An elite team of Iranian state-sponsored hackers successfully infiltrated hundreds of thousands of employee accounts at US companies and government agencies, according to the Feds, as part of a multiyear cyber espionage campaign aimed at stealing military secrets. The US Departments of Treasury and State are among those compromised in the elaborate campaign, which lasted […]
Recently, the Debian security team fixed several issues in GTKWave, an open-source waveform viewer for VCD (Value Change Dump) files. These vulnerabilities, if exploited, could result in the execution of arbitrary code, posing a significant risk to users. The security updates address a total of 82 identified vulnerabilities. This article details some of the patched […]
Update April 8th, 2024: Updated ETA for CloudLinux 6h and CloudLinux 7. The KernelCare team is working on deploying a live patch for CVE-2024-1086 for CloudLinux users. A patch has already been released for CloudLinux 6h and CloudLinux 7, and users can manually update without a live patch. Instructions for doing so can be found […]
Das Team Ag, a prominent national job placement agency with 25 branches across Switzerland and the Principality of Liechtenstein, confirmed that they fell victim to a cyberattack by the notorious Black Basta ransomware group. The Das Team Ag cyberattack targeted the company’s website and was listed as the victim on the data leak channel operated […]
Created by John Tuckner and the team at workflow and automation platform Tines, the SOC Automation Capability Matrix (SOC ACM) is a set of techniques designed to help security operations teams understand their automation capabilities and respond more effectively to incidents. A customizable, vendor-agnostic tool featuring lists of automation opportunities, it’s been shared and recommended […]
Incident response (IR) is a race against time. You engage your internal or external team because there’s enough evidence that something bad is happening, but you’re still blind to the scope, the impact, and the root cause. The common set of IR tools and practices provides IR teams with the ability to discover malicious files […]
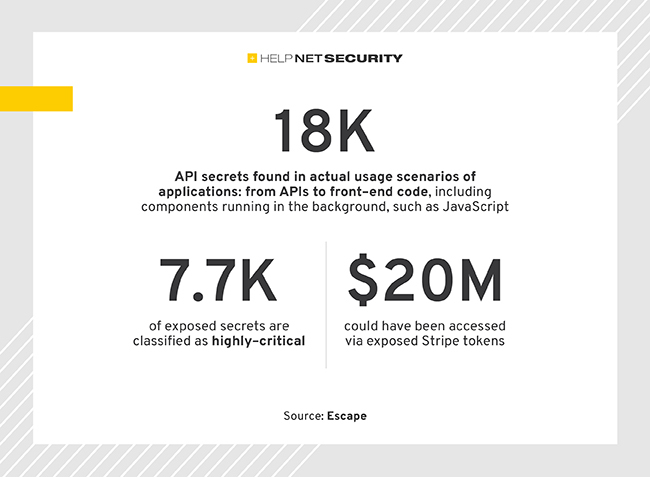
Escape’s security research team scanned 189.5 million URLs and found more than 18,000 exposed API secrets. 41% of exposed secrets were highly critical, i.e. could lead to financial risks for the organizations. Exposed API secrets The exposed secrets include hundreds of Stripe, GitHub/GitLab tokens, RSA private keys, OpenAI keys, AWS tokens, Twitch secret keys, cryptocurrency […]
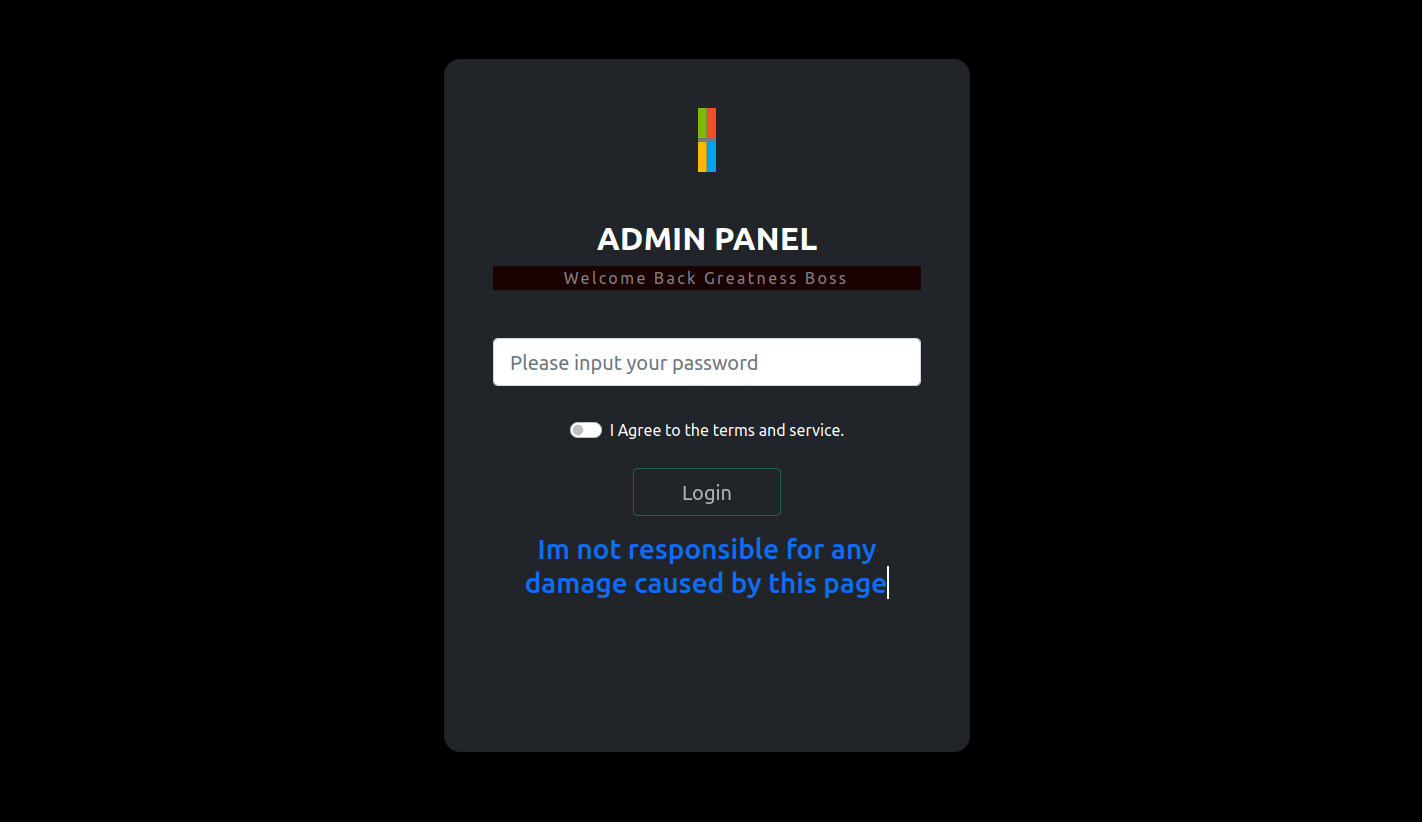
Emerging in 2022, a phishing tool known as Greatness has caught the attention of our research team due to its coordinated efforts to breach Microsoft 365 accounts and presence on compromised websites. More disturbingly, it has shown effectiveness against multi-factor authentication (MFA), elevating the potential threat level. Identified as a Phishing as a Service (PhaaS) […]
Feb 02, 2024NewsroomCryptojacking / Malware The Computer Emergency Response Team of Ukraine (CERT-UA) has warned that more than 2,000 computers in the country have been infected by a strain of malware called DirtyMoe. The agency attributed the campaign to a threat actor it calls UAC-0027. DirtyMoe, active since at least 2016, is capable of carrying […]