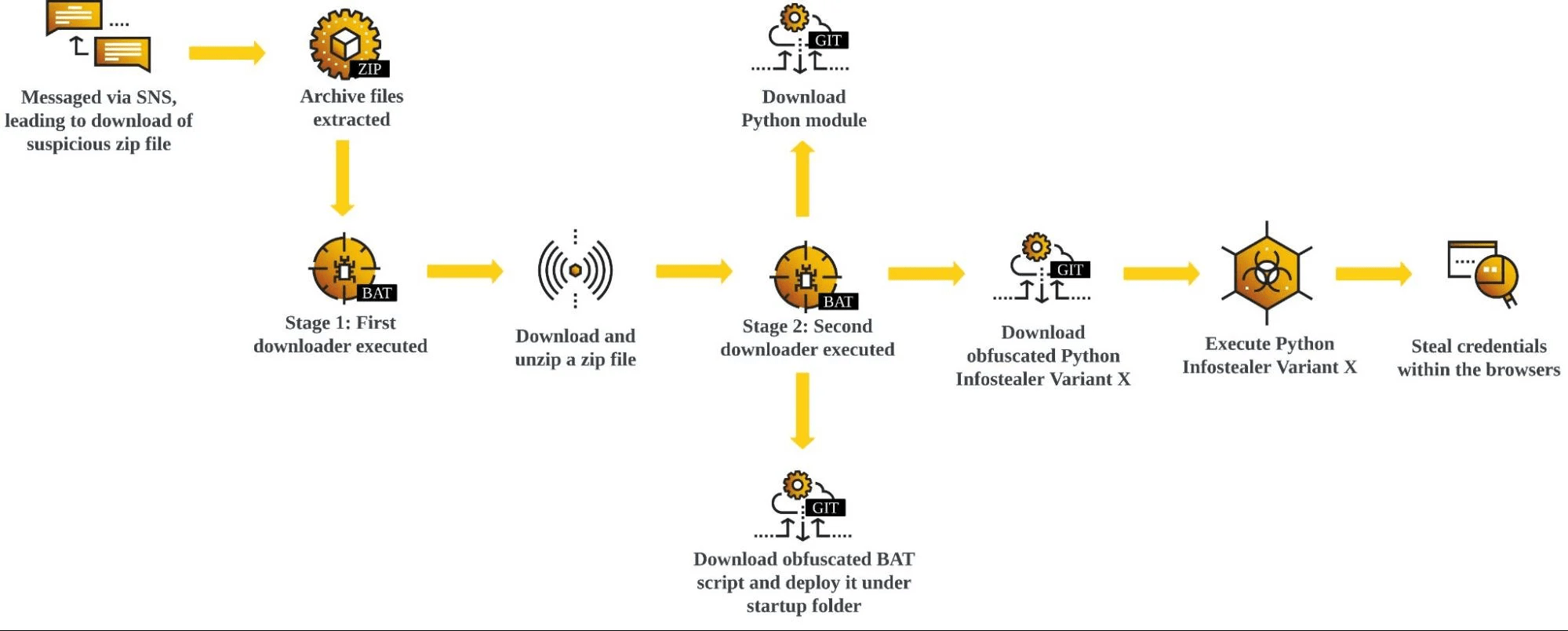
ESET researchers discovered a cyberespionage campaign that, since at least September 2023, has been victimizing Tibetans through a targeted watering hole (also known as a strategic web compromise), and a supply-chain compromise to deliver trojanized installers of Tibetan language translation software. The attackers aimed to deploy malicious downloaders for Windows and macOS to compromise website […]
The company reported annual recurring revenue (ARR) surpassing $100 million and secured investments from major players such as Delta-v Capital, Standard Investments, and Rockwell Automation.
According to the latest Internet Crime Complaint Center (IC3) annual report, digital crimes reported to the FBI in 2023 resulted in potential monetary losses of over $12.5 billion, marking a 22 percent increase from the previous year.
Cisco has released free software updates that address the vulnerability described in this advisory. Customers with service contracts that entitle them to regular software updates should obtain security fixes through their usual update channels. Customers may only install and expect support for software versions and feature sets for which they have purchased a license. By […]
Mar 08, 2024The Hacker NewsSecrets Management / Access Control In the realm of cybersecurity, the stakes are sky-high, and at its core lies secrets management — the foundational pillar upon which your security infrastructure rests. We’re all familiar with the routine: safeguarding those API keys, connection strings, and certificates is non-negotiable. However, let’s dispense with […]