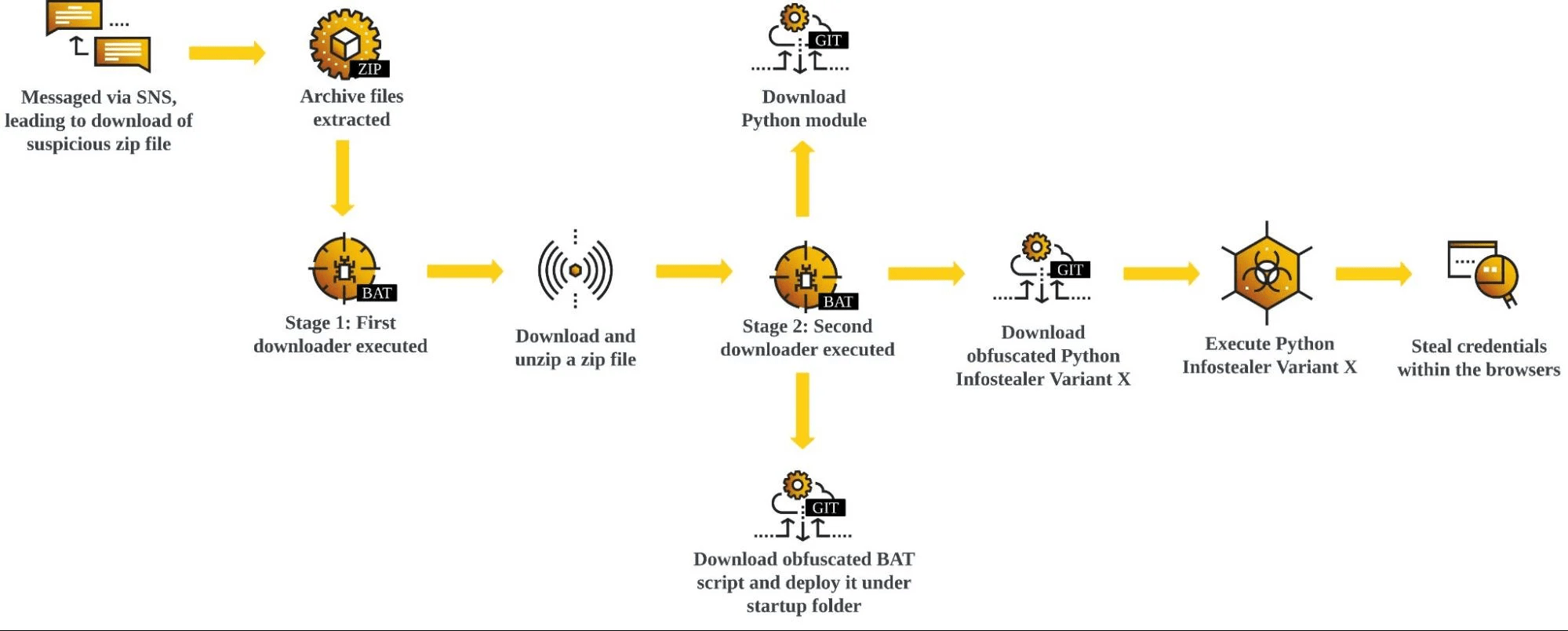
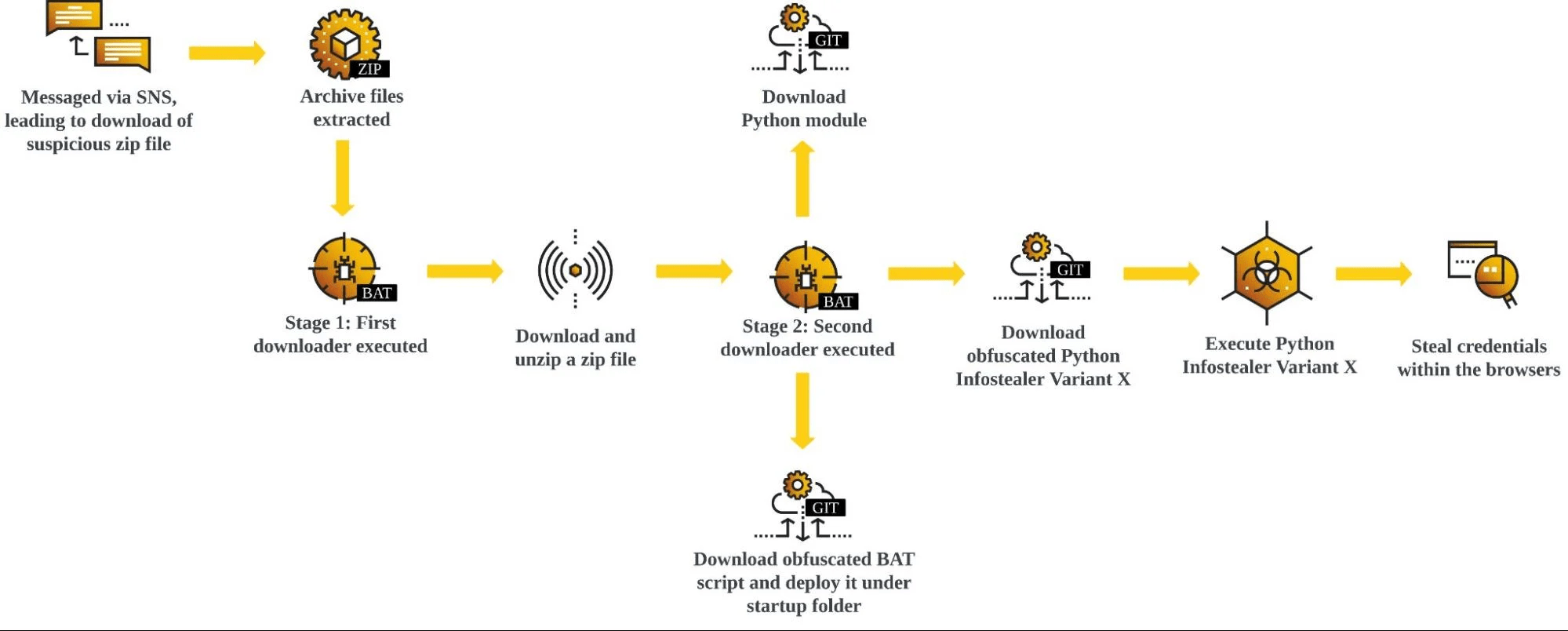
A new information stealer has been found leveraging Lua bytecode for added stealth and sophistication, findings from McAfee Labs reveal. The cybersecurity firm has assessed it to be a variant of a known malware called RedLine Stealer owing to the fact that the command-and-control (C2) server IP address has been previously identified as associated with […]
Mar 30, 2024NewsroomMalware / Cryptocurrency Malicious ads and bogus websites are acting as a conduit to deliver two different stealer malware, including Atomic Stealer, targeting Apple macOS users. The ongoing infostealer attacks targeting macOS users may have adopted different methods to compromise victims’ Macs, but operate with the end goal of stealing sensitive data, Jamf […]
Key takeaways AgentTesla (also known as OriginLogger) remains a prevalent commodity stealer, being daily distributed, mainly via email attachments; The primary method for exfiltrating data remains the usage of mail servers, although Telegram utilization is increasing; Available infection telemetry suggests that the most targeted countries are the United States, China and Germany. Malware as a […]
FortiGuard Labs researchers recently encountered a new Lumma Stealer campaign that leverages YouTube channels for propagation. The attackers are strategically compromising YouTube accounts and uploading videos that pretend to offer cracked software for legitimate video editing tools such as Vegas Pro. Modus operandi According to researchers, these videos contain embedded malicious URLs, enticing users to […]
A threat group is using YouTube channels to distribute a variant of Lumma Stealer, a malware that targets sensitive information, by uploading videos with malicious URLs disguised as cracked software installation guides.
New Version of Meduza Stealer Released in Dark Web Pierluigi Paganini December 29, 2023 The Resecurity’s HUNTER unit spotted a new version of the Meduza stealer (version (2.2)) that was released in the dark web. On Christmas Eve, Resecurity’s HUNTER unit spotted the author of perspective password stealer Meduza has released a new version (2.2). […]
Executive summary In recent developments, a sophisticated malware stealer strain crafted in the Go programming language has been discovered by AT&T Alien Labs, posing a severe threat to both Windows and macOS operating systems. As of the time of publishing of this article, traditional antivirus solutions have low or even non-existent detection rates, making it […]