Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development Firms Get $1 Million Funding to Develop System to Automatically Fix AI Bugs Rashmi Ramesh (rashmiramesh_) • March 12, 2024 The Defense Advanced Research Projects Agency awarded seven small businesses contracts to develop a cyber reasoning system. (Image: Shutterstock) The United States […]
A malicious campaign has been observed exploiting the blockchain-based Meson service for illicit gains ahead of the crypto token unlock planned for March 15. The campaign, discovered by the Sysdig Threat Research Team (TRT), saw an attacker swiftly create 6000 Meson Network nodes using a compromised cloud account, setting off alarms for multiple AWS users […]
While 70% of organizations feel their current security stacks are effective against image-based and QR code phishing attacks, 76% were still compromised in the last 12 months, according to IRONSCALES and Osterman Research. IT pros are highly aware of emerging types of phishing attacks 93% of IT and security professionals are aware of image-based phishing […]
The attacker, known as ‘ph1ns’, leaked the stolen database on a hacking forum. Acer acknowledged the breach and stated that the compromised data was not acquired directly from their systems.
This month’s best new releases include another Buchla reissue from Tiptop Audio, ALM’s compact utility module and a unique oscillator from EarthQuaker Devices. Buchla/Tiptop Audio Mixer/Preamplifier 207t Tiptop’s reissue of the Buchla 207 mixer sticks closely to the quirky format of the 1970s original. It’s a stereo design with six mono inputs, each of which […]
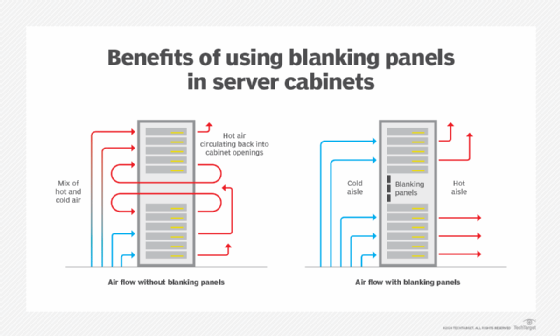
Advancements in modern data center operations lead to new capabilities and management challenges. Recent changes to modern data center standards and design maximize both operational and energy efficiency. The modern data center is far more sophisticated than its predecessors. With proper maintenance and management, today’s data centers can support new generations of hardware for years […]
The LockBit ransomware gang said it was behind an attack on South Africa’s government workers pension fund last month, which has hampered the organization’s operations and disrupted pension payments. The South African Government Pensions Administration Agency (GPAA) manages the money within the Government Employees Pension Fund (GEPF) — the largest pension fund in Africa — […]
Mar 13, 2024The Hacker NewsSaaS Security / Webinar Identities are the latest sweet spot for cybercriminals, now heavily targeting SaaS applications that are especially vulnerable in this attack vector. The use of SaaS applications involves a wide range of identities, including human and non-human, such as service accounts, API keys, and OAuth authorizations. Consequently, any […]
Company Has 20 Days to Disclose Details on Data Used for Training the AI System Akshaya Asokan (asokan_akshaya) • March 11, 2024 The Sora response to the prompt “instructional cooking session for homemade gnocchi hosted by a grandmother social media influencer set in a rustic Tuscan country kitchen with cinematic lighting.” The Italian […]