With the surging growth of intelligence available exclusively from publicly or commercially available information, intelligence agencies have been grappling with how to get a better handle on collecting and processing the data. In a new strategy released Friday by the Office of the Director of National Intelligence (ODNI) and the CIA, the agencies said the […]
The Misconfiguration Manager repository provides a comprehensive resource for both offensive professionals and defenders to understand and manage the attack path related to Microsoft Configuration Manager (MCM), formerly known as SCCM.
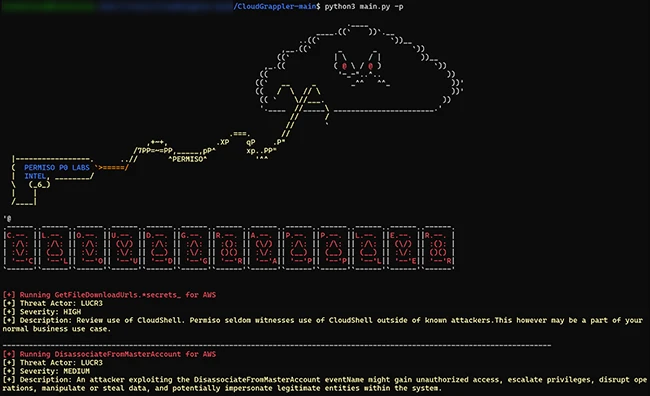
CloudGrappler is an open-source tool designed to assist security teams in identifying threat actors within their AWS and Azure environments. The tool, built on the foundation of Cado Security’s cloudgrep project, offers enhanced detection capabilities based on the tactics, techniques, and procedures (TTPs) of modern cloud threat actors like LUCR-3 (Scattered Spider). CloudGrappler queries for […]
Mar 12, 2024The Hacker NewsCryptocurrency / Cybercrime Threat hunters have discovered a set of seven packages on the Python Package Index (PyPI) repository that are designed to steal BIP39 mnemonic phrases used for recovering private keys of a cryptocurrency wallet. The software supply chain attack campaign has been codenamed BIPClip by ReversingLabs. The packages were […]
The company initially took some systems offline to contain the breach. Although the nature of the incident was not immediately disclosed, LockBit ransomware claimed responsibility for the attack.
Endpoint Security , Governance & Risk Management , Information Sharing GAO Report Criticizes CISA’s Info Sharing Programs for Critical Infrastructure Prajeet Nair (@prajeetspeaks) • March 11, 2024 The U.S. Government Accountability Office has found inefficiencies in the Cybersecurity and Infrastructure Security Agency’s information-sharing practices with critical infrastructure stakeholders – warning that the agency […]
Mar 12, 2024The Hacker NewsCTEM / Vulnerability Management In a world of ever-expanding jargon, adding another FLA (Four-Letter Acronym) to your glossary might seem like the last thing you’d want to do. But if you are looking for ways to continuously reduce risk across your environment while making significant and consistent improvements to security posture, […]
A number of French government agencies have been hit by “intense” cyberattacks, the prime minister’s office announced on Monday. The nature of the attacks, which began on Sunday night, has not been confirmed although the description is consistent with distributed-denial-of-service (DDoS) attacks. The French government said the attack was “conducted using familiar technical means but […]
Tuta Mail has introduced TutaCrypt, a new post-quantum encryption protocol to safeguard communications from anticipated decryption attacks, offering strong protection against future threats.