Technical Analysis Strings obfuscation The steps for decrypting a Pikabot string are relatively simple. Each string is decrypted only when required (in other words, Pikabot does not decrypt all strings at once). Pikabot follows the steps below to decrypt a string: Pushes on the stack the encrypted string array. Initializes the RC4 encryption algorithm. The […]
Technical Analysis The following analysis covers the technical characteristics of Case Study 1 and Case Study 2 for Tweaks. Case Study 1 1. BAT files establish webhooks: To start, once the user downloads the BAT file and executes it, the malware establishes the necessary webhook URLs using the Powershell commands below: “$payload = [PSCustomObject]@{ embeds […]
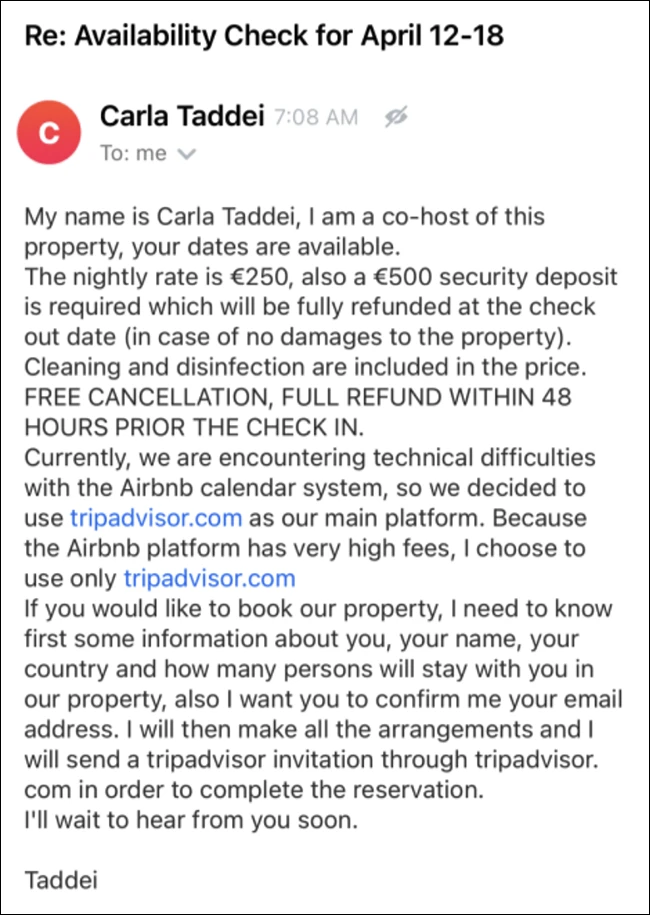
Scammers on Airbnb are faking technical issues and citing higher fees to get users to a spoofed Tripadvisor website and steal their money. The Airbnb scam Malwarebytes researchers came across the Airbnb scam when trying to book an apartment through the platform. The owner/scammer noted in the listing that those interested in booking the property […]
Technical Analysis In this section, we provide a detailed analysis of each component of the attack chain initiated when a victim receives and clicks on the link within the PDF. PDF analysis The PDF file is a fake invitation to a wine-tasting event purported to take place at the Indian ambassador’s residence on February 2nd, […]
Technical Analysis In the following sections, we dive into the technical details surrounding Zloader’s new updates to their anti-analysis techniques, embedded configuration, DGA, and network encryption. Anti-analysis techniques Zloader uses a combination of API import hashing, junk code, a filename check, and string obfuscation. The following sections analyze each technique. Imports and API resolution The […]
Technical Analysis Zscaler ThreatLabz has previously analyzed DreamBus and its modules. Each DreamBus module is an Executable and Linkable Format (ELF) binary that is packed by UPX with a modified header and footer. This alteration is designed to prevent the UPX command-line tool from statically unpacking DreamBus binaries. The magic bytes UPX! (0x21585055) are typically […]
Cybercrime , Fraud Management & Cybercrime , Governance & Risk Management IBM Blames ‘Technical Method’ for Allowing Unauthorized Access to Patient Info Marianne Kolbasuk McGee (HealthInfoSec) • October 17, 2023 IBM said nearly 631,000 individuals are affected by a recent database incident involving Johnson & Johnson’s Janssen CarePath service. (Image: IBM, J&J) IBM […]
Threat actors continued to exploit technical misconfigurations through various fraud schemes, according to a new report from Visa. These include the use of malvertising and search engine optimization (SEO) techniques to cultivate compelling and effective phishing and social engineering campaigns, the utilization of emerging advanced language model (ALM) technologies, and the increased targeting of authentication […]
Two UK police forces have admitted to a data breach caused by a “technical error” that saw the personally identifying information of victims, witnesses and suspects mistakenly posted online following Freedom of Information (FOI) requests. Norfolk and Suffolk police admitted on August 15 that the data of 1,230 people was included in files published to […]