Ledger users are advised to avoid using web3 dApps following a supply chain attack on the Ledger dApp Connect Kit library, which resulted in the theft of $600,000 worth of crypto and NFTs.
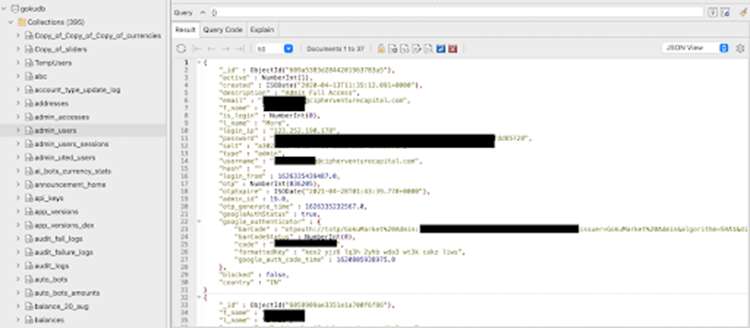
Data of over a million users of the crypto exchange GokuMarket exposed Pierluigi Paganini December 15, 2023 GokuMarket, a centralized crypto exchange owned by ByteX, left an open instance, revealing the details of virtually all of its users, the Cybernews research team has discovered. The leak comes after the team discovered an unprotected MongoDB instance, […]
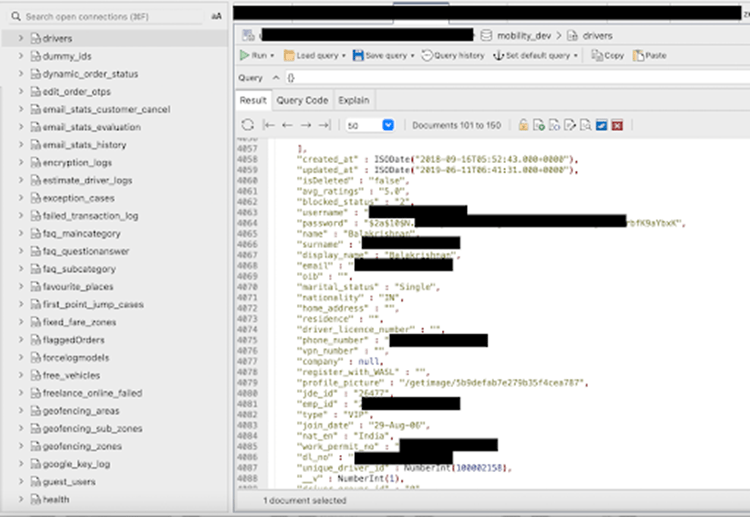
Dubai’s largest taxi app exposes 220K+ users Pierluigi Paganini December 12, 2023 The Dubai Taxi Company (DTC) app, which provides taxi, limousine, and other transport services, left a database open to the public, exposing sensitive customer and driver data. Dubai Taxi Company, a subsidiary of Dubai’s Roads and Transport Authority, leaked a trove of sensitive […]
SOPA Images/Getty Images Just when Chrome desktop users thought they could take a breather, it’s time for yet another update — this one with a host of security fixes. Chrome version 120 is now officially available for Windows, Mac, and Linux, and you’ll want to install this one if only to get all 10 bug […]
Microsoft will not abandon Windows 10 users to an insecure fate once it reaches end of support (EOS) on October 14, 2025: both enterprises and individual consumers will be able receive Extended Security Updates (ESU), but will have to pay for them. Details about the Windows 10 ESU program “The ESU program enables PCs to […]
Last updated 5 December, 2023 Users of Denon DJ and Numark’s standalone equipment can now download Engine DJ 3.3, the latest version of the embedded software for their DJ gear that brings a whole host of new features. As well as profiles allowing a single login for all services and enabling cloud BPM and key […]
What is a shell program? A shell program is software that provides users with an interface for accessing services in the kernel. The kernel manages the operating system’s (OS) core services. It’s a highly protected and controlled space that limits access to the system’s resources. A shell provides an intermediary connection point between the user […]
Due to the incident, users may experience difficulties accessing Blender’s services and sites, and should be cautious of downloading from third-party sources to avoid malware infections.
Android smartphone users in India are the target of a new malware campaign that employs social engineering lures to install fraudulent apps that are capable of harvesting sensitive data. “Using social media platforms like WhatsApp and Telegram, attackers are sending messages designed to lure users into installing a malicious app on their mobile device by […]