Both Advanced Micro Devices and Google released AI accelerators today: AMD the Instinct MI300 and Google TPU v5e. Both are data center-grade processors that speed AI tasks, such as training large language models. AMD is playing catch-up to Nvidia, which has parleyed its gaming tech expertise into an AI processing superpower. AI typically runs on […]
Just three US federal agencies have reached the required cyber security incident response standards
Security incidents are being triggered by employees using messaging apps in business environments
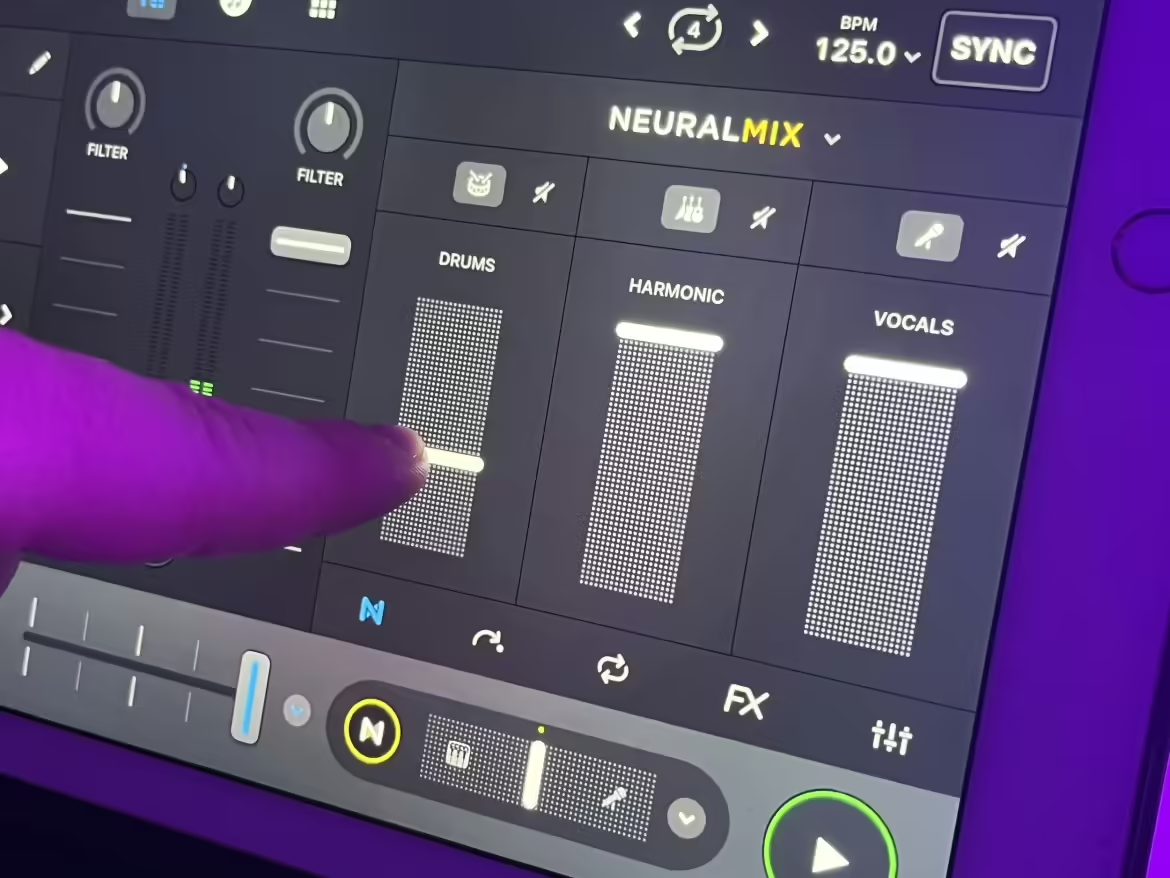
Last updated 6 December, 2023 Algoriddim has unveiled djay Pro 5, the latest update to its DJ software suite for iOS, iPadOS, and macOS. This version introduces a much more sophisticated AI music separation technology, developed in partnership with AudioShake. The new Neural Mix allows DJs to isolate vocals and instruments with unprecedented speed in […]
For years, one of the biggest powerhouses in the DJ software world has been Algoriddim. With their djay and djay Pro softwares, they took their Apple and iOS-centric design prowess and fed it directly into innovation and new features. They were among the first to bring real-time stem separation to DJ software while others were […]
Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Geo Focus: Asia Andariel Group Rented Server to Steal 1.2TB of Data, Extort $357,000 in Ransoms Jayant Chakravarti (@JayJay_Tech) • December 5, 2023 A Seoul Metropolitan Police Agency police station (Image Shutterstock) Seoul police have accused the North Korean hacker group Andariel of […]
Israeli startup Mine made a name for itself a few years ago with a tool designed for consumers to quickly run an audit of their data privacy situation. One scan of your inbox using AI and specifically natural language processing, and Mine can triangulate which companies have access to your personal data, and then let […]
Dec 06, 2023NewsroomAccess Management / Cloud Security Threat actors can take advantage of Amazon Web Services Security Token Service (AWS STS) as a way to infiltrate cloud accounts and conduct follow-on attacks. The service enables threat actors to impersonate user identities and roles in cloud environments, Red Canary researchers Thomas Gardner and Cody Betsworth said […]
Admins are advised to upgrade to the latest ALEOS version, change default SSL certificates, disable non-essential services, implement web application firewalls, and install an OT/IoT-aware IDS for enhanced protection against these vulnerabilities.