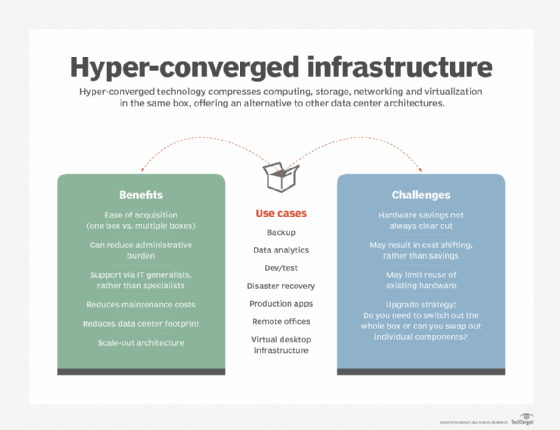
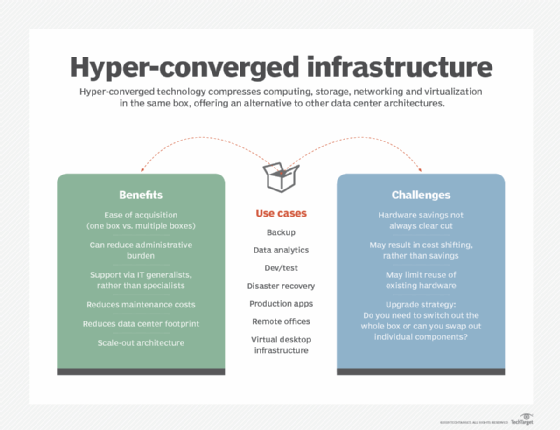
Hyper-converged infrastructure technology has taken big strides since emerging more than a decade ago, finding a home in data centers looking to ease procurement headaches and management chores. Vendors originally positioned the technology as a simple-to-deploy, all-in-one offering that combined compute, storage and networking with a hypervisor. The essential selling points around simplicity remain the […]
Hyper-converged infrastructure technology has taken big strides since emerging more than a decade ago, finding a home in data centers looking to ease procurement headaches and management chores. Vendors originally positioned the technology as a simple-to-deploy, all-in-one offering that combined compute, storage and networking with a hypervisor. The essential selling points around simplicity remain the […]
Hyper-converged infrastructure technology has taken big strides since emerging more than a decade ago, finding a home in data centers looking to ease procurement headaches and management chores. Vendors originally positioned the technology as a simple-to-deploy, all-in-one offering that combined compute, storage and networking with a hypervisor. The essential selling points around simplicity remain the […]
What makes one ransomware victim more likely to pay up than another? That’s what one Dutch researcher set out to find, analyzing national police and incident response data on hundreds of cases over the last four years. Companies that work with a third-party incident response firm are the most willing to pay their extortionists, he […]
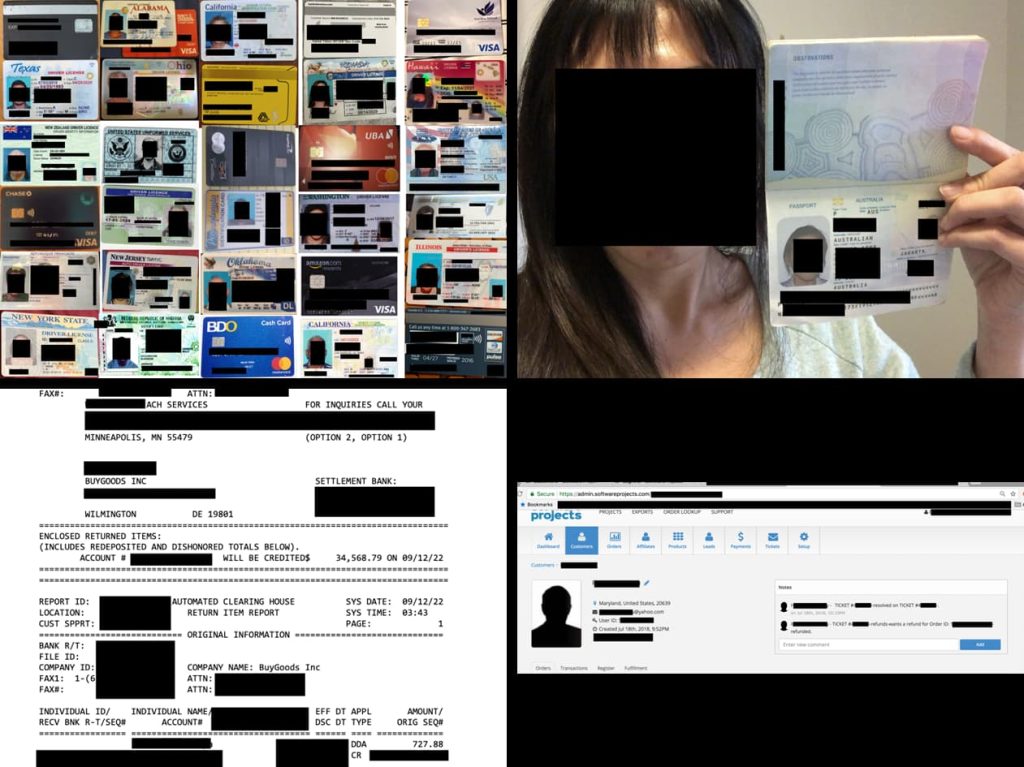
The staggering 198.3 gigabytes of misconfigured database contained more than 260,000 records including customer selfies with unredacted credit cards. Cybersecurity researcher Jeremiah Fowler recently uncovered a misconfigured cloud database that had left a wealth of sensitive data exposed. The affected database contained records attributed to customers of BuyGoods.com, alternatively recognized in the industry as Softwareproject. […]
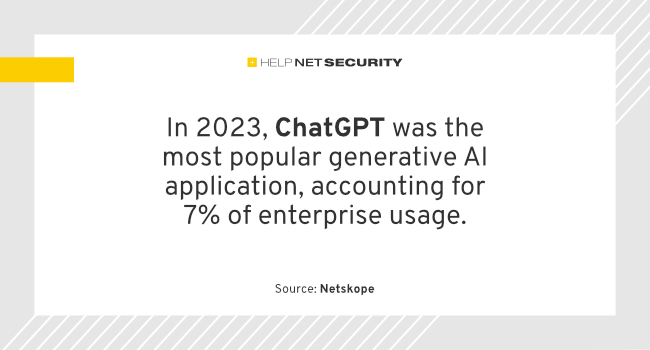
More than 10% of enterprise employees access at least one generative AI application every month, compared to just 2% a year ago, according to Netskope. In 2023, ChatGPT was the most popular generative AI application, accounting for 7% of enterprise usage. While Netskope expects the total number of users accessing AI apps in the enterprise […]
Picture a cybersecurity landscape where defenses are impenetrable, and threats are nothing more than mere disturbances deflected by a strong shield. Sadly, this image of fortitude remains a pipe dream despite its comforting nature. In the security world, preparedness is not just a luxury but a necessity. In this context, Mike Tyson’s famous adage, “Everyone […]
Distributed denial of service attacks hit an all-time high in 2023, more than doubling year over year in the fourth quarter, Cloudflare said Tuesday in a threat report. The record high year for DDoS attacks coincided with mass exploits of the novel zero-day vulnerability HTTP/2 Rapid Reset, which threat actors used to launch DDoS attacks […]
Hot in more ways than one Adham Zahran Anyone even vaguely familiar with Egypt’s traditional music, big on sultry atmospheres and always arranged around big, brash rhythms, will not be surprised to hear the ancient country is a key one to watch for emerging electronic artists. It’s in their musical DNA. Acts like 3Phaz, whose […]