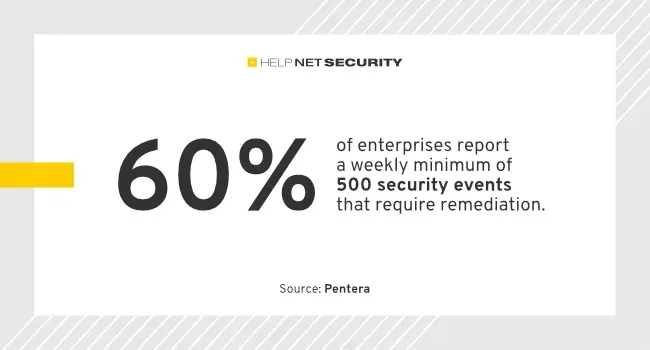
Threat actors are continuing to successfully breach across the entire attack surface and the stakes are only getting higher: 93% of enterprises who admitted a breach reported unplanned downtime, data exposure, or financial loss as a result, according to Pentera. Pentera surveyed 450 CISOs, CIOs, and IT security leaders at enterprise companies with more than […]
Apr 03, 2024The Hacker NewsCybersecurity / Penetration Testing Attack surface management (ASM) and vulnerability management (VM) are often confused, and while they overlap, they’re not the same. The main difference between attack surface management and vulnerability management is in their scope: vulnerability management checks a list of known assets, while attack surface management assumes you […]
Mar 05, 2024NewsroomAttack Surface / Exposure Management Startups and scales-ups are often cloud-first organizations and rarely have sprawling legacy on-prem environments. Likewise, knowing the agility and flexibility that cloud environments provide, the mid-market is predominantly running in a hybrid state, partly in the cloud but with some on-prem assets. While there has been a bit […]
Feb 29, 2024The Hacker NewsAttack Surface / Incident Response As an IT leader, staying on top of the latest cybersecurity developments is essential to keeping your organization safe. But with threats coming from all around — and hackers dreaming up new exploits every day — how do you create proactive, agile cybersecurity strategies? And what […]
Ionix (formerly Cyberpion) helps enterprises reduce their attack surface by giving them a better view of their overall security posture and software supply chain across on-premises, cloud and third-party platforms and services. The company today announced that it has added $15 million to its previously announced $27 million Series A round. The new funding comes […]
IT professionals have developed a sophisticated understanding of the enterprise attack surface – what it is, how to quantify it and how to manage it. The process is simple: begin by thoroughly assessing the attack surface, encompassing the entire IT environment. Identify all potential entry and exit points where unauthorized access could occur. Strengthen these […]
Today’s security leaders must manage a constantly evolving attack surface and a dynamic threat environment due to interconnected devices, cloud services, IoT technologies, and hybrid work environments. Adversaries are constantly introducing new attack techniques, and not all companies have internal Red Teams or unlimited security resources to stay on top of the latest threats. On […]
Stratascale, an SHI company, announced the acquisition of Vector0, an Attack Surface Management (ASM) provider. Through the acquisition, Stratascale professionals and their customers gain visibility of attack vectors and points of vulnerability, enhancing Stratascale’s ability to deliver proactive cybersecurity services. “Vector0 enables us to offer a comprehensive and proactive approach to Attack Surface Validation (ASV), […]