ESET researchers discovered a cyberespionage campaign that, since at least September 2023, has been victimizing Tibetans through a targeted watering hole (also known as a strategic web compromise), and a supply-chain compromise to deliver trojanized installers of Tibetan language translation software. The attackers aimed to deploy malicious downloaders for Windows and macOS to compromise website […]
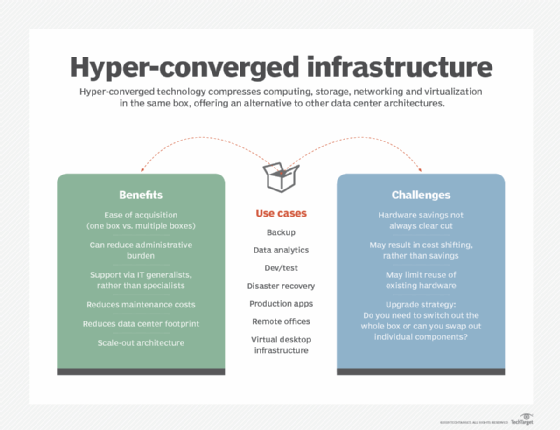
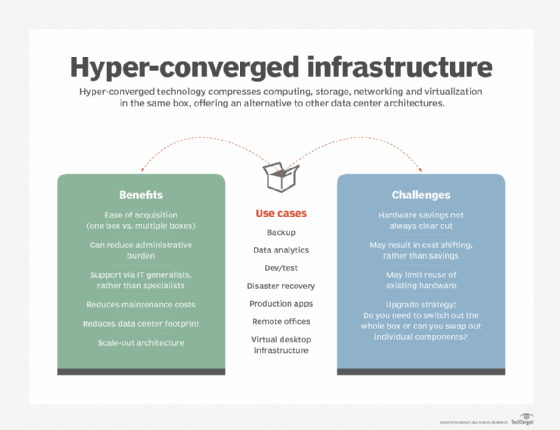
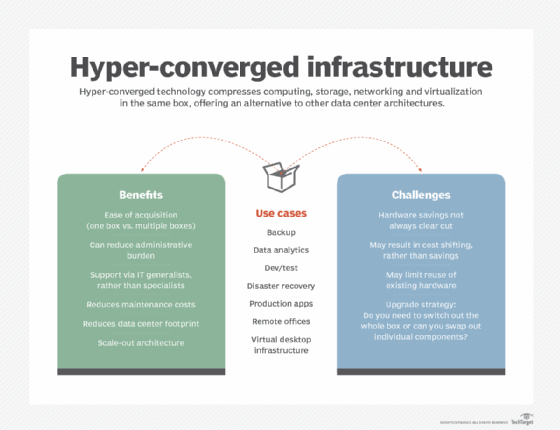
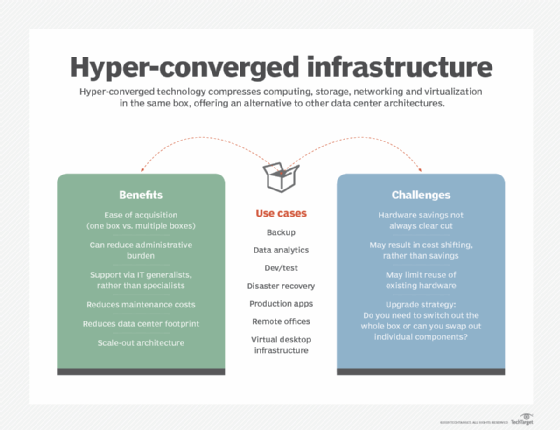
Hyper-converged infrastructure technology has taken big strides since emerging more than a decade ago, finding a home in data centers looking to ease procurement headaches and management chores. Vendors originally positioned the technology as a simple-to-deploy, all-in-one offering that combined compute, storage and networking with a hypervisor. The essential selling points around simplicity remain the […]
Hyper-converged infrastructure technology has taken big strides since emerging more than a decade ago, finding a home in data centers looking to ease procurement headaches and management chores. Vendors originally positioned the technology as a simple-to-deploy, all-in-one offering that combined compute, storage and networking with a hypervisor. The essential selling points around simplicity remain the […]
Hyper-converged infrastructure technology has taken big strides since emerging more than a decade ago, finding a home in data centers looking to ease procurement headaches and management chores. Vendors originally positioned the technology as a simple-to-deploy, all-in-one offering that combined compute, storage and networking with a hypervisor. The essential selling points around simplicity remain the […]
SoundCloud has had a wild ride since it was founded in 2007, and today it was reported by Sky News that the current owners are trying to sell it for one billion dollars. What does this price tag mean? How could it impact DJs and producers who rely on the platform? Could this be a […]
A novel way to abuse a decades-old protocol used to send emails since the beginning of the Internet allows attackers to evade Domain-based Message Authentication, Reporting and Conformance (DMARC) and other email protections, putting organizations and individuals at risk for targeted phishing attacks that appear to come from legitimate sources. Using a technique called “SMTP […]
Kelvin Security has been active since 2013, targeting public-facing systems to obtain user credentials and steal confidential data, which they would sell or leak on hacking forums.
Hyper-converged infrastructure technology has taken big strides since emerging more than a decade ago, finding a home in data centers looking to ease procurement headaches and management chores. Vendors originally positioned the technology as a simple-to-deploy, all-in-one offering that combined compute, storage and networking with a hypervisor. The essential selling points around simplicity remain the […]
Hyper-converged infrastructure technology has taken big strides since emerging more than a decade ago, finding a home in data centers looking to ease procurement headaches and management chores. Vendors originally positioned the technology as a simple-to-deploy, all-in-one offering that combined compute, storage and networking with a hypervisor. The essential selling points around simplicity remain the […]