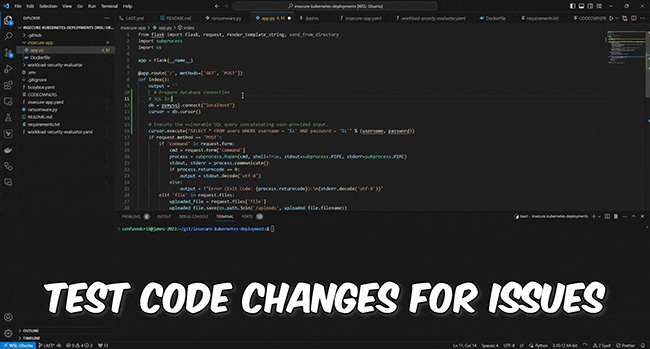
SiCat is an open-source tool for exploit research designed to source and compile information about exploits from open channels and internal databases. Its primary aim is to assist in cybersecurity, enabling users to search the internet for potential vulnerabilities and corresponding exploits. Akas Wisnu Aji, the creator of SiCat, outlined the key features of the […]
Generative AI based on large language models (LLMs) has become a valuable tool for individuals and businesses, but also cybercriminals. Its ability to process large amounts of data and quickly generate results has contributed to its widespread adoption. AI in the hands of cybercriminals According to a report from Abnormal Security, generative AI (GenAI) is […]
Popular remote monitoring and management software company AnyDesk said all versions of its tool obtained from “official sources” are safe to use following a cyberattack that caused days of outages and concern among users. The cyberattack affected servers in Spain and Portugal but nowhere else, AnyDesk said. The company confirmed last Friday that a four-day […]
Latio Application Security Tester is an open-source tool that enables the usage of OpenAI to scan code from the CLI for security and health issues. Features and future plans James Berthoty, the creator of Latio Application Security Tester, told Help Net Security about the unique features that make it stand out: 1. Easily send code […]
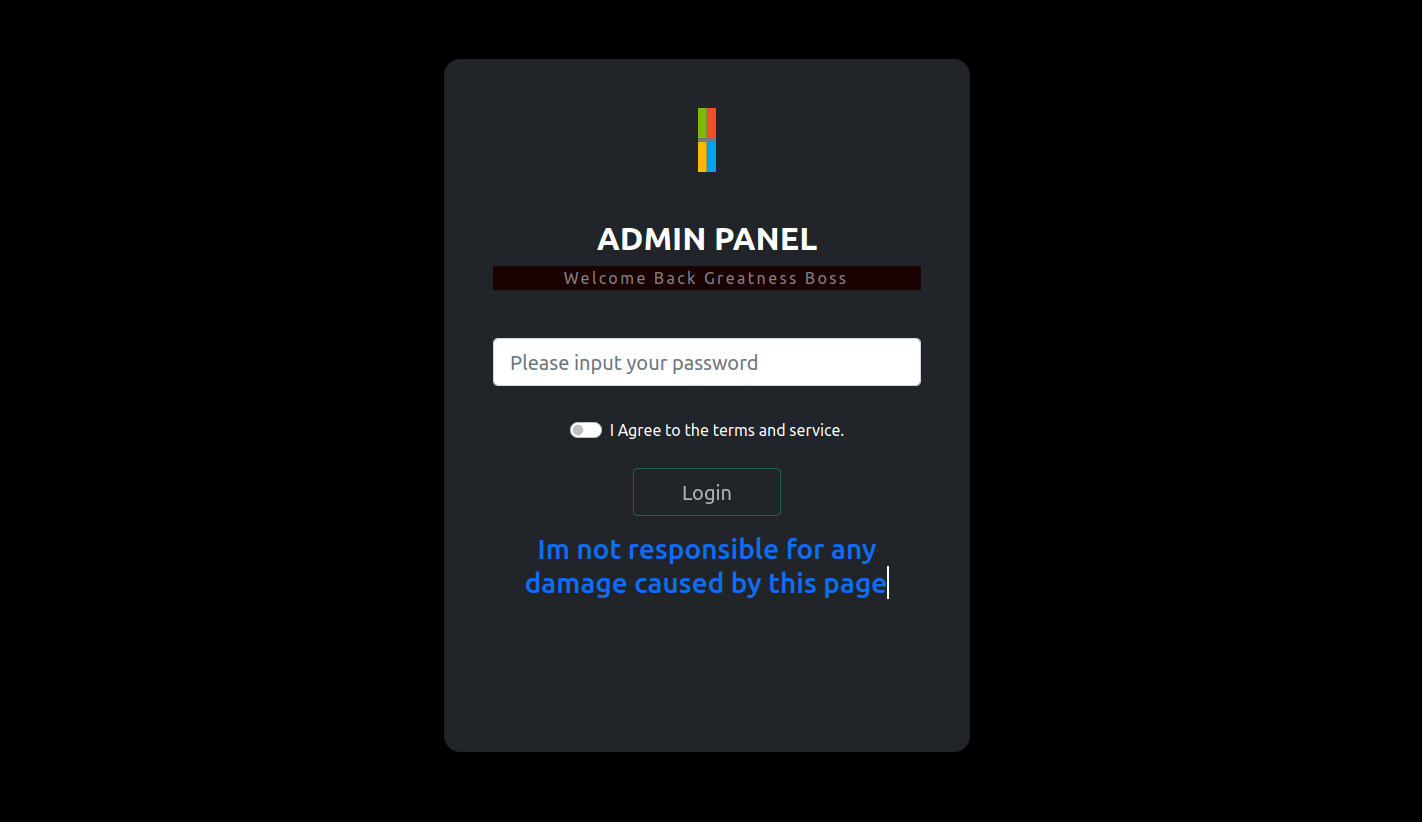
Emerging in 2022, a phishing tool known as Greatness has caught the attention of our research team due to its coordinated efforts to breach Microsoft 365 accounts and presence on compromised websites. More disturbingly, it has shown effectiveness against multi-factor authentication (MFA), elevating the potential threat level. Identified as a Phishing as a Service (PhaaS) […]
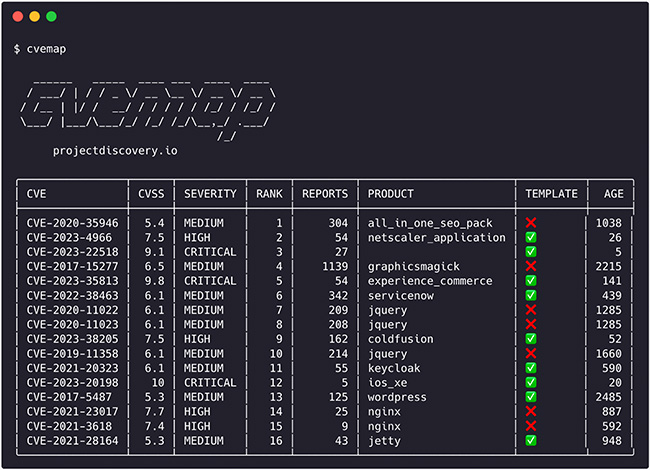
CVEMap is an open-source command-line interface (CLI) tool that allows you to explore Common Vulnerabilities and Exposures (CVEs). It’s designed to offer a streamlined and user-friendly interface for navigating vulnerability databases. Although CVEs are crucial for pinpointing and discussing security weaknesses, their rapid growth and occasional overstatement of severity often result in misleading information. Security […]
Jan 11, 2024NewsroomCloud Security / Cyber Attacks A new Python-based hacking tool called FBot has been uncovered targeting web servers, cloud services, content management systems (CMS), and SaaS platforms such as Amazon Web Services (AWS), Microsoft 365, PayPal, Sendgrid, and Twilio. “Key features include credential harvesting for spamming attacks, AWS account hijacking tools, and functions […]
AuthLogParser is an open-source tool tailored for digital forensics and incident response, specifically crafted to analyze Linux authentication logs (auth.log). The tool examines the auth.log file, extracting crucial details like SSH logins, user creations, event names, IP addresses, among others. It produces a concise summary that offers a clear overview of the activities documented in […]
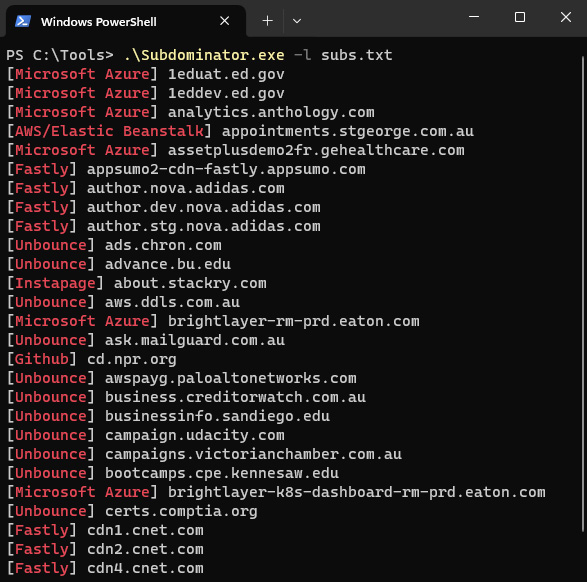
Subdominator is a dependable and fast open-source command-line interface tool to identify subdomain takeovers. It boasts superior accuracy and reliability, offering improvements compared to other tools. “Initially, Subdominator was created internally because all the current subdomain takeover tools had gaps in their functionality. No tool had a complete set of accurate service fingerprints or features. […]