A dependency confusion vulnerability has been found within an archived Apache project. According to new data by Legit Security, who made the discovery, the finding underscores the importance of scrutinizing third-party projects and dependencies, particularly those archived and potentially neglected in terms of updates and security patches. The technical post, published today, suggests that despite […]
Apr 12, 2024The Hacker NewsDevSecOps / Identity Management Identities now transcend human boundaries. Within each line of code and every API call lies a non-human identity. These entities act as programmatic access keys, enabling authentication and facilitating interactions among systems and services, which are essential for every API call, database query, or storage account access. […]
Security researchers have uncovered critical security flaws within ChatGPT plugins. By exploiting these flaws, attackers could seize control of an organization’s account on third-party platforms and access sensitive user data, including Personal Identifiable Information (PII). “The vulnerabilities found in these ChatGPT plugins are raising alarms due to the heightened risk of proprietary information being stolen […]
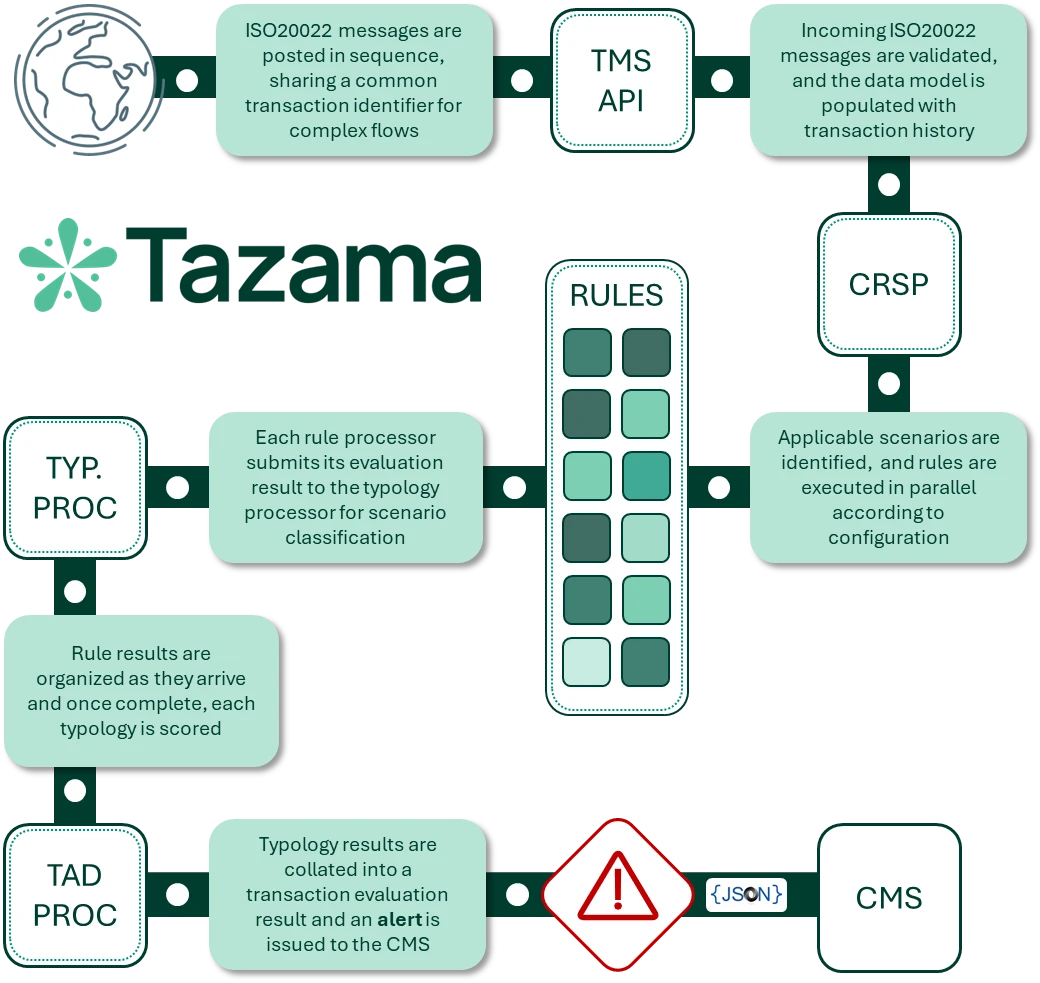
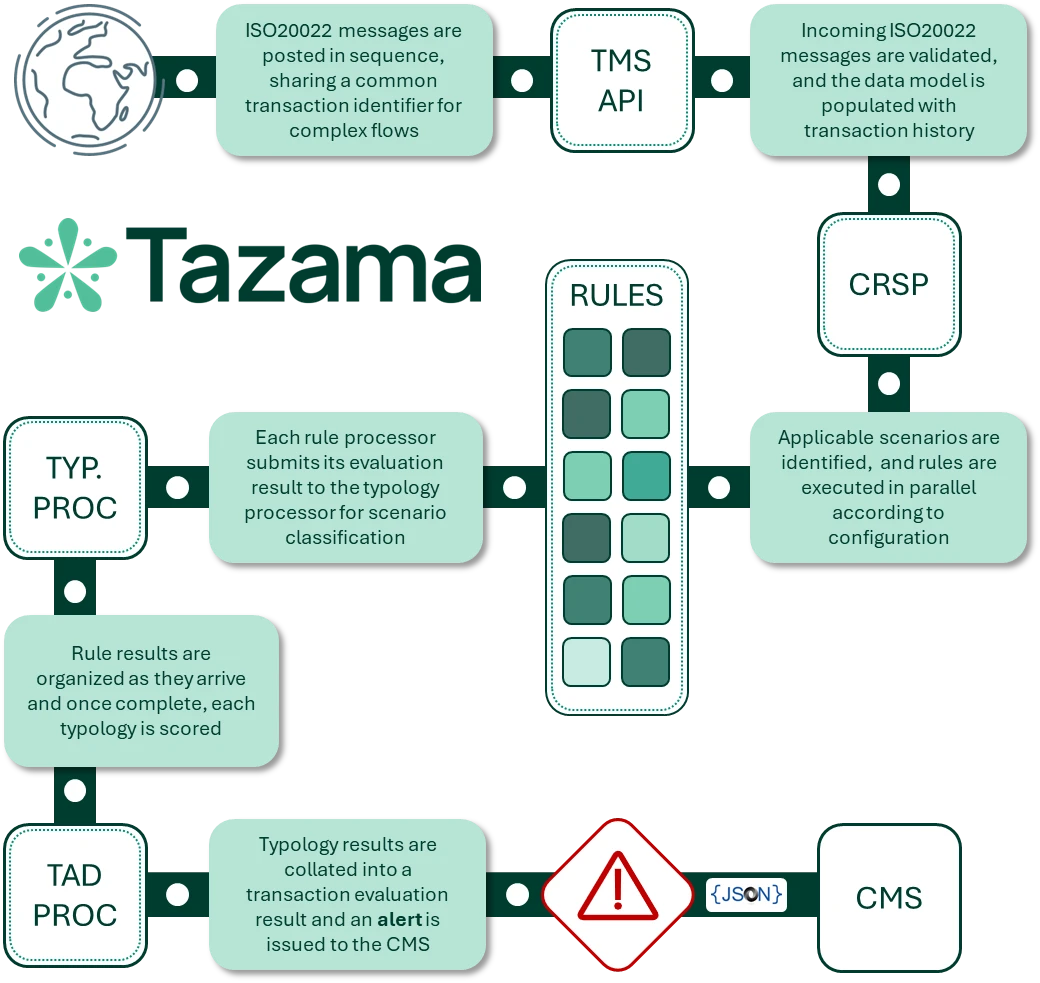
Tazama is an open-source platform focused on improving fraud management within digital payment systems. Tazama marks a substantial transformation in the approach to financial monitoring and compliance worldwide. Previously, the financial sector struggled with proprietary solutions that were both expensive and restrictive, impeding access and flexibility, particularly in developing economies. Tazama challenges this status quo […]
Tazama is an open-source platform focused on improving fraud management within digital payment systems. Tazama marks a substantial transformation in the approach to financial monitoring and compliance worldwide. Previously, the financial sector struggled with proprietary solutions that were both expensive and restrictive, impeding access and flexibility, particularly in developing economies. Tazama challenges this status quo […]
Orca has discovered three new vulnerabilities within various Azure HDInsight third-party services, including Apache Hadoop, Spark, and Kafka. These services are integral components of Azure HDInsight, a widely used managed service offered within the Azure ecosystem. Two of the vulnerabilities could have led to Privilege Escalation (PE) and one could have been used to cause […]
Feb 05, 2024The Hacker NewsData Protection / Threat Intelligence A significant challenge within cyber security at present is that there are a lot of risk management platforms available in the market, but only some deal with cyber risks in a very good way. The majority will shout alerts at the customer as and when they […]
Adalanche provides immediate insights into the permissions of users and groups within an Active Directory. It’s an effective open-source tool for visualizing and investigating potential account, machine, or domain takeovers. Additionally, it helps identify and display any misconfigurations. What unique features make Adalanche stand out? “The best feature is the low user effort to get […]
Microsoft will store all cloud customers’ personal data within the European Union rather than allowing transfers abroad, the company said on Thursday — the latest step in ongoing efforts by cloud providers to navigate varying privacy regulations across jurisdictions. Under the new policy, Microsoft will keep within what it calls the “EU data boundary” all […]