The FTC is sending $5.6 million in refunds to Ring users whose private video feeds were accessed without consent by Amazon employees and contractors, or had their accounts and devices hacked because of insufficient security protections.
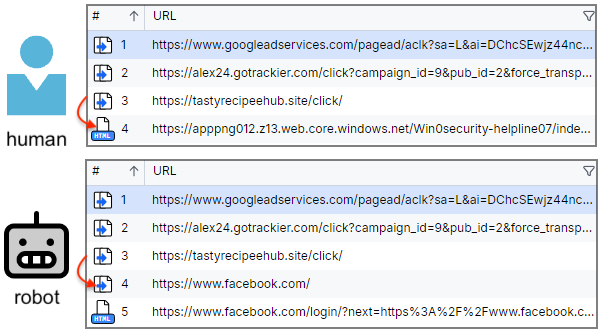
Today, we are looking at a malicious ad campaign targeting Facebook users via Google search. It is well-known that tech support scammers attract new victims by buying ads for certain keywords related to their audience. What is perhaps less known is how it is even possible to impersonate top brands and get away with it. […]
Similar to a recently reported issue in GitHub, users can abuse the “comments” feature in GitLab to upload malware to any repository without the repository owner’s knowledge.
Users started noticing on Monday that X’s programmers implemented a rule on its iOS app that auto-changed Twitter.com links that appeared in Xeets (tweets) to X.com links.
Docker has been one of the most popular default container runtime engines for users because of how straightforward it is. However, Red Hat has changed the way it supports running Docker, which causes users to switch to Podman. Security is a speculated reason why Red Hat changed its support for Docker. Podman is a close […]
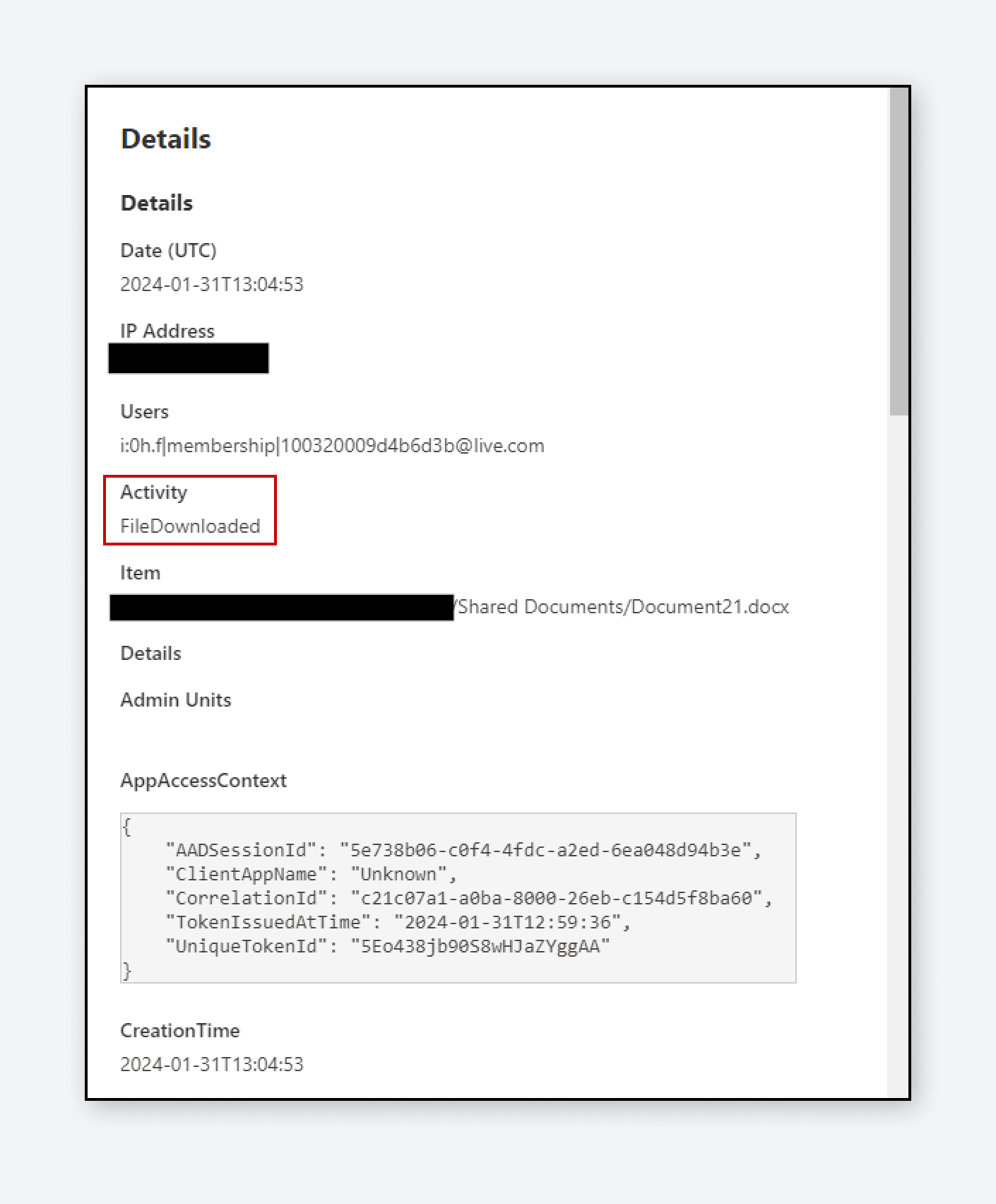
Varonis Threat Labs discovered two techniques in SharePoint that allow users to circumvent audit logs and avoid triggering download events while exfiltrating files. These techniques can bypass the detection and enforcement policies of traditional tools, such as cloud access security brokers, data loss prevention, and SIEMs, by hiding downloads as less suspicious access and sync […]
Minecraft, with over 500 million registered users and 166 million monthly players, faces significant risks from distributed denial-of-service (DDoS) attacks, threatening server functionality, player experience, and the game’s reputation. Despite the prevalence of DDoS attacks on the game, the majority of incidents go unreported, leaving a gap in awareness and protection. This article explains what […]
Being a CISO is a balancing act: ensuring organizations are secure without compromising users’ productivity. This requires taking multiple elements into consideration, like cost, complexity, performance and user experience. CISOs around the globe use Cato SSE 360, as part of the Cato SASE Cloud platform to balance these factors without compromise. This article details how […]
Users in Brazil are the target of a new banking trojan known as CHAVECLOAK that’s propagated via phishing emails bearing PDF attachments. “This intricate attack involves the PDF downloading a ZIP file and subsequently utilizing DLL side-loading techniques to execute the final malware,” Fortinet FortiGuard Labs researcher Cara Lin said. The attack chain involves the […]