Sep 21, 2023The Hacker NewsSaaS Security / App Security Security teams are familiar with threats emanating from third-party applications that employees add to improve their productivity. These apps are inherently designed to deliver functionality to users by connecting to a “hub” app, such as Salesforce, Google Workspace, or Microsoft 365. Security concerns center on the […]
Technology company Microsoft has revealed that it suffered a data leak in July 2020 which exposed 38 terabytes of private employee data. News of the leak was made public via a blog post on September 18. In it, Microsoft explained that the leak was caused by a software misconfiguration. The company shared that the misconfiguration […]
The British government’s controversial Online Safety Bill finally completed its passage through parliament on Tuesday, marking the end of one of the most (if not the most) fraught episodes in the United Kingdom’s recent legislative history. The origin and intention of the new law — which began three prime ministers and seven secretaries of state […]
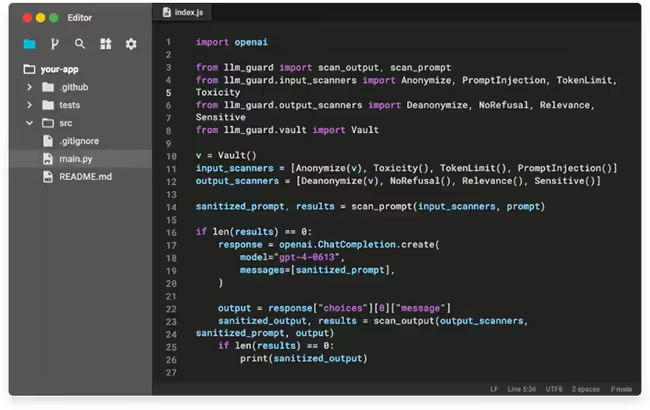
LLM Guard is a toolkit designed to fortify the security of Large Language Models (LLMs). It is designed for easy integration and deployment in production environments. It provides extensive evaluators for both inputs and outputs of LLMs, offering sanitization, detection of harmful language and data leakage, and prevention against prompt injection and jailbreak attacks. LLM […]
Sep 21, 2023THNCyber Espionage / Spyware China’s Ministry of State Security (MSS) has accused the U.S. of breaking into Huawei’s servers, stealing critical data, and implanting backdoors since 2009, amid mounting geopolitical tensions between the two countries. In a message posted on WeChat, the government authority said U.S. intelligence agencies have “done everything possible” to […]
According to user reports on social media, the exposed information included customers’ names, phone numbers, addresses, account balances, and credit card details like the expiration dates and the last four digits.
Australia is rolling out a six-pillar cyber security strategy to safeguard its digital interests, covering education, technology safety, threat-sharing, infrastructure protection, infosec capability, and global coordination.
Sep 21, 2023THNCyber Threat / Ransomware A financially motivated threat actor has been outed as an initial access broker (IAB) that sells access to compromised organizations for other adversaries to conduct follow-on attacks such as ransomware. SecureWorks Counter Threat Unit (CTU) has dubbed the e-crime group Gold Melody, which is also known by the names […]
The investigation into the claims found that the information leaked by USDoD was likely obtained from another organization’s systems, given that the data and its formatting are different than TransUnion’s.