The Royal ransomware group intruded Dallas’ systems and surveilled and exfiltrated data for a month before it initiated a ransomware attack that threw city operations into disarray last spring, the city said Wednesday in a post-attack report. The prolific ransomware group, which was linked to a spree of attacks in the Dallas metro area, established […]
Researchers at SentinelOne have noticed a potential cyberespionage group, whose origins are unclear (as of now), and employed modular backdoors and covert techniques to target telecommunication firms in the Middle East, Western Europe, and South Asia. This group, labeled Sandman APT, utilizes a new backdoor named LuaJIT, which is a just-in-time compiler for the Lua […]
Berlin-based French producer’s debut LP out next month pic: Ulrike Rindermann Fantastic Twins aka Julienne Dessagne unveils her new single ‘Land of Pleasure Hi Fi’ today, complete with a mindbendingly weird promo film. The single is taken from the from the Berlin-based French producer, musician and vocalist’s forthcoming debut album Two Is Not a Number, out […]
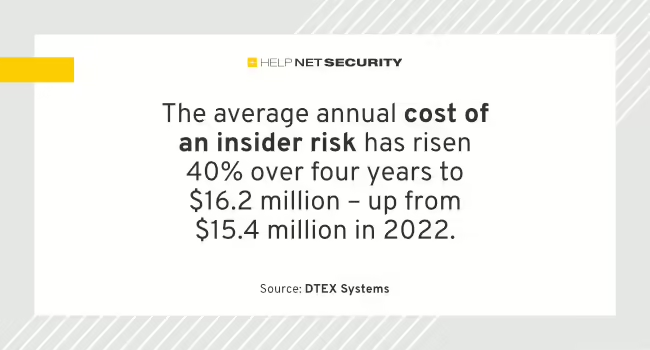
The cost of an insider risk is the highest it’s ever been, as organizations spend more time than ever trying to contain insider incidents, according to DTEX Systems. The average annual cost of an insider risk has increased to $16.2 million – a 40% increase over four years. Meanwhile, the average number of days to […]
Encrypted SSDs have existed for more than a decade, but many end users and some sys admins don’t fully understand them. Most SSDs are self-encrypting drives (SEDs) that support internal encryption. However, there are various levels of encryption, reasons for using it and vendors that supply it, so organizations have a lot to consider. How […]
SOC 2, ISO, HIPAA, Cyber Essentials – all the security frameworks and certifications today are an acronym soup that can make even a compliance expert’s head spin. If you’re embarking on your compliance journey, read on to discover the differences between standards, which is best for your business, and how vulnerability management can aid compliance. […]
Sep 26, 2023THNMobile Security / Malware An updated version of an Android banking trojan called Xenomorph has set its sights on more than 35 financial institutions in the U.S. The campaign, according to Dutch security firm ThreatFabric, leverages phishing web pages that are designed to entice victims into installing malicious Android apps that target a […]
Despite some positive developments, the impact of ransomware attacks remains high, according to SpyCloud. Infostealer infections preceded 22% of ransomware events for North American and European ransomware victim companies in 2023 – with common infostealers such as Raccoon, Vidar, and Redline increasing the probability even further. SpyCloud’s analysis shows that 76% of infections that preceded […]
How To Use This Report Enhance situational awareness of techniques used by threat actors Identify potential attacks targeting your industry Gain insights to help improve and accelerate your organization’s threat response Summary of Findings The Network Effect Threat Report offers insights based on unique data from Fastly’s Next-Gen WAF from Q2 2023 (April 1, 2023 […]