Confidential virtual machines could be breached through two different types of novel Ahoi attacks, reports SecurityWeek. Intrusions leveraging the first technique, dubbed “Heckler,” involved the targeting of hardware-based trusted execution environments running on Intel’s Trust Domain Extensions and AMD’s Secure Encrypted Virtualization-Secure Nested Paging technologies with malicious hypervisors that sought to facilitate authentication evasion and […]
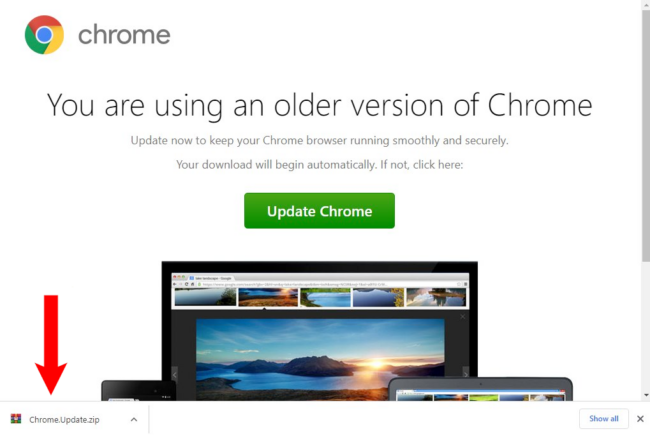
SocGholish malware, otherwise known as “fake browser updates”, is one of the most common types of malware infections that we see on hacked websites. This long-standing malware campaign leverages a JavaScript malware framework that has been in use since at least 2017. The malware attempts to trick unsuspecting users into downloading what is actually a […]
The National Telecommunication Monitoring Centre (NTMC) in Bangladesh has exposed a database to the open web. The types of data that leaked online were extensive, American technology magazine WIRED reports. The list of data is long: names, professions, blood groups, parents’ names, phone numbers, the length of calls, vehicle registrations, passport details and fingerprint photos, […]
AWS said most-privileged users, and eventually more account types, will be required to use multifactor authentication beginning in mid-2024. The move makes the cloud giant the first of the three major hyperscalers to commit to MFA baseline controls by default. “AWS is further strengthening the default security posture of our customers’ environments by requiring the […]
There are many different types of malware in existence and unfortunately the number is increasing year-on-year. According to a report by software company Symantec there were almost 670 million malware variants in 2017, with researchers estimating this has risen to more than 1 billion malware programs today. While the presence of so many malware variants […]