Security researchers have uncovered critical security flaws within ChatGPT plugins. By exploiting these flaws, attackers could seize control of an organization’s account on third-party platforms and access sensitive user data, including Personal Identifiable Information (PII). “The vulnerabilities found in these ChatGPT plugins are raising alarms due to the heightened risk of proprietary information being stolen […]
The VCURMS RAT uses a Proton Mail email address for communicating with a command-and-control server and can extract and execute commands from specific subject lines in emails.
Hard to spell – but easy to listen to Nick Bourne Onomatopoeia Records started life as a home for the music of former Cardiacs member William D Drake but has grown into one stop shop for some of the most adventurous, idiosyncractic and generally brilliant songwriting happening in the UK right now. Nick Bourne, owner […]
A cyberattack has disrupted operations at one of the world’s biggest boat sellers, the company said in regulatory filings this week. MarineMax, which calls itself the world’s largest recreational boat, yacht, and superyacht services company, filed documents with the Securities and Exchange Commission on Tuesday afternoon describing the incident, which began Sunday. “MarineMax determined… that […]
A report by Red Canary highlighted that cloud account compromises using the MITRE ATT&CK technique T1078.004 surged to the fourth most prevalent technique used by threat actors, impacting three times as many organizations compared to 2022.
The hills are alive – with the sound of “techno“ Founder of the impeccable Art-Aud label, DJ and producer Kreggo evidently likes to keep busy. The label is preparing to celebrate its tenth birthday at the end of 2024, having many of its founder’s intricate, detailed but atmospheric techno productions and tons of other artists […]
Technical Analysis The following analysis covers the technical characteristics of Case Study 1 and Case Study 2 for Tweaks. Case Study 1 1. BAT files establish webhooks: To start, once the user downloads the BAT file and executes it, the malware establishes the necessary webhook URLs using the Powershell commands below: “$payload = [PSCustomObject]@{ embeds […]
General Data Protection Regulation (GDPR) , Governance & Risk Management , Privacy Court Decision Backs 3-Month Ban Imposed by the Country’s Data Regulator Akshaya Asokan (asokan_akshaya) • March 12, 2024 Image: Shutterstock The Spanish High Court on Monday sided with the country’s data regulator to uphold a three-month ban on OpenAI founder Sam […]
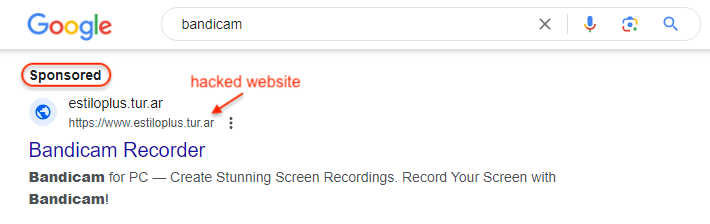
February was a particularly busy month for search-based malvertising with the number of incidents we documented almost doubling. We saw similar payloads being dropped but also a few new ones that were particularly good at evading detection. One malware family we have been tracking on this blog is FakeBat. It is very unique in that […]