Endpoint Security , Governance & Risk Management , Patch Management Gateway Maker Says Technique Won’t Succeed in Live Customer Environment Mihir Bagwe (MihirBagwe) • March 1, 2024 Ivanti disputes that hackers in a production environment can establish persistence after a factory reset. (Image: Shutterstock) Corporate VPN maker Ivanti disputed findings by the U.S. […]
Tomer Nahum and Eric Woodruff Key findings Golden SAML, an attack technique that exploits the SAML single sign-on protocol, was used as a post-breach exploit, compounding the devastating SolarWinds attack of 2020—one of the largest breaches of the 21st century. The supply chain SolarWinds attack affected thousands of organizations around the world, including the U.S. […]
Feb 29, 2024NewsroomThreat Intelligence / Cyber Threat Cybersecurity researchers have disclosed a new attack technique called Silver SAML that can be successful even in cases where mitigations have been applied against Golden SAML attacks. Silver SAML “enables the exploitation of SAML to launch attacks from an identity provider like Entra ID against applications configured to […]
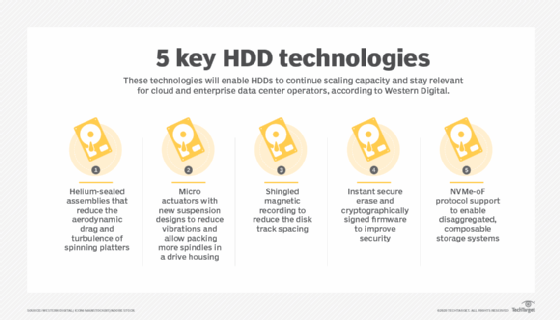
What is shingled magnetic recording (SMR)? Shingled magnetic recording (SMR) is a technique for writing data to a hard disk drive (HDD) whereby the data tracks partially overlap to increase the areal density and overall storage capacity per disk. In SMR HDDs, the term derives from the manner in which shingles are installed on a […]
Jan 03, 2024NewsroomCyber Threat / Email Security A new exploitation technique called Simple Mail Transfer Protocol (SMTP) smuggling can be weaponized by threat actors to send spoofed emails with fake sender addresses while bypassing security measures. “Threat actors could abuse vulnerable SMTP servers worldwide to send malicious emails from arbitrary email addresses, allowing targeted phishing […]
The use of public services as command-and-control (C2) infrastructure isn’t a revolutionary technique for malicious actors. ReversingLabs has observed such behavior in several malware campaigns throughout the last few years. Malware authors occasionally place their samples in services like Dropbox, Google Drive, OneDrive and Discord to host second stage malware and sidestep detection tools. However, […]
Dec 05, 2023NewsroomMobile Security / Spyware A new “post-exploitation tampering technique” can be abused by malicious actors to visually deceive a target into believing that their Apple iPhone is running in Lockdown Mode when it’s actually not and carry out covert attacks. The novel method, detailed by Jamf Threat Labs in a report shared with […]
Nov 15, 2023NewsroomRansomware / Vulnerability Cybersecurity researchers have demonstrated a new technique that exploits a critical security flaw in Apache ActiveMQ to achieve arbitrary code execution in memory. Tracked as CVE-2023-46604 (CVSS score: 10.0), the vulnerability is a remote code execution bug that could permit a threat actor to run arbitrary shell commands. It was […]
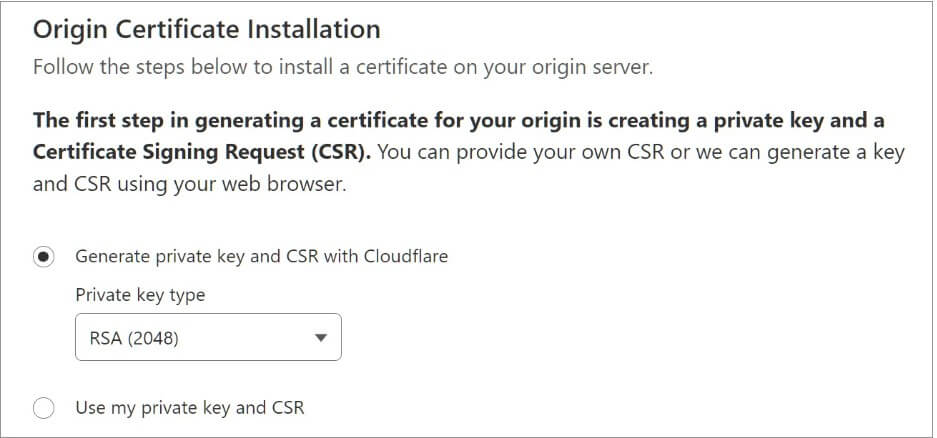
The effectiveness of Cloudflare’s Firewall and DDoS prevention has been proven to be compromised by an attack technique that takes the use of logical vulnerabilities in cross-tenant security policies. This finding has sparked worries about possible vulnerabilities that could damage the security company’s clients. How Does the Cloudflare Attack Work? The attack only requires the creation […]
- 1
- 2