Star Blizzard has targeted academia, defense, governmental organizations and politicians with spear phishing campaigns
Our final modular round-up of the year includes a monster synth voice from Jomox, digital creativity from Xaoc and a typically slick reverb from Erica Synths. Jomox Mod FM Despite being best known for their outstanding drum machines, German veterans Jomox’s synth offerings should never be overlooked. The Mod FM is a module which has […]
BlackCat/ALPHV ransomware group leaked photos of what appears to be stolen passports, contact lists, emails and confidential documents
Dive Brief: Progress Software disclosed two new high-severity vulnerabilities in the beleaguered MOVEit file-transfer service last week. A privilege escalation path vulnerability, CVE-2023-6218, and a cross-site scripting vulnerability, CVE-2023-6217, were disclosed and patched Nov. 29. The additional set of vulnerabilities brings the total number of CVEs in MOVEit to eight since a zero-day vulnerability, CVE-2023-34362, […]
Dec 08, 2023NewsroomEndpoint Security / Malware Unauthorized websites distributing trojanized versions of cracked software have been found to infect Apple macOS users with a new Trojan-Proxy malware. “Attackers can use this type of malware to gain money by building a proxy server network or to perform criminal acts on behalf of the victim: to launch […]
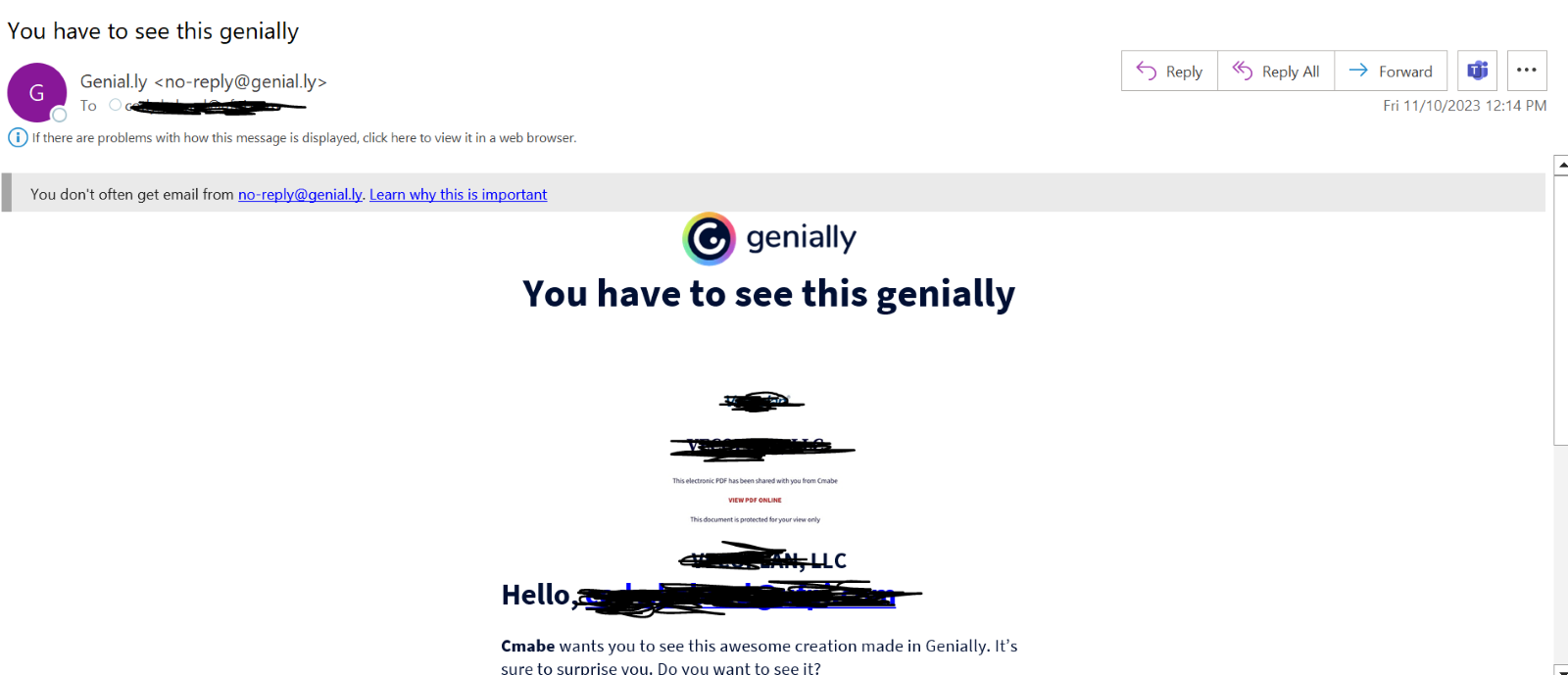
This malware is a Python-based information stealer compressed with cx-Freeze to evade detection. MrAnon Stealer steals its victims’ credentials, system information, browser sessions, and cryptocurrency extensions.
Dec 08, 2023NewsroomVulnerability / Website Security WordPress has released version 6.4.2 with a patch for a critical security flaw that could be exploited by threat actors by combining it with another bug to execute arbitrary PHP code on vulnerable sites. “A remote code execution vulnerability that is not directly exploitable in core; however, the security […]
This vulnerability could allow attackers to run arbitrary PHP code on a target website. The vulnerability is a Property Oriented Programming (POP) chain that requires an attacker to control all the properties of a deserialized object.